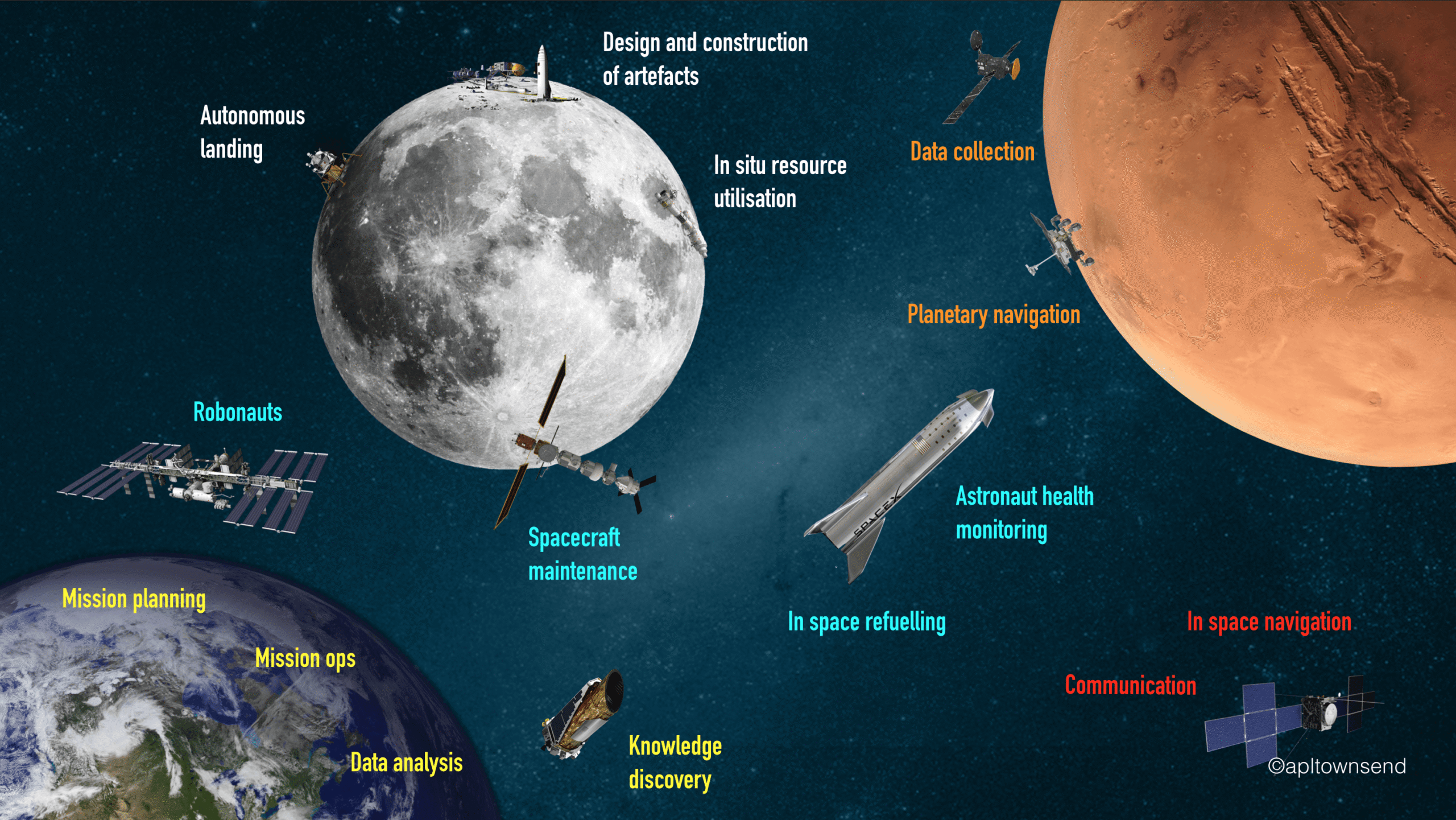
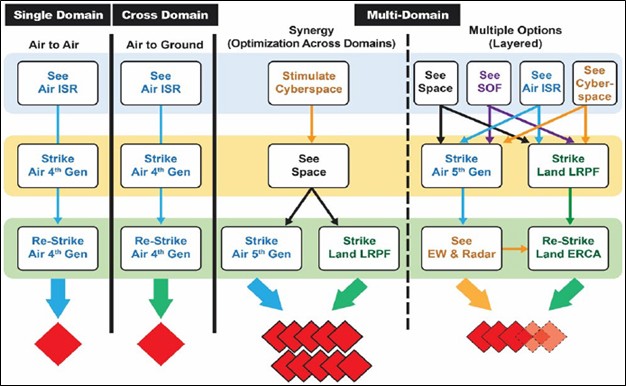
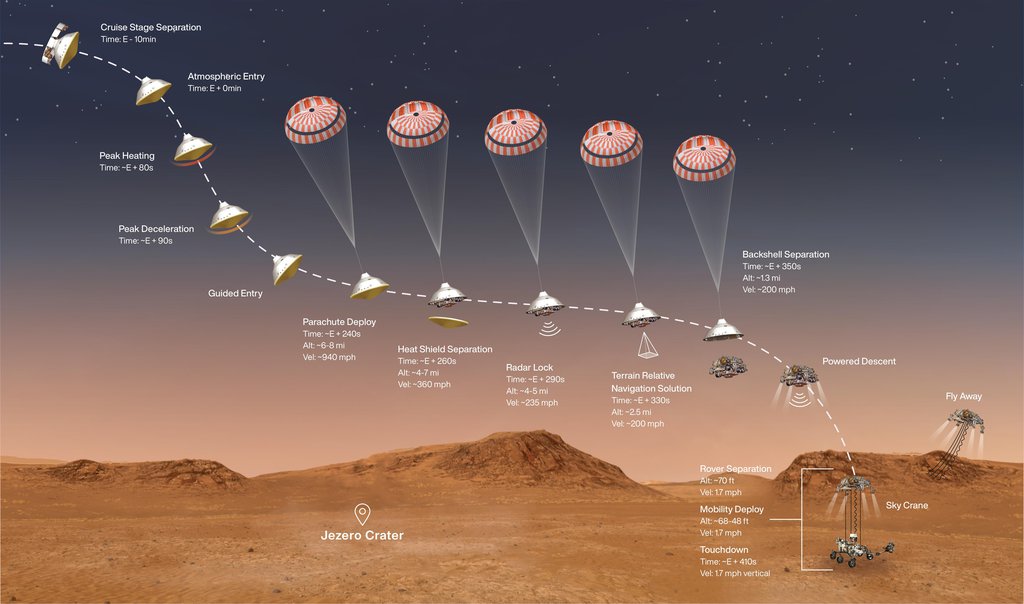
With Space a Warfighting domain, Countries plan military space strategy and space commands for deterrence , space control , and space protection

As the space domain has become more congested, the potential for intentional and unintentional threats to space system assets has increased. Space is also becoming another domain of conflict due to enhanced militarization and weaponization of space. There has been…