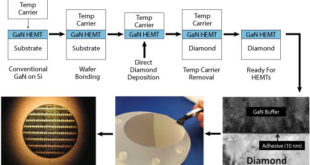
Gallium nitride (GaN) is hot. Even hotter is a race to integrate GaN with other materials to boost GaN’s performance further. The power electronics industry has seen the theoretical performance limit reached by silicon MOSFETs and now needs to move to a new element. GaN is a wide bandgap, …
Read More »Recent Posts
With Space a Warfighting domain, Countries plan military space strategy and space commands for deterrence , space control , and space protection
As the space domain has become more congested, the potential for intentional and unintentional threats to space system assets has increased. Space is also becoming another domain of conflict due to enhanced militarization and weaponization of space. There has been enhanced testing of Anti-satellite weapons (ASAT) and space weapons designed …
Read More »Nuclear Risk has increased because of Emerging technologies
Although nuclear weapons have not been used in conflict for decades, the risk of their use persists. Around the world, countries are still building and modernizing nuclear arsenals. Russia, US and China are rapidly upgrading and modernizing their strategic triad. The potential use of nuclear weapons poses the greatest danger …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis