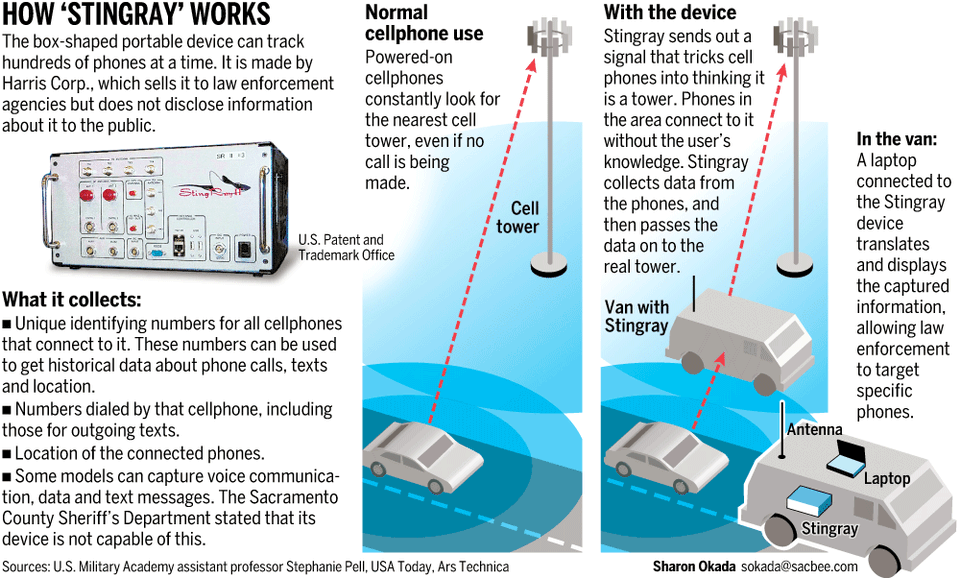
Smartphones increasingly vulnerable from hacking and spying through malware attacks, holes in hardware, Geolocation devices and cameras

Today, mobile devices are coming under increasing attack. The number of mobile malware is rapidly on the rise with malicious activities, such as stealing users data, sending premium messages and making phone call to premium numbers that users have…...