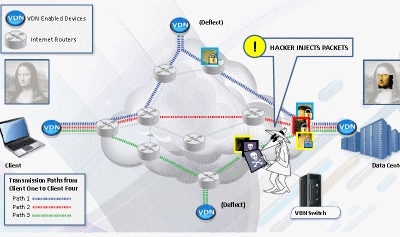
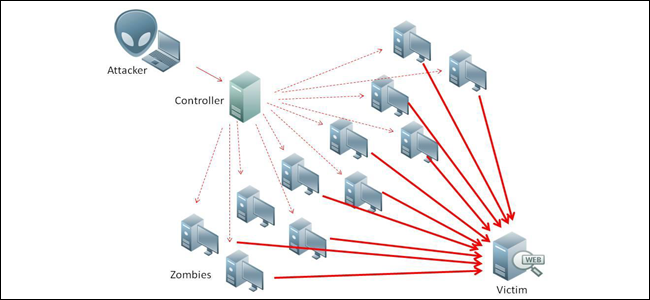
Real-time behavioral analytics, new tool for detecting advanced external and internal Cyber threats and mental health, employed by Intelligence agencies to DOD
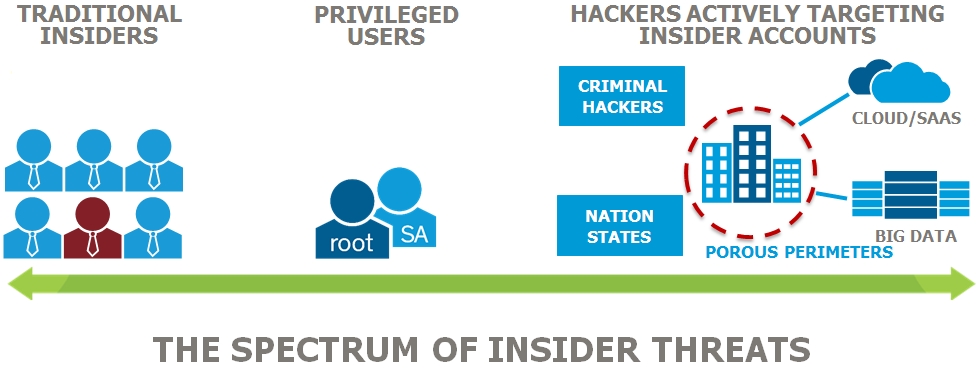
An insider threat is a malicious threat to an organization that comes from people within the organization, such as employees, former employees, contractors or business associates, who have inside information concerning the organization’s security practices, data and computer systems. The…...