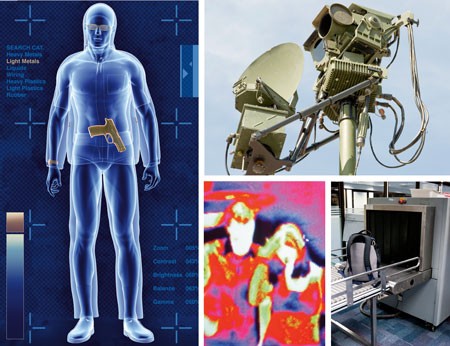
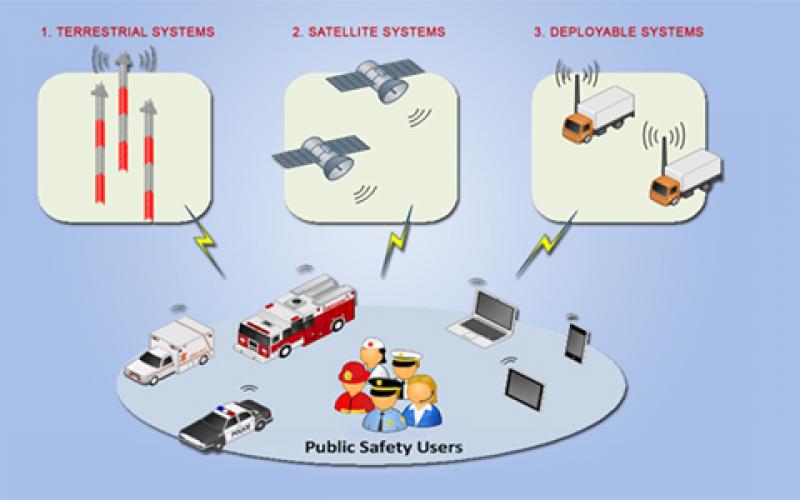
Next Robot revolution is achieving Human-Like dexterous manipulation for home, Industry and Security
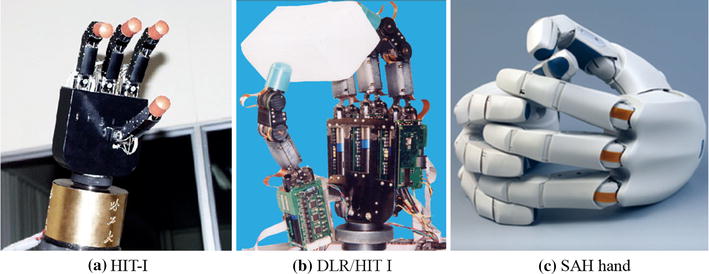
Robots have already become an indispensable part of our lives. However currently, most robots are relatively rigid machines which make unnatural movements. In contrast, humans seem to be able to manipulate objects with our fingers with incredible ease like sifting…...