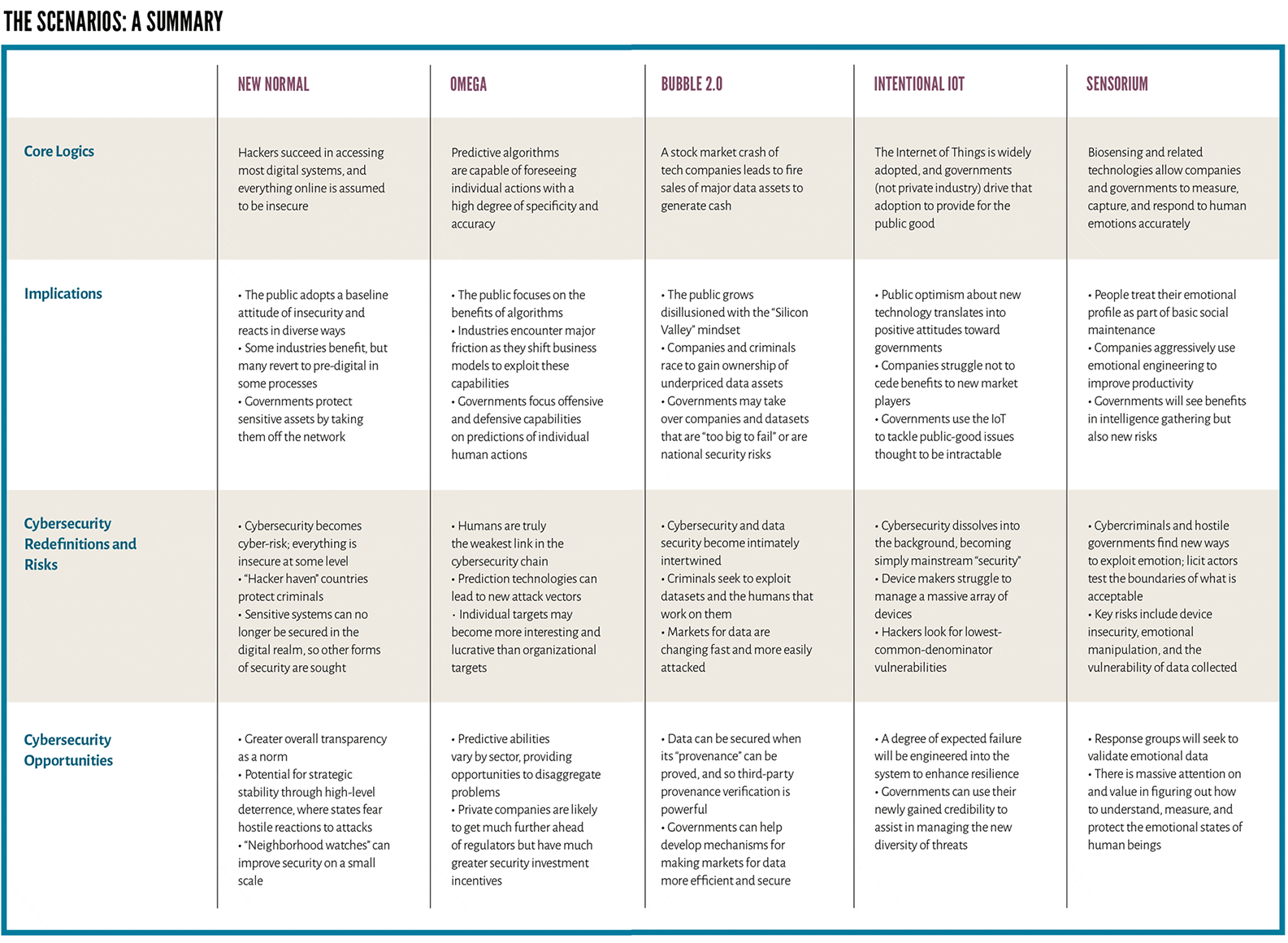
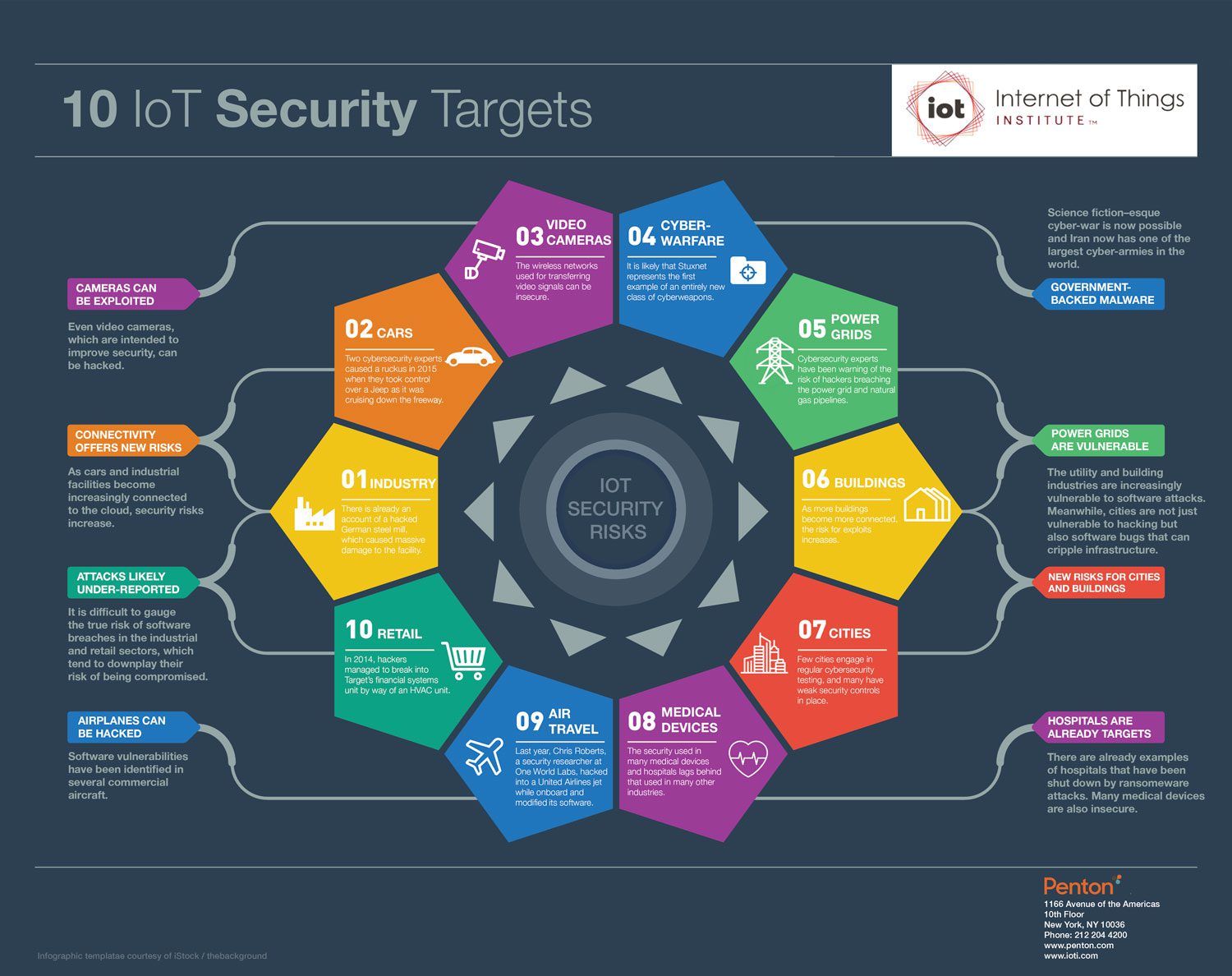
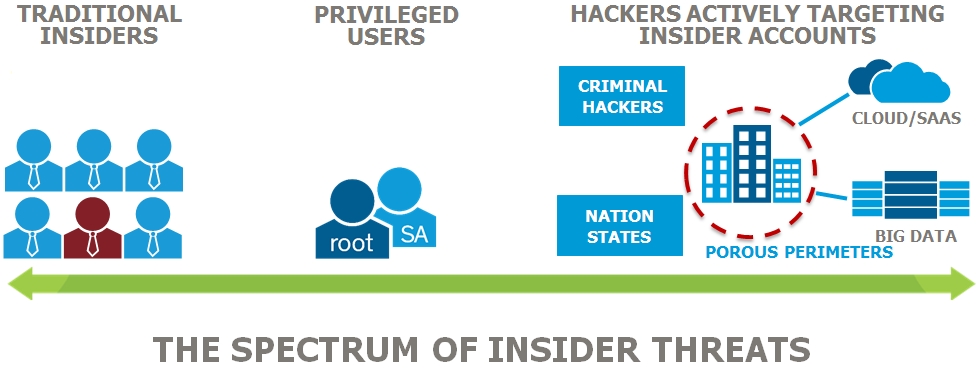
Military developing sound endpoint management strategies to deal with rising cyber-attacks and data breaches, and increasingly mobile workforce
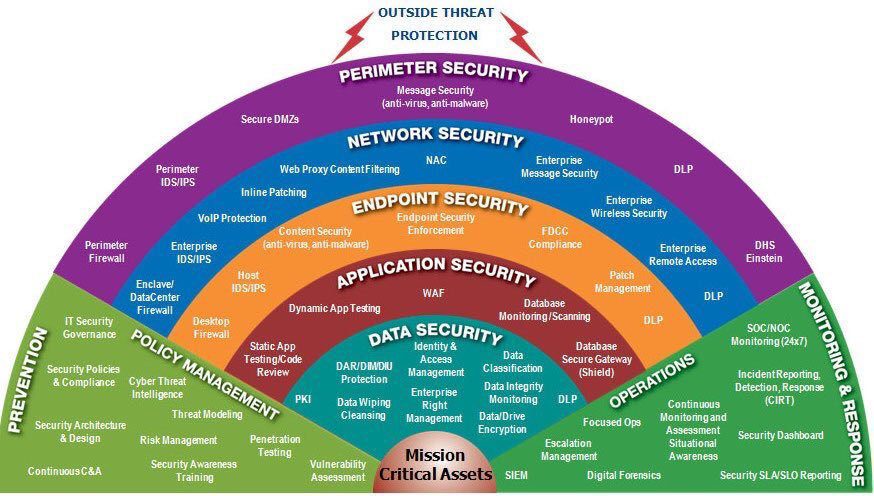
With the rise of cyber-attacks and data breaches, and today’s increasingly mobile workforce, securely managing data and endpoints without inhibiting employee productivity has become critical to organizations including military. Many devices including smart phones, tablets and laptops now have network…...