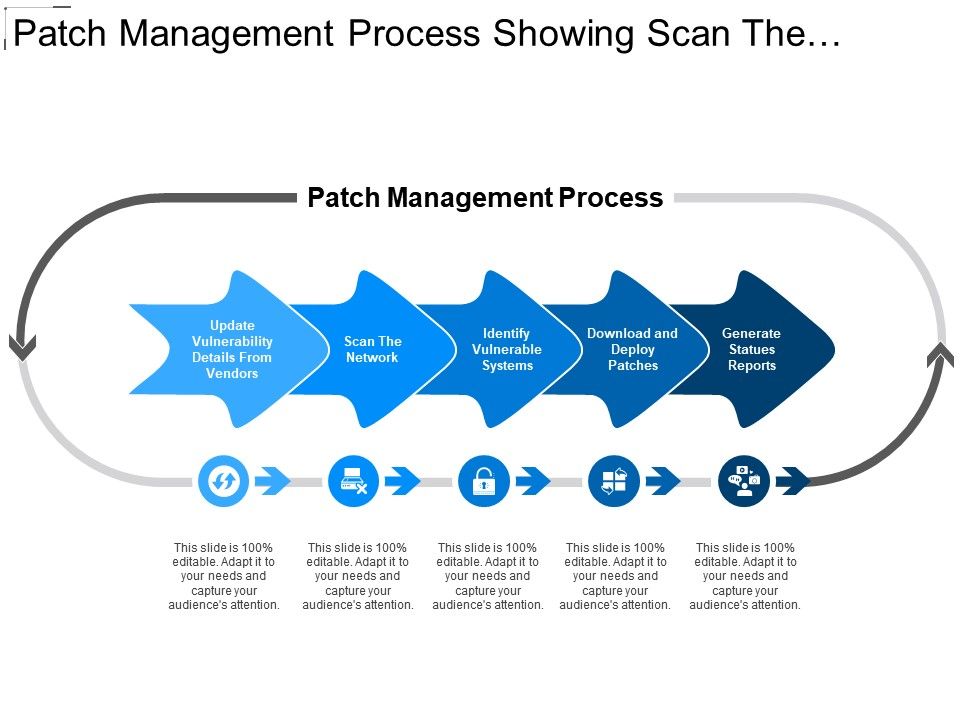
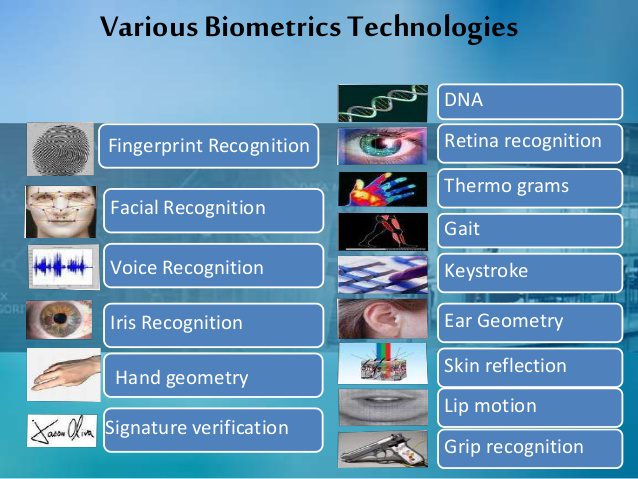
New Physical and behavioral Biometrics technologies with increased accuracy and security being developed
Identity theft is increasingly a 21st-Century problem. As more data moves off of physical paper and onto Internet-connected servers, the chances of that data getting stolen increases as well. According to the FTC, there were 2.8 million fraud reports from…...