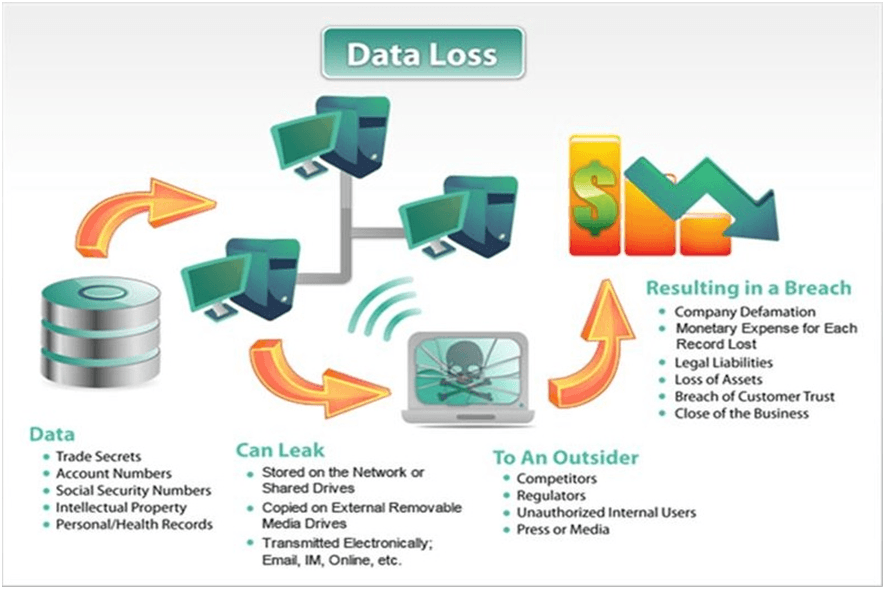
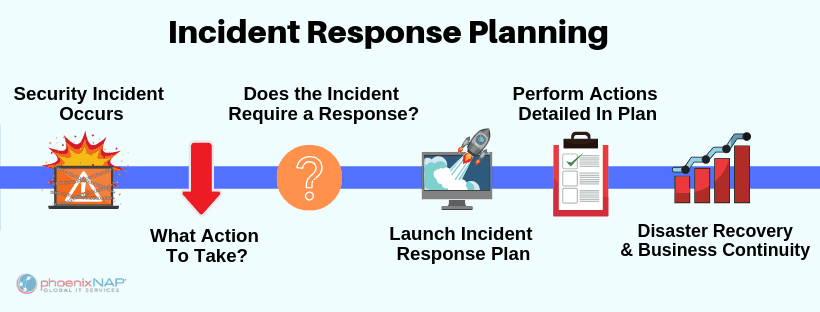
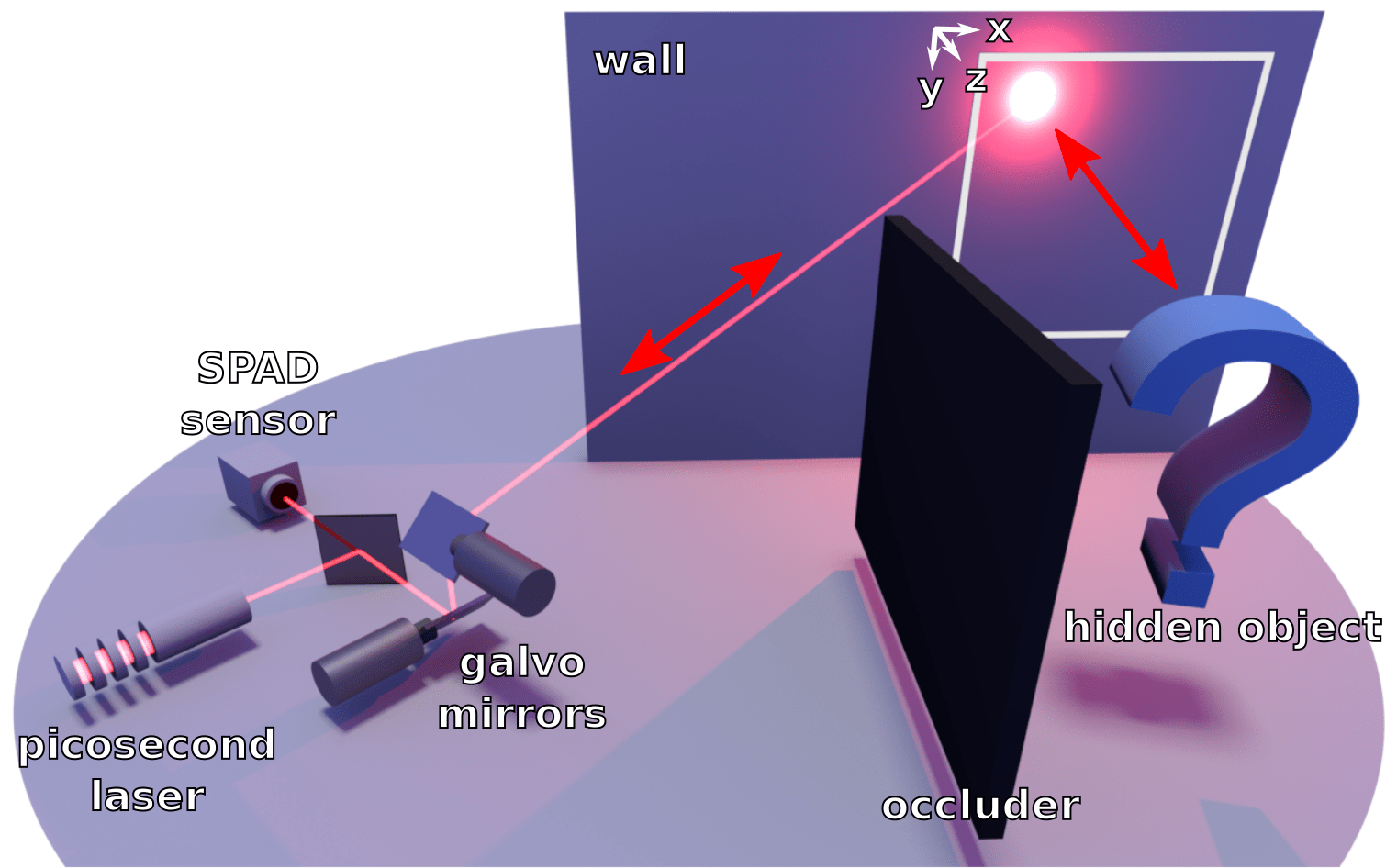
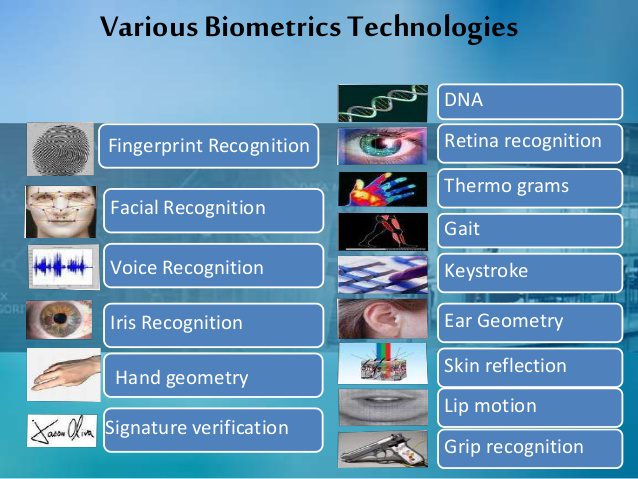
Ground-penetrating radar for Autonomous driving, to detection of Tunnel, landmine and buried IEDs

Radar is an electromagnetic sensor used for detecting, locating, tracking, and recognizing objects of various kinds at considerable distances. It operates by transmitting electromagnetic energy toward objects, commonly referred to as targets, and observing the echoes returned from them. Energy is…...