Today, majority of organizations and many government departments and agencies have shifted their databases onto the cloud to improve efficiency and productivity of resources as well as bring down costs. Unfortunately, this move has exposed sensitive information to hackers, who have frequently launched cyber-attacks to retrieve and misuse data. The major challenge of cloud service providers has been of ensuring security.
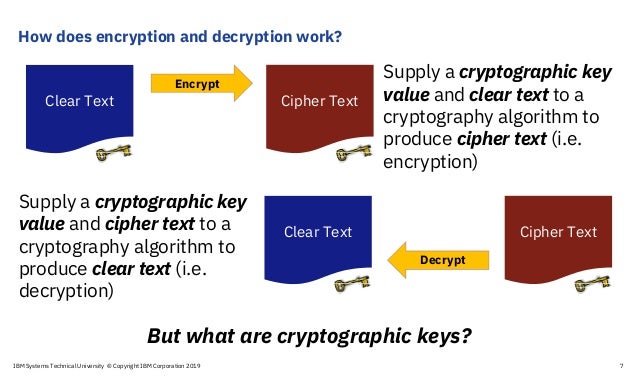
Encryption is a process that uses algorithms to encode data as cyphertext. This cyphertext can only be made meaningful again, if the person or application accessing the data has the tools (encryption keys) to decode the cyphertext. So, if the data is stolen or accidentally shared, it is protected because it is indecipherable.
A recent Ponemon Institute study found that extensive use of encryption is a top factor in reducing the business impact and cost of a data breach, reducing cost on average by $125 per record. According to IBM, only 4% of the more than 9 billion data records lost or stolen since 2013 were encrypted, indicating that most data is vulnerable to cyber attackers.
Every year, more organizations adopt encryption to protect their sensitive data. According to the 2019 Ponemon Institute Global Encryption Trends Study, the percentage of companies with enterprise-wide encryption strategies has tripled in the last 15 years. With regulations like GDPR and the California Consumer Privacy Act providing incentives for companies to encrypt customer data, that trend will likely accelerate in 2020 and beyond.
Encryption types
Organizations considering encryption have many options to choose from, ranging from solutions that protect single hard drives to those that facilitate company-wide protection. One of the most important distinctions to consider is between transparent encryption and persistent encryption. Encryption can be implemented many different ways, some of which leave data vulnerable as it moves from user to user and device to device. Organizations should understand when their encryption software leaves data in the clear (meaning the data is not encrypted) in order to understand their exposure to internal and external cyber threats.
-
- Network encryption provides protection for data as it travels across a network. Data is encrypted while in motion from its origin to its destination, but remains in the clear on either side of the transmission, unless another form of encryption is used.
-
- Transparent encryption provides protection for data at rest. When transparent encryption is applied, the protection is removed before data is accessed, for example when an authorized user copies a file from a file server. This makes the encryption process “transparent” to end users, but also means data exists in the clear any time it is moved or copied from the protected location.The two most common forms of transparent encryption are full disk encryption and file system encryption.
- Full disk encryption protects data at rest by encrypting all data on a hard drive or other storage device. However, this type of encryption only provides protection in the event that the storage device is physically stolen, because data on a drive is decrypted as soon as the device is powered on and accessed by an authorized user.
- Transparent encryption provides protection for data at rest. When transparent encryption is applied, the protection is removed before data is accessed, for example when an authorized user copies a file from a file server. This makes the encryption process “transparent” to end users, but also means data exists in the clear any time it is moved or copied from the protected location.The two most common forms of transparent encryption are full disk encryption and file system encryption.
-
-
- File system encryption protects data at rest in specific locations, usually file or application servers. This method of encryption provides protection against access by outsiders and by unauthorized insiders, because only authorized users or applications can decrypt and access data in the protected locations.
-
-
- Persistent encryption is encryption that travels with data as it is shared, copied, and moved from one system or user to another. Depending on whether the encryption is applied to structured data (fields in a database) or unstructured data (files on servers, laptops, desktops, and mobile devices), persistent data encryption can be categorized as either field level encryption or persistent file encryption.
- Field-level encryption is applied to specific columns or tables within a database. If encrypted data is exported for use in another location, the encryption travels with it, protecting it from inappropriate use. To preserve referential integrity, the length and/or format of protected data can be preserved during encryption.
- Persistent encryption is encryption that travels with data as it is shared, copied, and moved from one system or user to another. Depending on whether the encryption is applied to structured data (fields in a database) or unstructured data (files on servers, laptops, desktops, and mobile devices), persistent data encryption can be categorized as either field level encryption or persistent file encryption.
-
- Persistent file encryption is applied to files on servers, user devices, and other locations, as well as email messages and other forms of unstructured data. Encryption can be applied on a file-by-file basis, or applied to all files within a protected folder. Persistent file encryption remains with files no matter how many times they are copied, shared, or moved, ensuring that only authorized users can access them.
Regulation Compliance
It is becoming increasingly important for organisations to be able to prove that data is protected in the face of regulations like the EU’s General Data Protection Regulation (GDPR) and encryption requirements set for financial institutions by regulators in the Singapore, Hong Kong, and the US at a federal and state level. Encryption is a recommended best practice for almost all compliance and data privacy standards and mandates, including PCI DSS, HIPAA/Hitech, GDPR and many others.
While many data protection regulations—including GDPR, the California Consumer Privacy Act, and New York’s cybersecurity law for financial services companies—recommend the use of encryption, few laws explicitly require it, or prescribe a specific way of using it. For example, the GDPR requirement for security of personal data (Article 32) is to “implement appropriate technical and organisational measures to ensure a level of security appropriate to the risk,” one of which may be encryption. Most other recent data protection laws contain similar language.
While they may not mandate its use, GDPR, the CCPA, and other laws do provide exemptions for companies that use it. The GDPR contains detailed instructions for how and when a company must notify EU citizens after a security breach involving personal data, but companies are exempt from the notification requirements if the stolen data was encrypted, because encrypted data cannot be used by anyone without the right key.
When evaluating their compliance strategies and risks, organizations should consider the distinction between transparent encryption and persistent encryption. If hackers gain access to data protected by transparent encryption and copy it to another location, the encryption will disappear, leaving the data vulnerable to misuse, and leaving the company exposed to fines and other sanctions. Data protected by persistent encryption, however, remains protected even when moved or copied, and is more likely to satisfy regulators and auditors.
Encryption solutions
Transparent Data Encryption (often abbreviated to TDE) is a technology employed by Microsoft, IBM and Oracle to encrypt database files. TDE offers encryption at file level. TDE solves the problem of protecting data at rest, encrypting databases both on the hard drive and consequently on backup media. It does not protect data in transit nor data in use. Enterprises typically employ TDE to solve compliance issues such as PCI DSS which require the protection of data at rest.
Microsoft offers TDE as part of its Microsoft SQL Server 2008, 2008 R2, 2012, 2014, 2016, 2017 and 2019. TDE was only supported on the Evaluation, Developer, Enterprise and Datacenter editions of Microsoft SQL Server, until it was also made available in the Standard edition for 2019. SQL TDE is supported by hardware security modules from Thales e-Security, Townsend Security and SafeNet, Inc. IBM offers TDE as part of Db2 as of version 10.5 fixpack 5. It is also supported in cloud versions of the product by default, Db2 on Cloud and Db2 Warehouse on Cloud.
Oracle requires the Oracle Advanced Security option for Oracle 10g and 11g to enable TDE.[citation needed] Oracle TDE addresses encryption requirements associated with public and private privacy and security mandates such as PCI and California SB 1386. Oracle Advanced Security TDE column encryption was introduced in Oracle Database 10g Release 2. Oracle Advanced Security TDE tablespace encryption and support for hardware security modules (HSMs) were introduced with Oracle Database 11gR1. Keys for TDE can be stored in an HSM to manage keys across servers, protect keys with hardware, and introduce a separation of duties.
Thales Enables Teradata Vantage Customers to Protect Data at Rest With Simplicity, Speed and Scale
Thales in Oct 2020 announced a new high-performance data security solution for Teradata customers using the Vantage platform for data and analytics. By providing users with a totally transparent and scalable encryption solution to protect data at rest in any environment, the Thales Transparent Encryption solutions enable Teradata Vantage customers to better meet compliance and privacy regulations through encryption, access controls and data access audit logging.
Easily deployed across files and systems, this solution enables data at rest to be quickly encrypted within the Vantage platform. Since it is “transparent”, it is simple to deploy because there are no application development or database integration changes required. The cost-effective solution removes data breach risks and supports compliance initiatives while saving organisations months on the deployment of data protection for a Teradata environment.
Thales’ Transparent Encryption is completely invisible to Vantage users and administrators as long as they are authorised to access the databases and system files they won’t know that solution is protecting your business. However, processes and actions from unauthorised users are immediately stopped and logged. The solution can be flexibly deployed across physical, virtual and cloud environments, giving organisations the ability to implement granular access policies that allow administrators to access infrastructure and systems without ever being able to see sensitive data in clear text.
The solution is designed to meet the high-scale and performance requirements of Vantage deployments on-premises, in clouds and hybrid, which can be several hundred terabytes to many petabytes in size and contain highly sensitive and regulated data and subsequently subject to privacy regulations (e.g., GDPR, CCPA, etc.). The scalable solution provides little overhead, from encryption and decryption activities, letting users robustly secure data and retain critical I/O and storage efficiencies.
“We’re pleased to have worked with the Teradata team to expand the Thales offering to include the transparent encryption solutions for Teradata. Our existing joint customers will simply expand their data security platform investment to include their Vantage environment. They will find that the policies for encryption, privileged user access and the additional security intelligence logs to further enhance their visibility are entirely familiar. New customers will be taking their first steps in unifying all their data security requirements and use cases on one easy to use, scalable and high-performance platform. The Thales solution complements the rich set of controls in the Vantage environment, ensuring that deployments meet the toughest regulatory audit scrutiny and protects a company’s most valuable data,” said Todd Moore, Senior Vice President, Encryption Solutions at Thales.
Jay Irwin JD, Director of Teradata Center for Enterprise Securityadded: “Teradata’s customer base is comprised of some of the largest and most data-centric companies on the planet. Security at scale is vital to this clientele, which makes Thales’ solution a particularly good fit for enabling Teradata’s best-in-industry cloud security to be even more robust. With the application of Thales transparent encryption solutions, we provide a layered defense that protects customer data on-premises, in the cloud and in hybrid environments – all deployment types that our customers use today.”
IBM announced breakthrough Z Pervasive Encryption in 2017, a Paradigm Shift in mainframe Security
BM’s mainframes are widely used in the tech industry for delivery of critical services to the government, including large banks, flight booking website, healthcare companies or an ecommerce platform. However, an increasing danger of our connected, digital world is the rise of hackers, and their potential to inflict serious damage with real-world consequences.
What the company has done for the first time ever with the newly released z14 mainframe is to allow Multiple levels of data encryption at every level of the system, and then storing everything inside encrypted containers, designed to hoodwink even the most diligent hackers out there. IBM, which reported revenue of $79.9 billion in 2016, said that its India hardware and firmware team had made significant contributions to the z14 system and microprocessor development.
Encryption is vital to security as only 4% of the more than 9 billion data records lost or stolen since 2013 were encrypted, According to IBM. A recent Ponemon Institute study found that extensive use of encryption is a top factor in reducing the business impact and cost of a data breach, reducing cost on average by $125 per record.
However, Encryption is perceived as complex. Organizations struggle with determining which data should be encrypted, where encryption should occur and who is responsible for it. Therefore many companies only encrypt what’s required for compliance and also at the application layer. This leads to costly implementation and maintenance throughout the application lifecycle because of requirement of highly skilled manpower. As a result, IBM said only about 2% of corporate data is encrypted today, while more than 80% of mobile device data is encrypted.
IBM has introduced Pervasive encryption that provides a transparent and consumable approach to enable extensive encryption of data in flight and at rest to simplify and reduce the costs associated with protecting data and achieving compliance mandates This means it is possible to encrypt data associated with any application, cloud service or data base all the time, which IBM is claiming as a world first.
“The new capabilities being delivered with z14 will allow organizations to encrypt all of the data associated with an application or database, without the need to make any application changes and without impacting service level agreements,” says Sardino. “No other platform in the world can do this.”
“Strong walls and perimeter defenses are no longer adequate to shield organizations from cyberattacks. We must view data as the new perimeter, and put the security controls for the data on the data itself,” says Nick Sardino, program director, IBM Z Offering Management. “That means implementing strong encryption of data wherever it resides.”
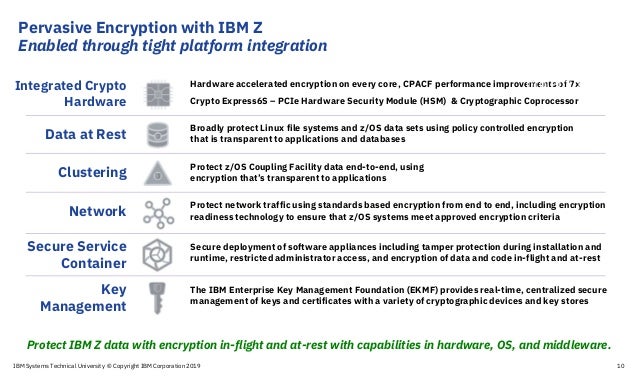
To achieve this new standard for encryption, IBM Z delivered several new capabilities integrated throughout the z14 stack in the hardware, OS and middleware. The on-chip cryptographic acceleration was enhanced to provide more than 6x more performance than z13 at more than 18x faster than competitive platforms, according to a Solitaire Interglobal report. Bulk file and data set encryption was placed at a point in the OS where the encryption would be transparent to applications and highly optimized for performance. IBM also designed new capabilities to encrypt the data in the z/OS Coupling Facility, and more easily report on the security of z/OS network sessions.
Another concern for users is the protection of encryption keys. In large firms, hackers often target encryption keys, which are routinely exposed in memory as they are used, the company said. It said IBM Z can protect millions of keys, as well as the process of accessing, generating and recycling them. It does this in ‘tamper responding’ hardware that causes keys to self-destruct at any sign of intrusion and they can then be reconstituted in safety.
BM middleware such as Db2 and IMS was enhanced to exploit these new features as well. “Clients can transition Db2 and IMS high availability databases from unencrypted to encrypted without stopping the database or the application,” says Sardino, “which is a huge value for the DBAs that we’ve spoken to.”
BM Security also enhanced the IBM Security zSecure suite to provide administration and audit support for pervasive encryption. The system also provides an audit trail showing if and when permissioned insiders accessed data. When organizations can quickly and easily demonstrate to auditors all of their data is encrypted, the cost and complexity are significantly reduced.
The suite can feed data into a newly designed QRadar dashboard for auditors. Other IBM Security solutions such as IBM Security Guardium Data Encryption for Db2 and IMS Databases and IBM Security Guardium Data Activity Monitor can be layered on top of pervasive encryption for additional levels of data protection.
Although there is a small chance that determined attackers will find a way of breaking the 256-bit AES encryption to access the stolen data, security commentators say that if the technology lives up to IBM’s claims, it could be a big step forward in terms of data protection. IBM Z is the only platform that offers the protection of pervasive encryption. This no-compromise approach to data protection is at the core of trusted digital experiences. With pervasive encryption you can rest easy knowing your data is secure.
References and Resources also include:
http://ibmsystemsmag.com/mainframe/trends/ibm-announcements/pervasive-encryption/
http://www.computerweekly.com/news/450422750/IBM-claims-breakthrough-in-mainframe-encryption
 International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis