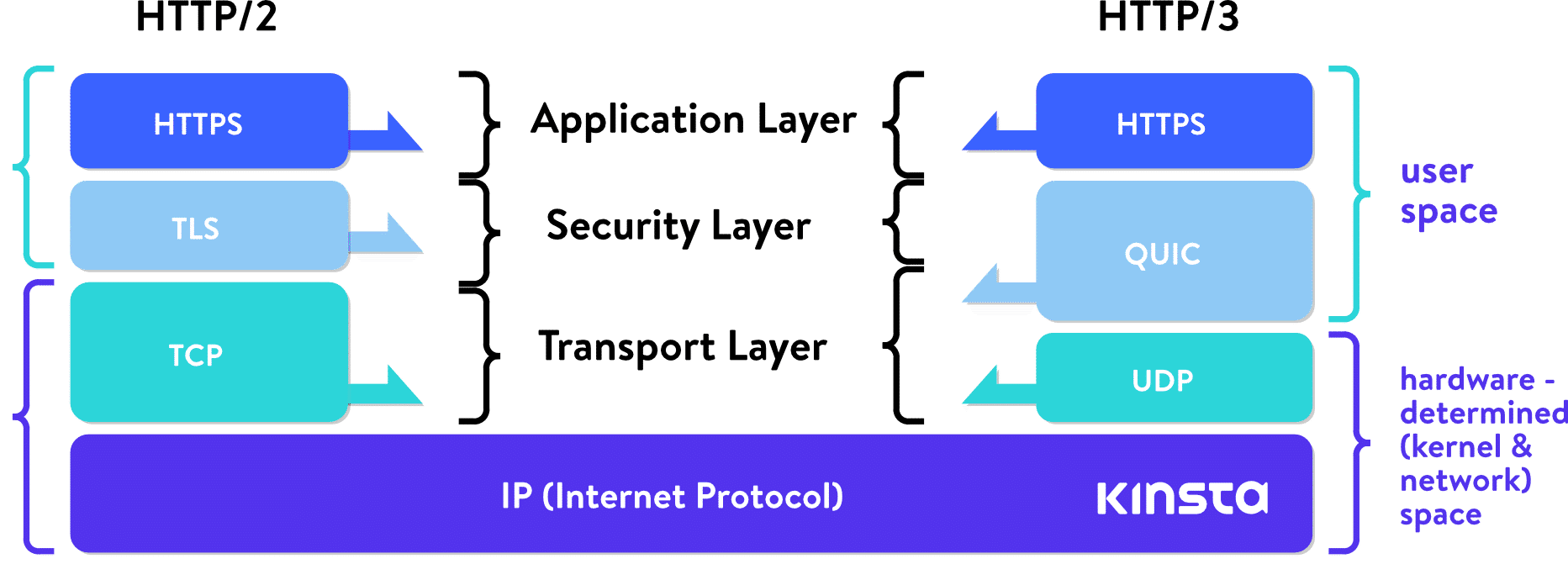
Internet becoming secure and faster through QUIC, the new transport protocol set to replace TCP and HTTP/3
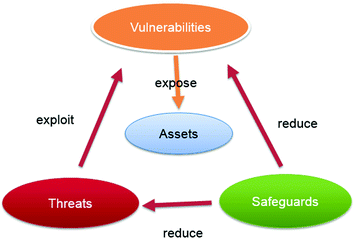
As the Military and civilian technological systems, from fighter aircraft to networked household appliances, are becoming ever more dependent upon internet, they are also becoming more vulnerable to hackers and electronic intruders. Electronic system security has become an increasingly critical…...