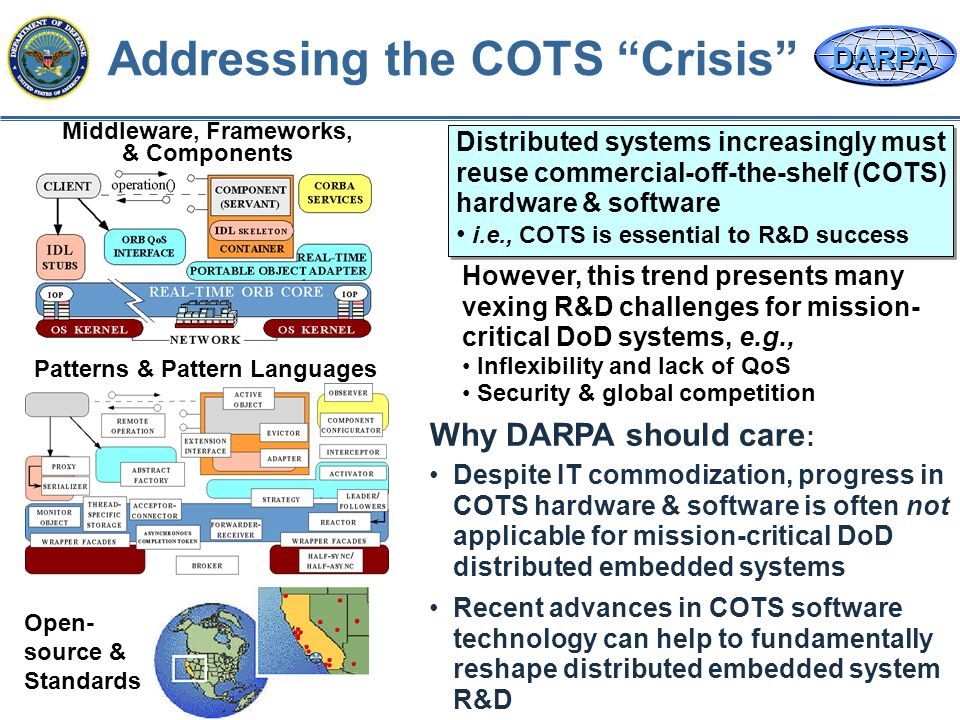
Militaries employ ‘The mother of all bombs’ or MOABs for wiping out fortified ground targets and creating ‘shock and awe’
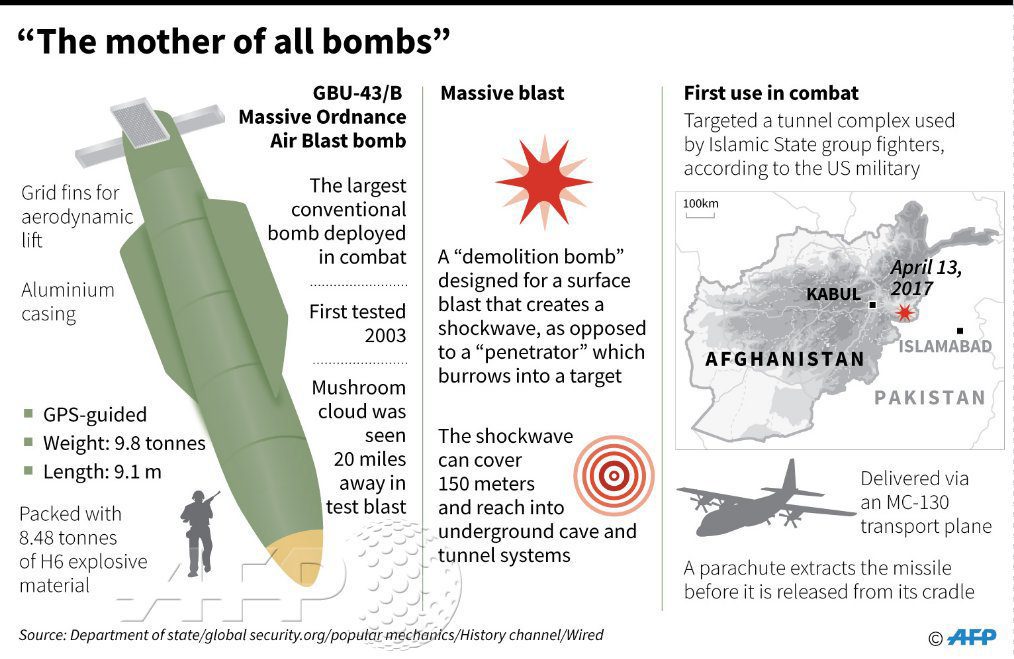
The US’s GBU-43/B Massive Ordnance Air Blast (MOAB) is a precision-guided munition weighing 21,500 pounds and was dropped from a C-130 Hercules aircraft. The MOAB isn’t the heaviest non-nuclear bomb in the US arsenal (that’s the 30,000-pound Massive Ordinance Penetrator…...