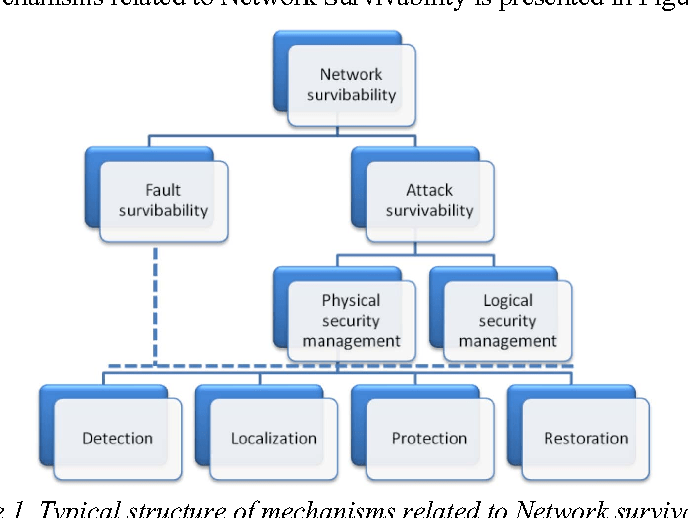
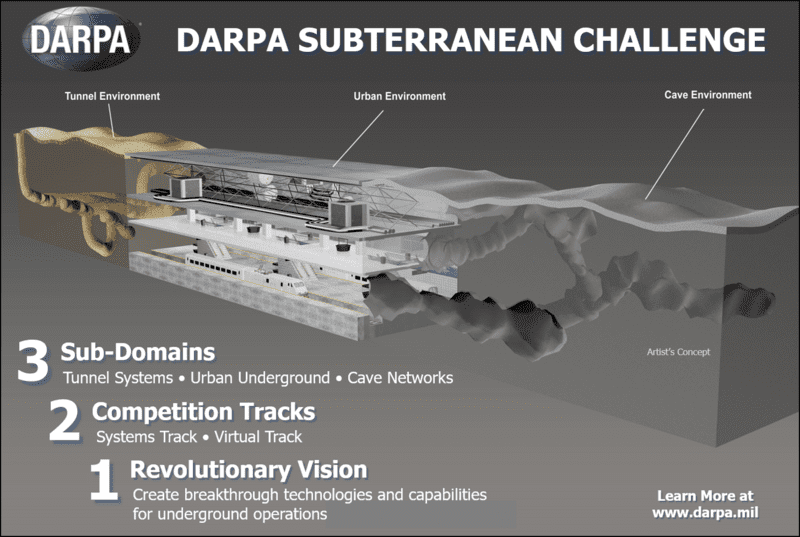
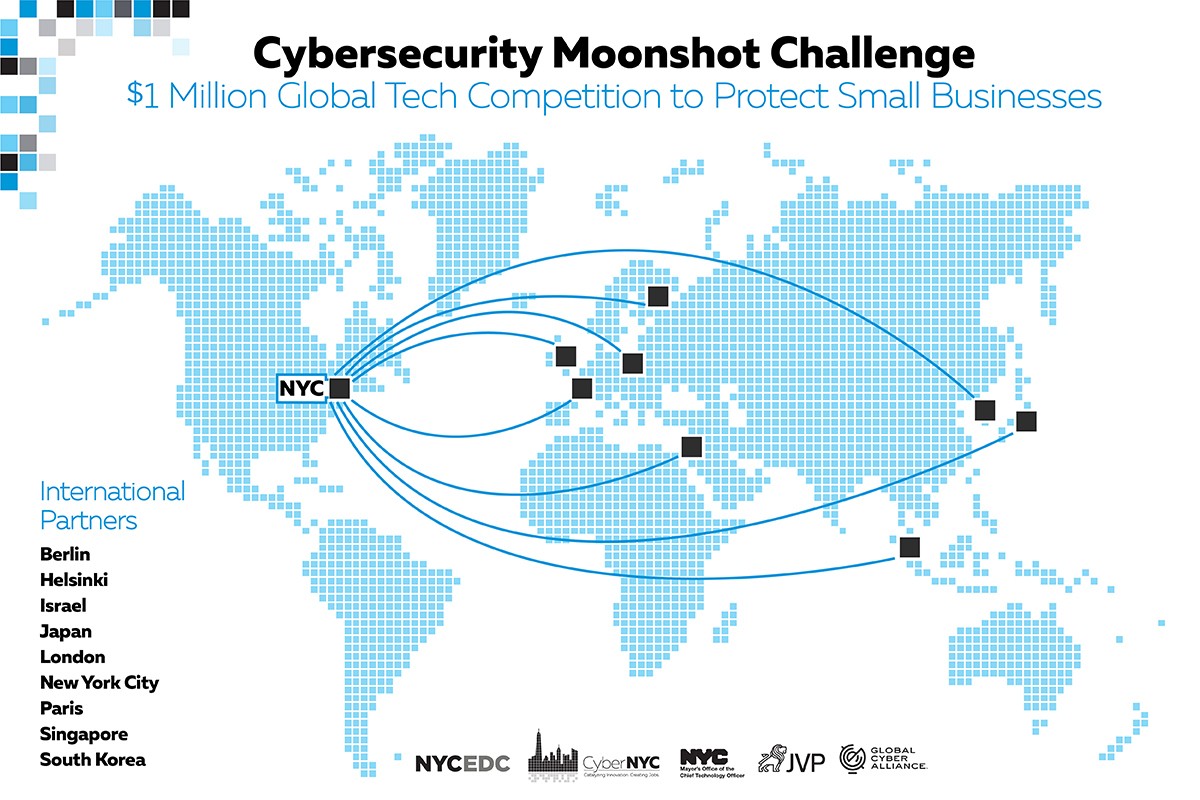
Growing Cyber threats to commercial aviation require cyber risk management, and resilient systems
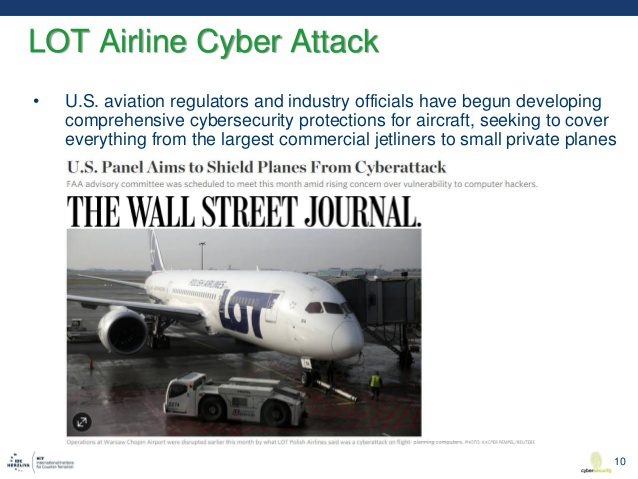
Cyber attacks are growing in number and sophistication affecting large corporations, critical infrastructures of all kinds, governments to SMEs, and increasingly the aviation industry. Commercial aviation plays a central role in our daily lives and is an essential part…...