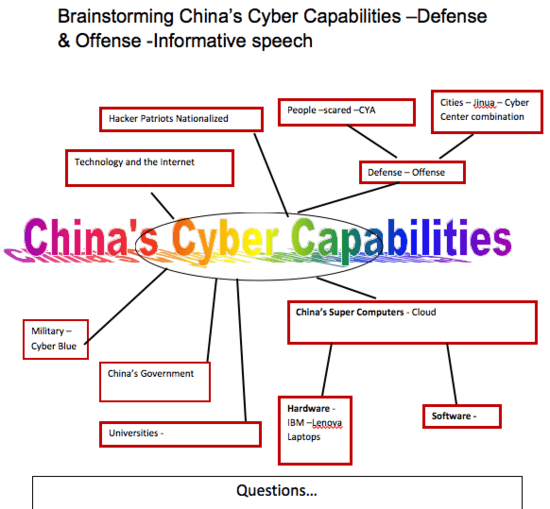
In today’s interconnected world, cyberspace has become the new battleground for global dominance. Nation-states are increasingly leveraging cyber capabilities to conduct espionage, steal intellectual property, and destabilize geopolitical rivals. Among the most notorious actors in this domain are Russia, China, North Korea, and Iran. These countries have been implicated in numerous cyber attacks aimed at…