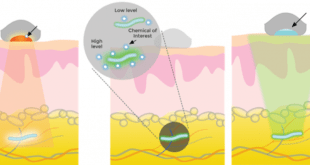
Biosensors, that is sensors that can detect parameters in a living being, are becoming more and more effective in several respects: detecting more and more parameters, becoming more and more sensitive, being able to co-exist for long period of time with the hosting organism to the point of becoming an …
Read More »Ramjet Powered Artillery Round can penetrate anti-access/area denial networks
One of the major lessons from Ukraine’s artillery war is that the side that can shoot farthest dominates the battlefield. According to the report, Russian howitzers are expending 20,000 shells daily on average, compared to 6,000 fired by Ukraine. The ratio for rocket artillery and ballistic-missile launches is even worse. …
Read More »Emerging Unmanned Underwater Vehicle(UUV) threat
Drones have become an essential platform for any military and they have changed the shape of recent conflicts. Their slow speed and small radar cross-section have created a lot of challenges for conventional sensors and weapons to detect and engage them. Many technologies have been developed for their detection and …
Read More »Biomedical Informatics and Computational biology technologies require Supercomputers for projects like Covid-19 and Military
Computational biology is a branch of biology that aims to better understand and model biological structures and processes by utilizing computers and computer science. It entails the application of computer methods (such as algorithms) to the representation and simulation of biological systems and the large-scale analysis of experimental data. …
Read More »US Navy “Distributed Maritime Operations (DMO),” strategy integrating diverse autonomous unmanned vehicles UUV, USVs, UAVs
The US Navy published a navigation plan to boost the war vessels to 500 by 2045 in the region citing “both a current and long-term challenge.” Reiterating that China is the central threat to the US Navy’s maritime dominance, the report says: “This is a critical decade. As global challengers …
Read More »Aligning Marketing Strategy with Sales Strategy
Your Sales and Marketing strategy is your plan for reaching, engaging, and converting target prospects into profitable customers. A marketing strategy is how you will reach your target audience, while a sales strategy is how you will convert them to customers. A marketing strategy sets the direction for how you will …
Read More »DARPA’s NOMARS developing long endurance Autonomous warship for surveillance, targeting, electronic warfare and strike warfare
In 2018, China surpassed the U.S. Navy as the world’s largest naval force. China has now launched a new “world-leading unmanned warship” that is supposedly ready for combat, Chinese media reports. The JARI multi-purpose unmanned combat vessel, a new product of the state-owned China Shipbuilding Industry Corporation, is 50 feet …
Read More »Aircraft propulsion system Market driven by demand for air travel and cargo, aircraft deliveries, and fuel efficiency
All Aircrafts depend on propulsion system is to produce thrust so as to lift the object for a prolonged period of time by consuming different fuels. Presently jet engines are the workhorses of airplanes carrying millions of people, trillions of miles every year, at supersonic speed and with high safety; …
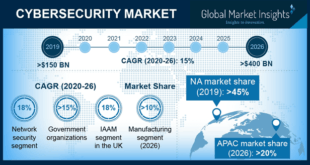
Read More »Cyber Warfare threat driving Defense Cyber Security market and new security technologies
In 2019, 1,473 data breaches in the U.S. led to the exposure of 164,683,455 confidential records, as per the Identity Theft Resource Center (ITRC). Additionally, in May 2020 alone, 841,529 records were exposed in 108 data breach incidents. The records ranged from people’s financial and medical information to strongly protected …
Read More »Mine Countermeasures (MCM) technologies for Anti-Submarine Warfare (ASW) , Surface Warfare (SUW) , and counter terrorism missions
Sea mines are one of the cheapest and most dangerous threats for naval forces; a reality experienced in both World Wars and the Korean War. In order to mitigate the impacts and risks of sea mines on naval operations, advanced navies have been increasing their investments in autonomous Mine Countermeasure …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis