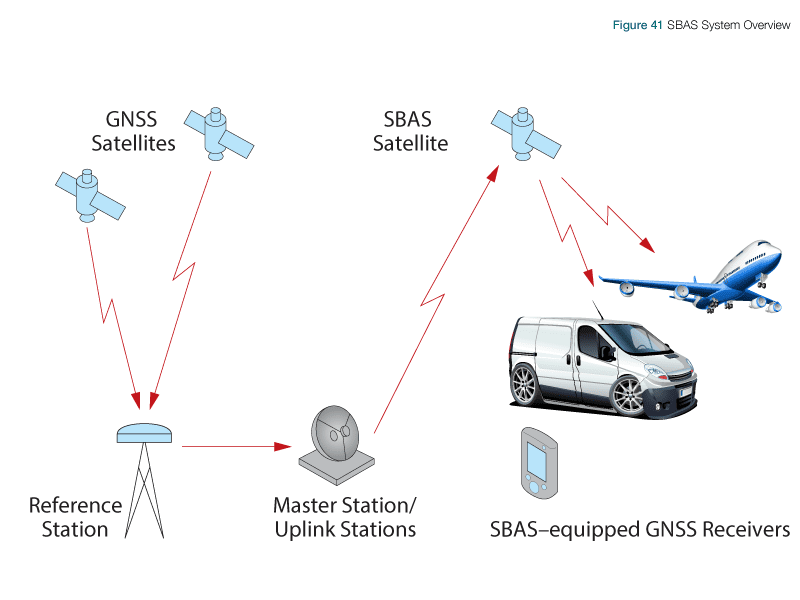
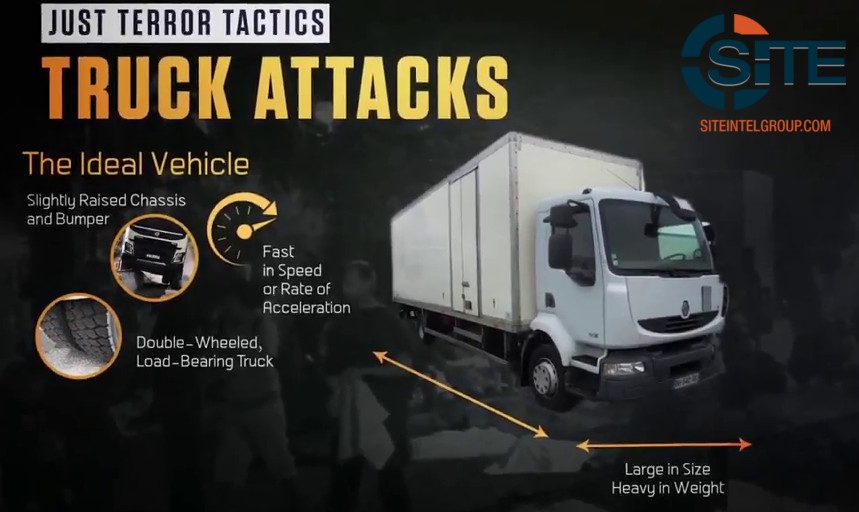
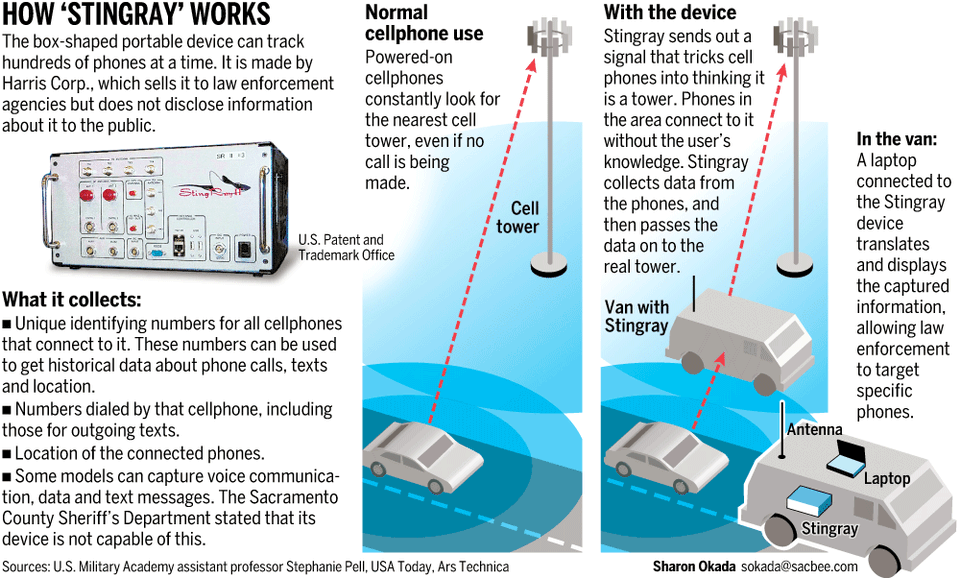
Telecoms are suffering more attacks than any other sector, Telcos Managing cyber security risks
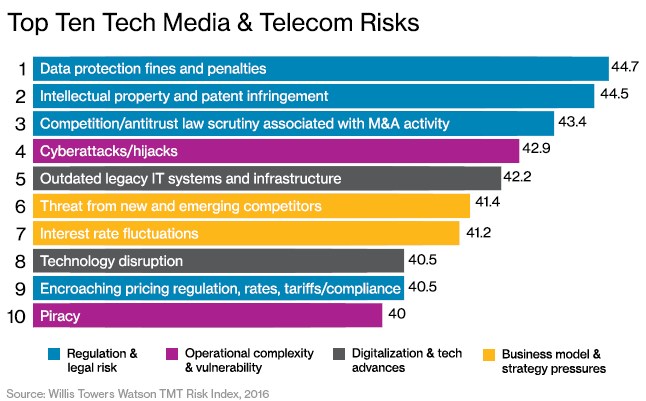
Telecoms companies, their core infrastructure and the large volumes of personal data they hold on subscribers, all represent an attractive target for malicious actors. Telecoms have suffered more attacks than any other surveyed. Telecoms organisations admitted to having faced four…...