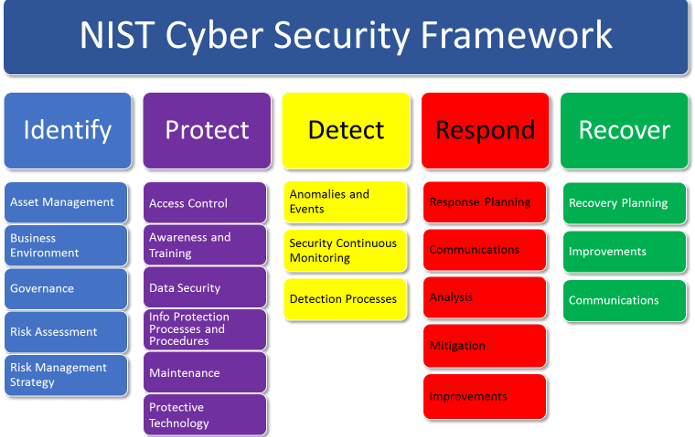
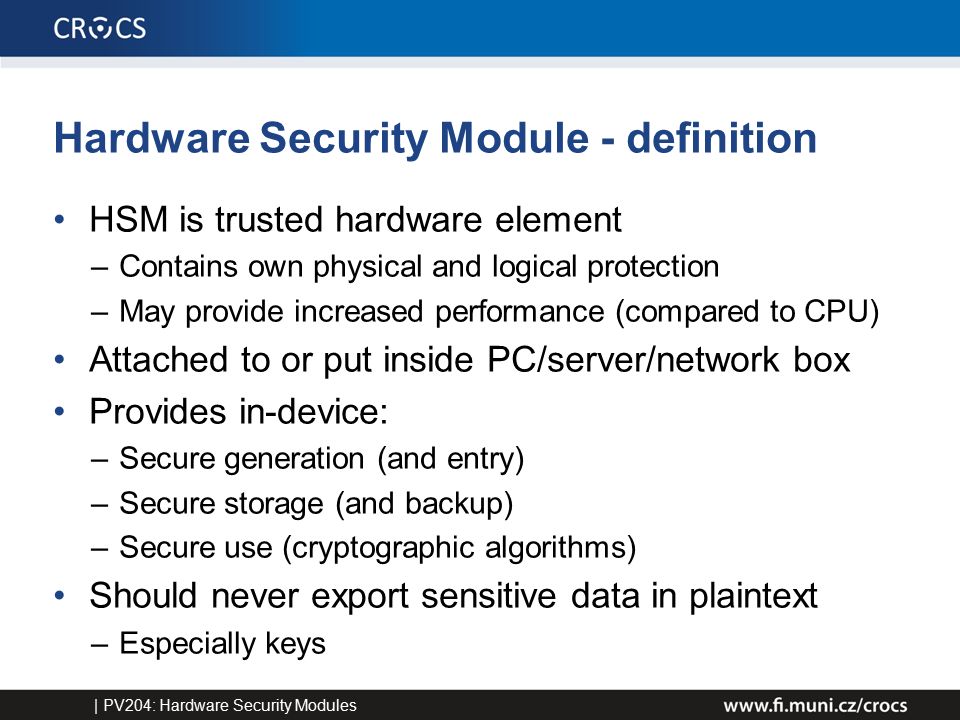
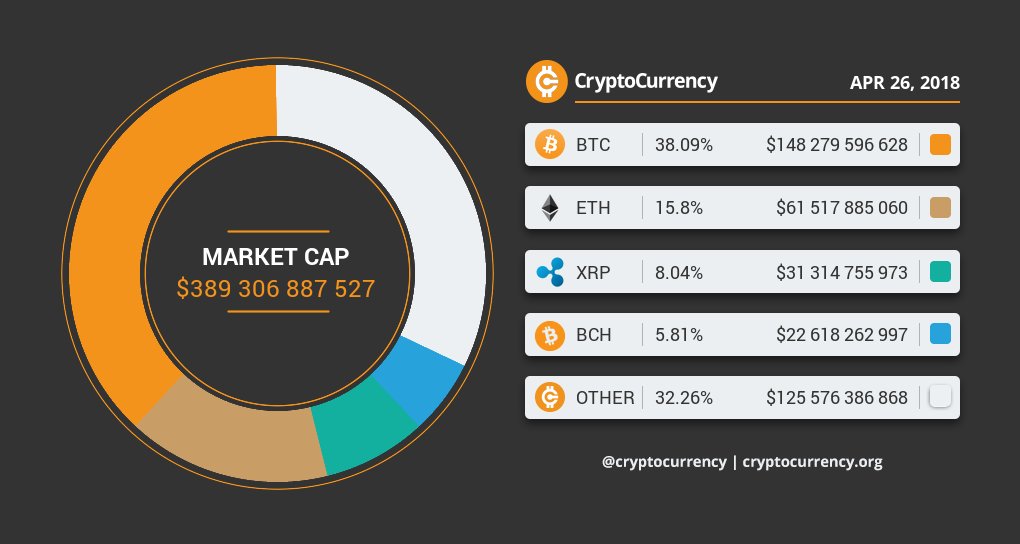
DARPA’s SHIELD developed technologies for secure reliable authentication for ICs subject to hardware Trojans, cloning, counterfeit or recycling in Military systems that pose critical National Security Risk

Outsourcing of integrated circuit (IC) and printed circuit board (PCB) design, fabrication, packaging, and testing have dramatically reduced the time and cost of product development. In doing so, this has enabled the widespread availability of microelectronics, which has indeed transformed…