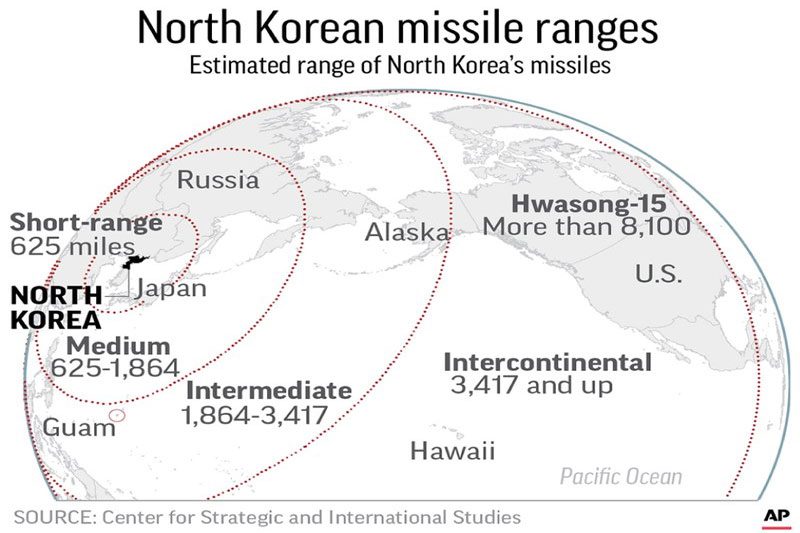
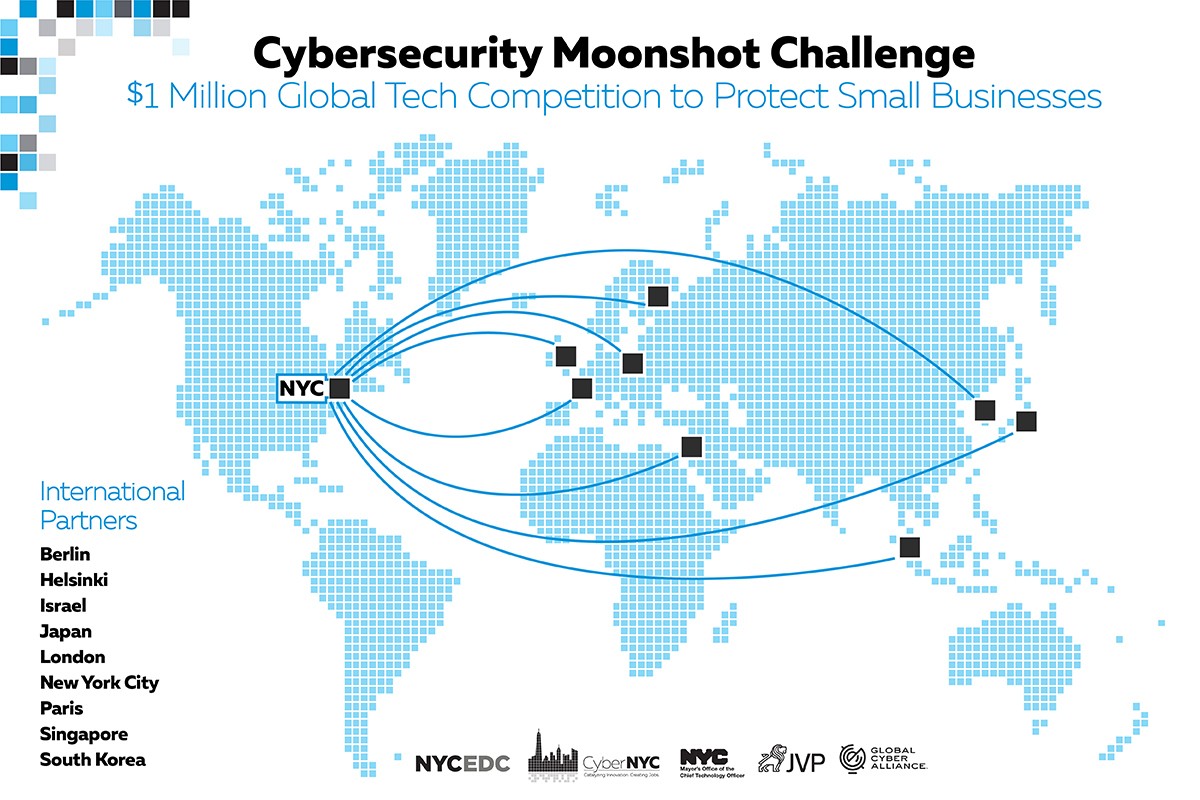
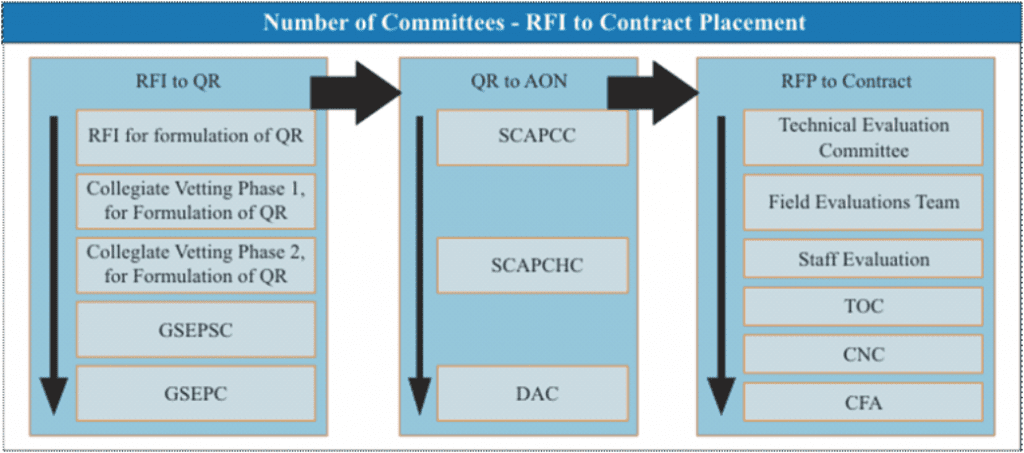
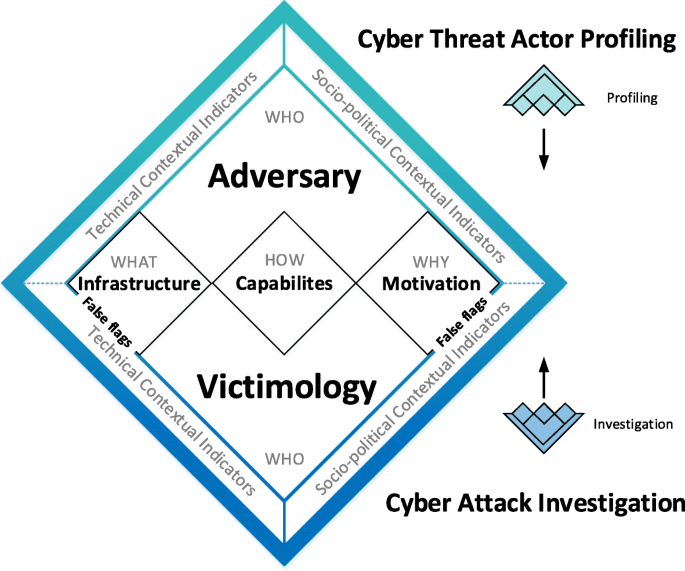
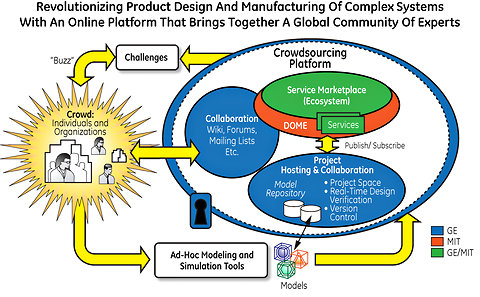
Enterprise architecture
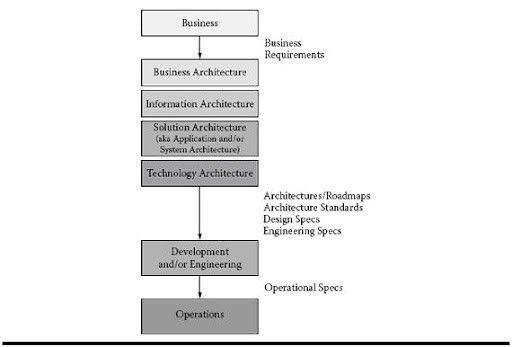
The term enterprise can be defined as describing an organizational unit, organization, or collection of organizations that share a set of common goals and collaborate to provide specific products or services to customers. In that sense, the term enterprise covers various…...