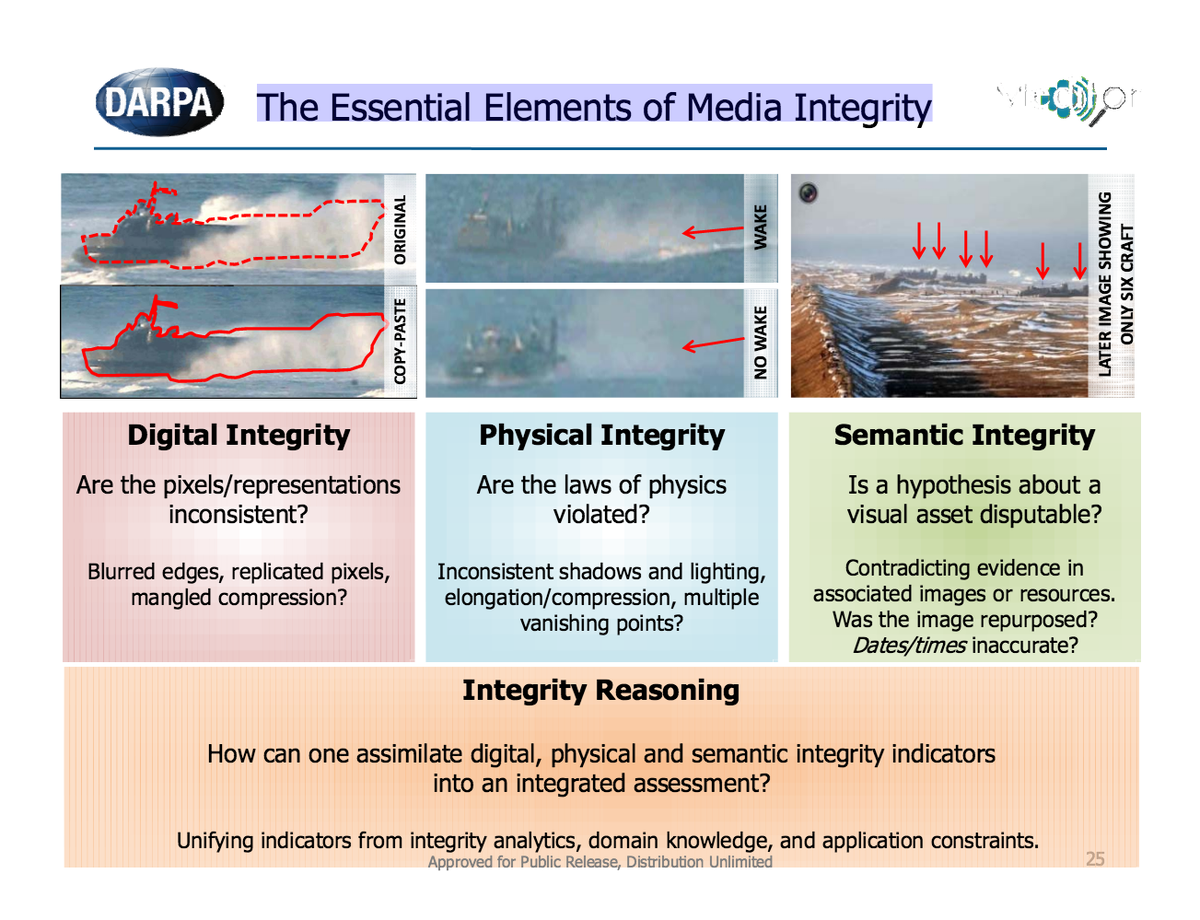
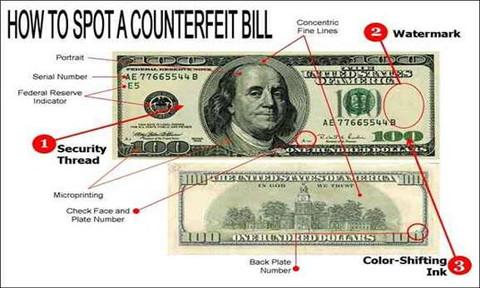
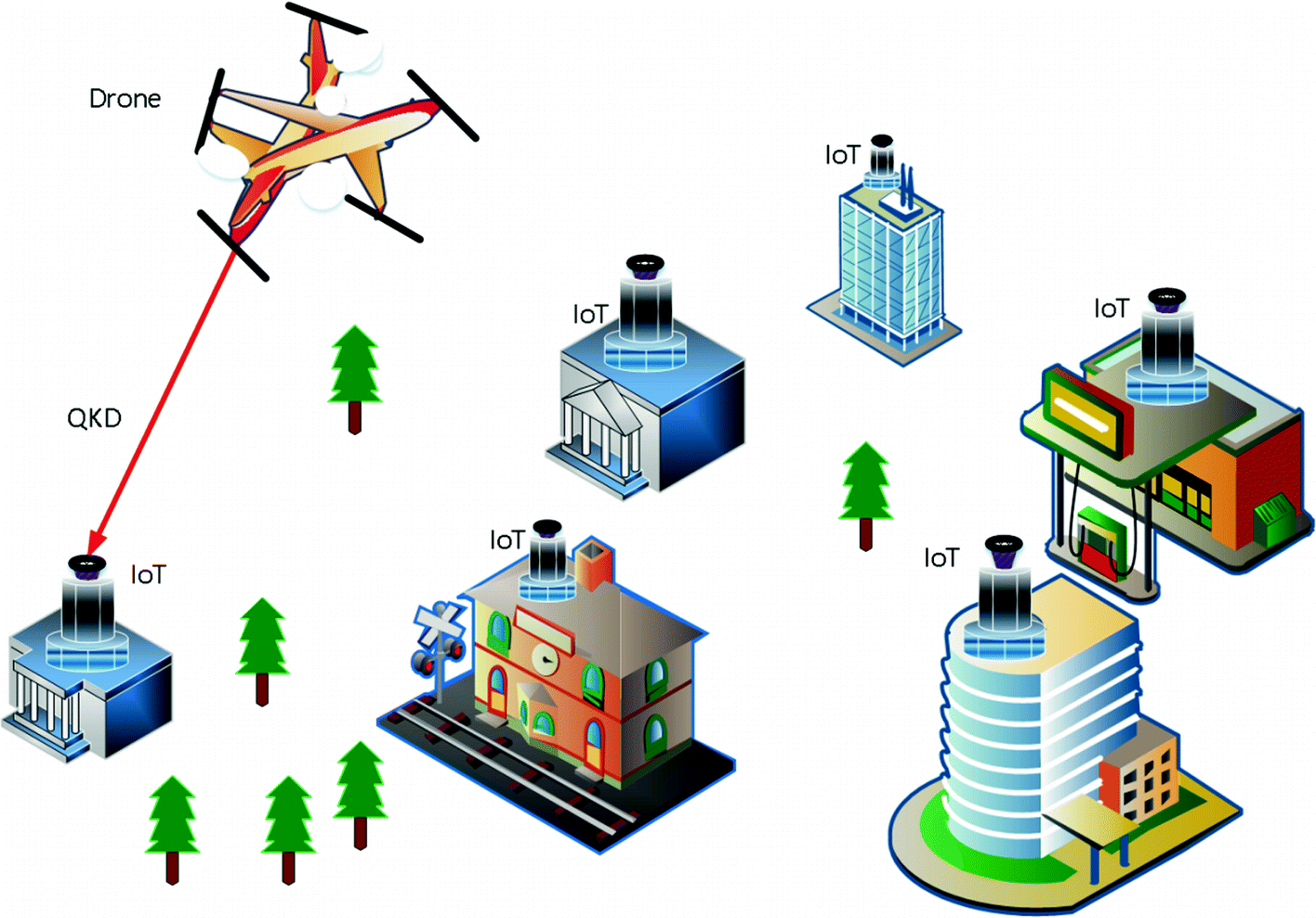
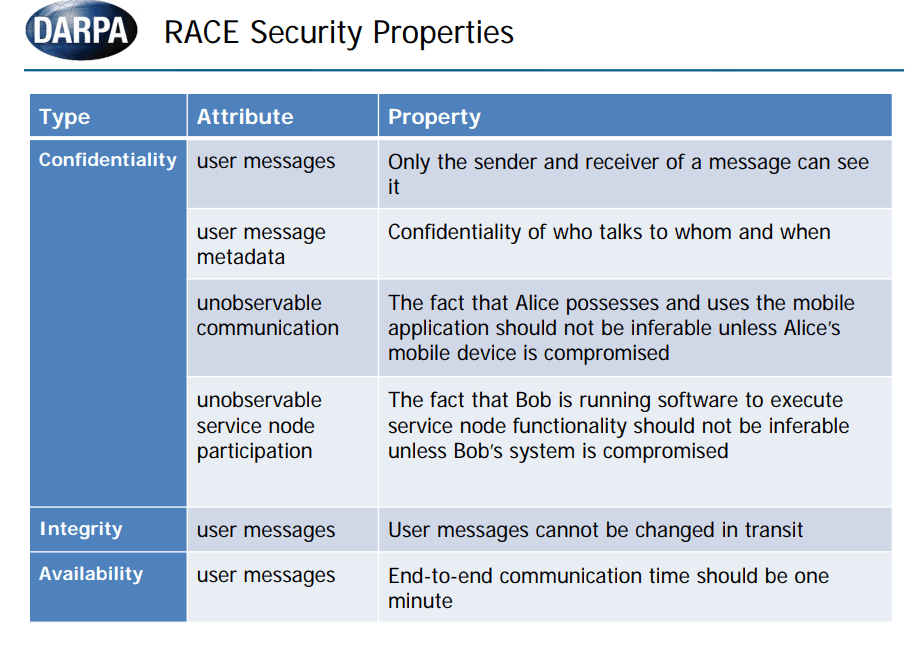
Border Agents can fight the Threat of Drug trafficking networks by portable Drug Detection Devices that can identify drugs within seconds

Criminal networks traffic a range of drugs including cannabis, cocaine, heroin and methamphetamine. As international borders become increasingly porous, global abuse and accessibility to drugs have become increasingly widespread. This international trade involves growers, producers, couriers, suppliers and dealers.…...