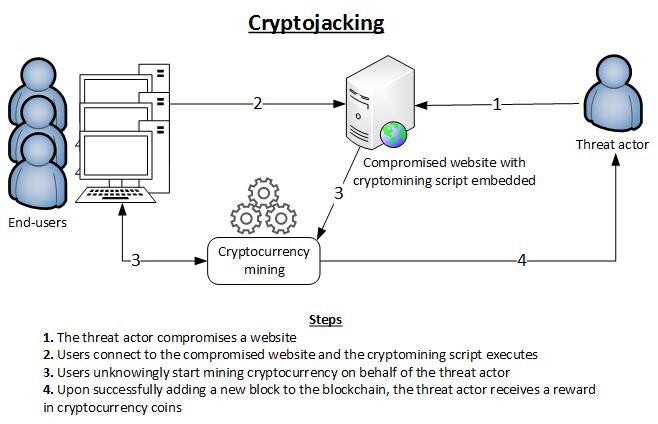
Cyber criminals are switching away from ransomware to stealthier attacks as the main sources of generating revenue, according to analysis by British artificial intelligence (AI)-based cyber security firm Darktrace. Cryptojacking is the unauthorized use of someone else’s computer to mine cryptocurrency. Cryptocurrency is a form of digital currency that can be used in exchange for goods, services, and even real money. Users can “mine” it on their computer by using special programs to solve complex, encrypted math equations in order to gain a piece of the currency.
Coin mining on your own can be a long, costly endeavor. Elevated electricity bills and expensive computer equipment are major investments and key challenges to coin mining. The more devices you have working for you, the faster you can “mine” coins. Because of the time and resources that go into coin mining, cryptojacking is attractive to cybercriminals. In a sense, cryptojacking is a way for cybercriminals to make free money with minimal effort. Cybercriminals can simply hijack someone else’s machine with just a few lines of code.
This leaves the victim bearing the cost of the computations and electricity that are necessary to mine cryptocurrency. The criminals get away with the tokens. Hackers do this by either getting the victim to click on a malicious link in an email that loads crypto mining code on the computer, or by infecting a website or online ad with JavaScript code that auto-executes once loaded in the victim’s browser.
Either way, the crypto mining code then works in the background as unsuspecting victims use their computers normally. Whichever method is used, the code runs complex mathematical problems on the victims’ computers and sends the results to a server that the hacker controls. The only sign they might notice is slower performance or lags in execution.
The Ukranian cyber police say that they have arrested an unnamed person who infected numerous of his websites with malware such as ‘Wannacry.’ He infected his own websites by putting crypto mining malware scripts into it; local law enforcement of Ukraine reported the matter on March 2019. An unnamed 32-year-old man has been caught by the cyber-crime unit of the Ukraine national police from the region of Bukovina who, apparently, put cryptojacking software over a number of educational websites which were developed and administered by him. The unidentified websites and the internet resources were visited by around 1.5 million users every month, the cyber-crime police mentioned.
Cryptojacking malware and ransomware activities have increased rapidly, the cybersecurity firm McAfee Labs revealed in the month of December 2018 , that the overall occurrences of cryptojacking malware grew by more than 4,000 percent in the year 2018.
Rise in Stelathier attacks including Crptojacking
The firm’s latest cyber threat landscape report is based on analysis of threats recorded from a customer base of more than 7,000 deployments. The data reveals that the incidence of banking Trojans, which harvest the credentials of online banking customers from infected machines, increased by a staggering 239% in 2018 compared with 2017. Darktrace also detected a 78% growth in the frequency of another under-the-radar threat, cryptojacking, within the same time period.
This February, Bad Packets Report found 34,474 sites running Coinhive, the most popular JavaScript miner that is also used for legitimate crypto mining activity. In July, Check Point Software Technologies reported that four of the top ten malware it has found are crypto miners, including the top two: Coinhive and Cryptoloot.
While ransomware attacks are highly visible and require the cooperation of the targeted firms in paying to decrypt their data encrypted by the ransomware, cryptojacking is designed to remain hidden. The crypto mining code runs surreptitiously and can go undetected for a long time. Once discovered, it’s very hard to trace back to the source, and the victims have little incentive to do so since nothing was stolen or encrypted. Hackers tend to prefer anonymous cryptocurrencies like Monero and Zcash over the more popular Bitcoin because it is harder to track the illegal activity back to them
Cryptojacking doesn’t even require significant technical skills. According to the report, The New Gold Rush Cryptocurrencies Are the New Frontier of Fraud, from Digital Shadows, cryptojacking kits are available on the dark web for as little as $30.
Bad Packets Report found 34,474 sites running Coinhive, the most popular JavaScript miner that is also used for legitimate crypto mining activity. In July, Check Point Software Technologies reported that four of the top ten malware it has found are crypto miners, including the top two: Coinhive and Cryptoloot.
“Crypto mining is in its infancy. There’s a lot of room for growth and evolution,” says Marc Laliberte, threat analyst at network security solutions provider WatchGuard Technologies. He notes that Coinhive is easy to deploy and generated $300 thousand in its first month. “It’s grown quite a bit since then. It’s really easy money.”
Countering Cryptojacking threat
Crypto mining code can hide from signature-based detection tools,” says Laliberte. “Desktop antivirus tools won’t see them.” Cryptojacking can be detected by noting High processor usage on your device, Sluggish or unusually slow response times and Overheating of your device. Cryptojacking is easy to detect via network monitoring solutions, and most corporate organizations have network monitoring tools.
In addition to using security software and educating yourself on cryptojacking, you can also install ad-blocking or anti-cryptomining extensions on web browsers for an extra layer of protection. Laliberte recommends extensions like No Coin and MinerBlock, which are designed to detect and block cryptomining scripts.
For in-browser JavaScript attacks, the solution is simple once cryptomining is detected: Kill the browser tab running the script. IT should note the website URL that’s the source of the script and update the company’s web filters to block it. Consider deploying anti-crypto mining tools to help prevent future attacks.
As always, be sure to remain wary of phishing emails, unknown attachments, and dubious links.
Using Machine learning
With hackers adopting stealthier techniques, security teams need to find a way of gaining visibility and control of their corporate networks.”
As an AI-based cyber security firm, Darktrace claims that to overcome these fundamental limitations, security teams must be willing to rethink their security tactics and use AI technology to battle against machine-speed attacks. This report details seven case studies of attacks in which Darktrace claims that the subtle indicators of suspicious activity were only detectable using AI technology, which learns what is normal for the business environment and autonomously responds to attacks before damage is done
Created by mathematicians, Darktrace’s Enterprise Immune System uses machine learning and AI algorithms to detect and respond to cyber threats across diverse digital environments, including cloud and virtualised networks, IoT and industrial control systems.
The company claims that its technology is self-learning and requires no setup, identifying threats in real time, including zero-days, insider threats and stealthy, silent attackers.
These attacks will only increase with time as everything is going digital and we have to learn and evolve from them.
Stay abreast of crypto jacking trends. Delivery methods and the crypto-mining code itself are constantly evolving. Understanding the software and behaviors can help you detect crypto jacking, says Travis Farral, director of security strategy at Anomali. “A savvy organization is going to stay abreast of what’s happening. If you understand the delivery mechanisms for these types of things, you know this particular exploit kit is delivering crypto stuff. Protections against the exploit kit will be protections against being infected by the cryptomining malware,” he says.
References and Resources also include:
https://us.norton.com/internetsecurity-malware-what-is-cryptojacking.html