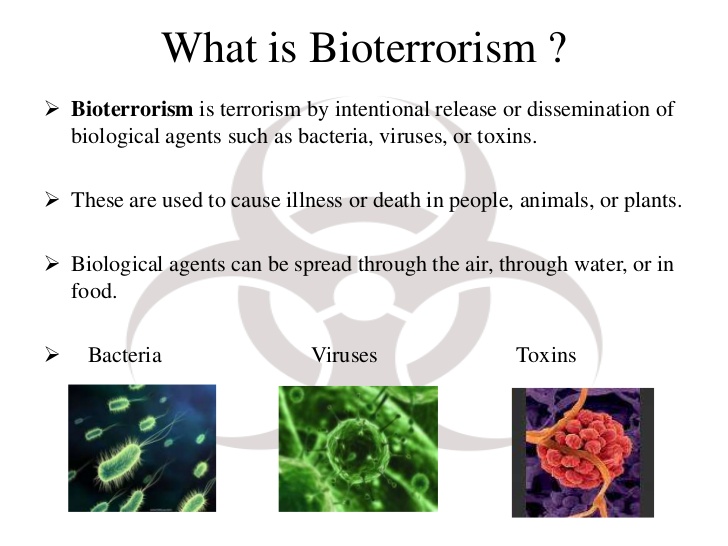
Remerging threat of Biological Weapons attack against Agricultural Targets and Agrobioterrorism, with advances in Gene editing, synthetic biology, and improved delivery systems

Food and agriculture are key elements of the critical infrastructure of every country because they provide products that are essential for life. The United States is a country with a highly developed agricultural sector. Food and agriculture constitute a sixth…...