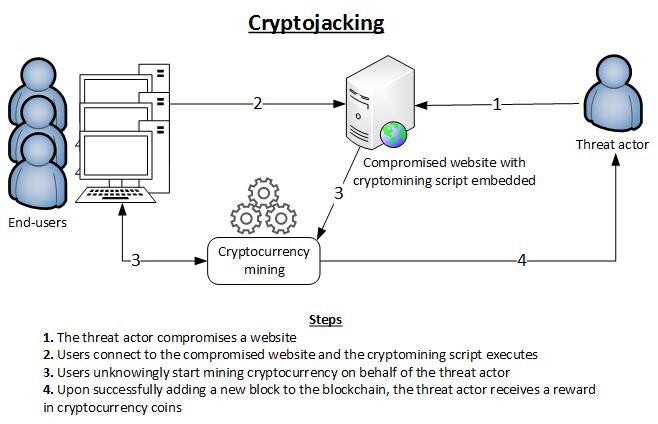
New counter-terrorism training technologies prepare security forces for every possible terror scenario

Today’s terrorist landscape is more fluid and complex than ever and the threat landscape is less predictable. The United States and our allies face an increasingly complex terrorist landscape, populated by a diverse array of actors employing new technologies and…...