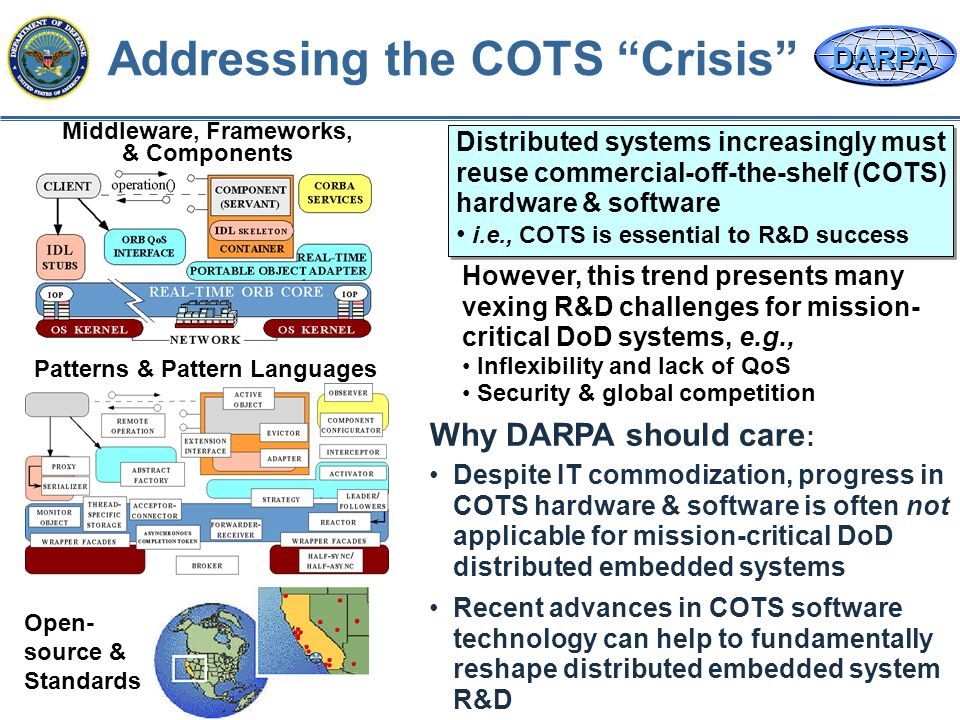
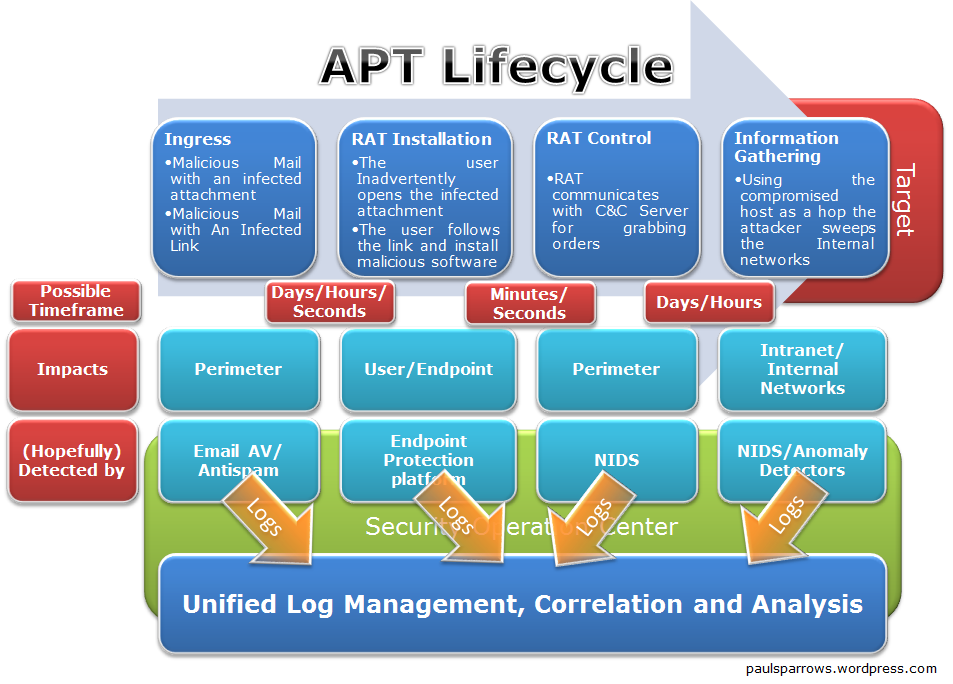
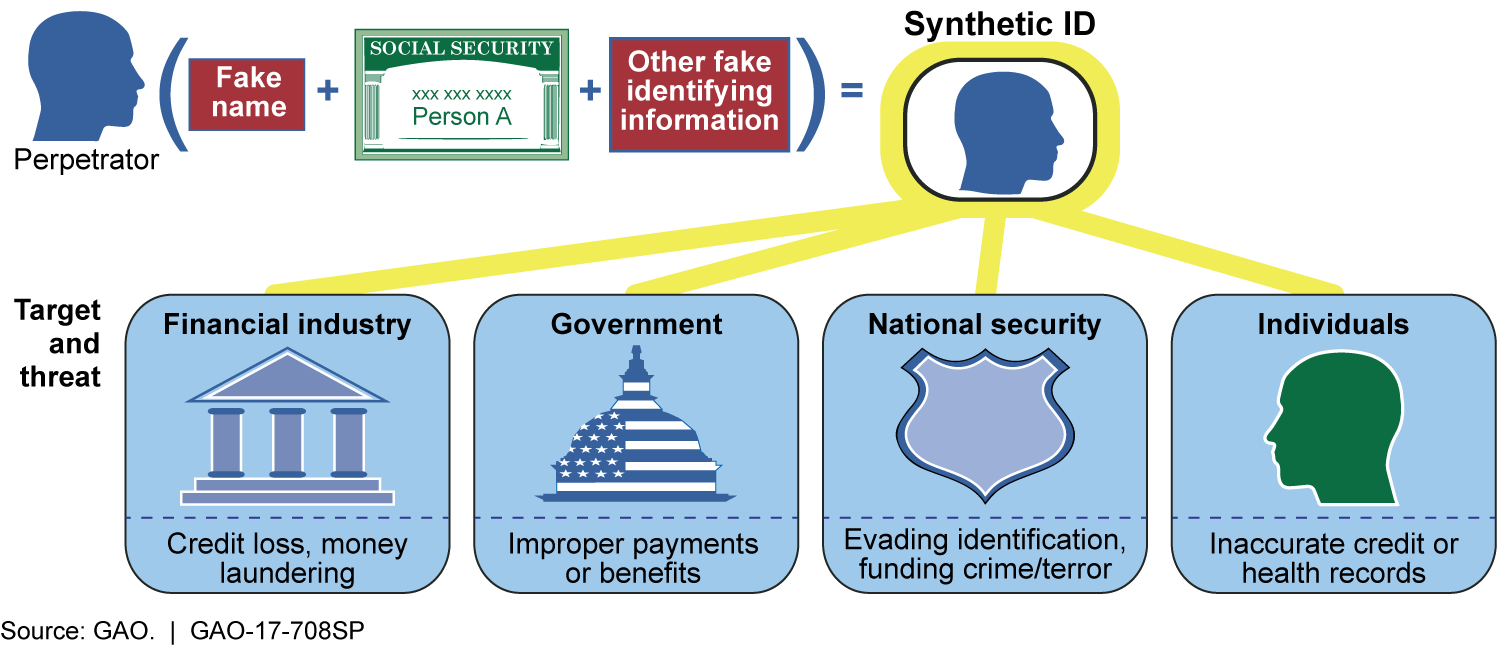
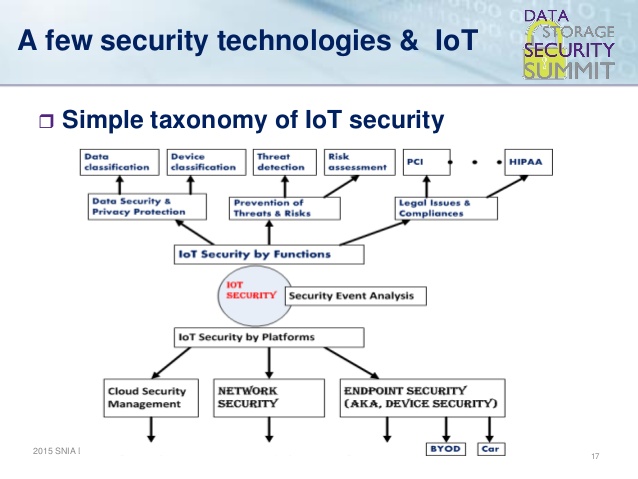
With rising threat of mobile malware, Mobile companies are launching secure smartphones

The recent rise in mobile malware have made Mobile phones vulnerable to data leakage and tempering of sensitive information such as business documents, bank details, credit card information and make purchases. Malware client called Pegasus have been found that can jailbreak…...