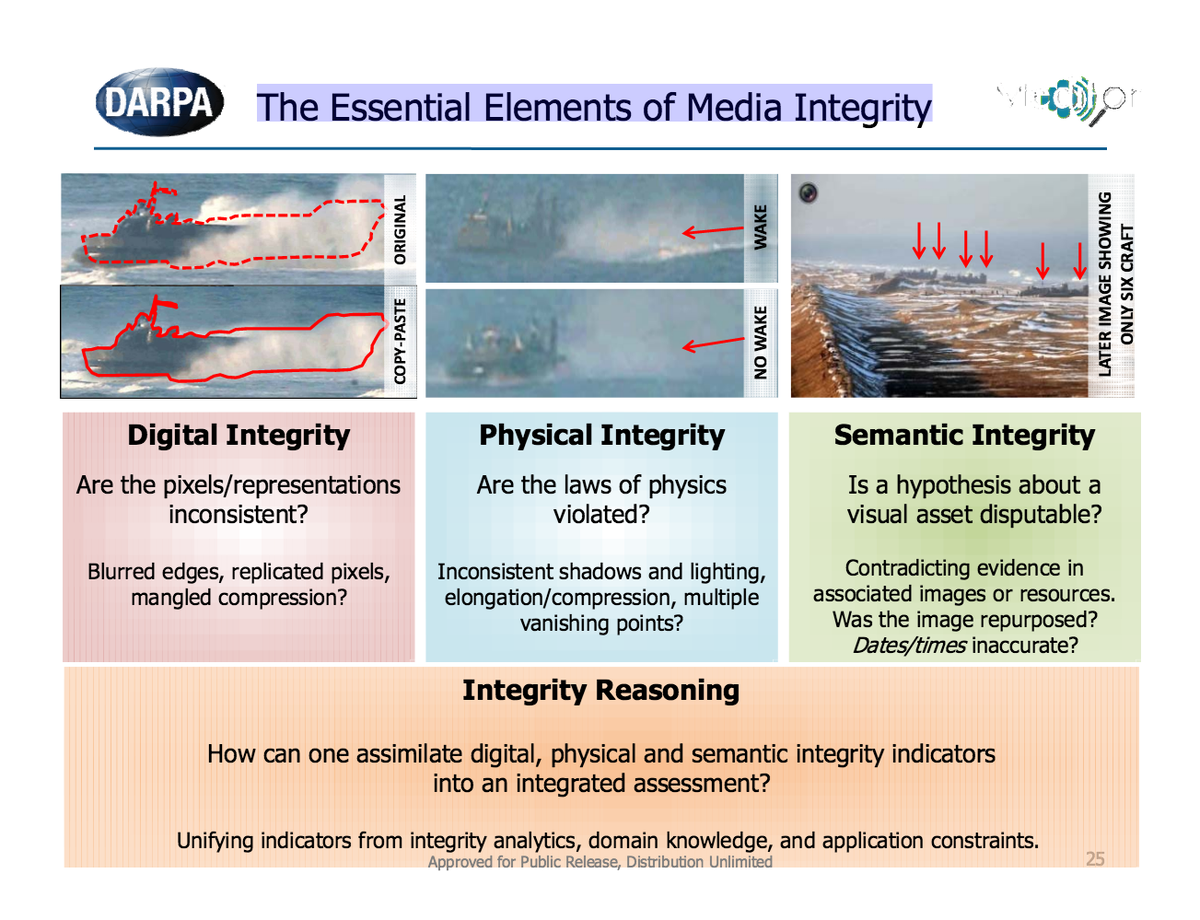
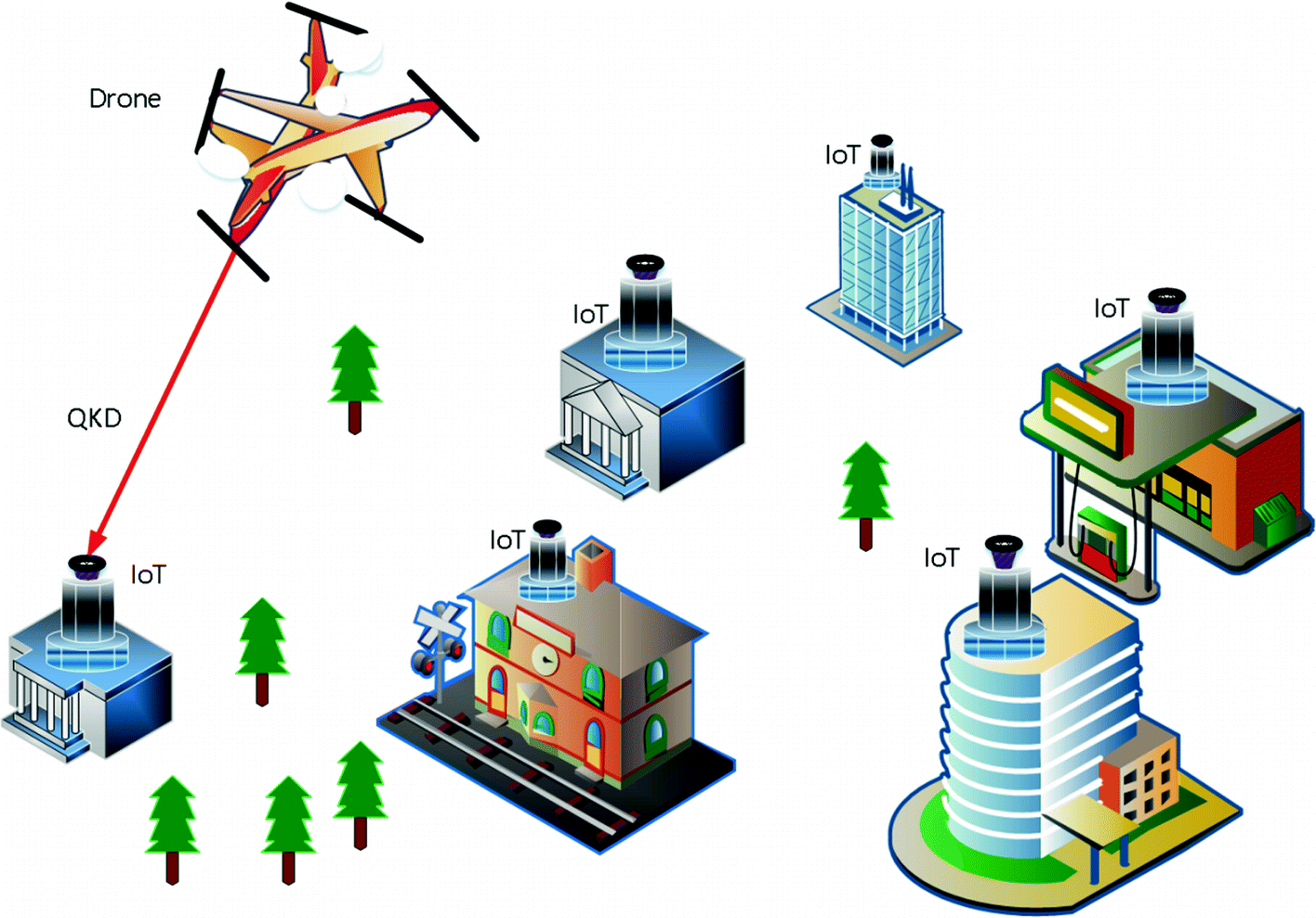
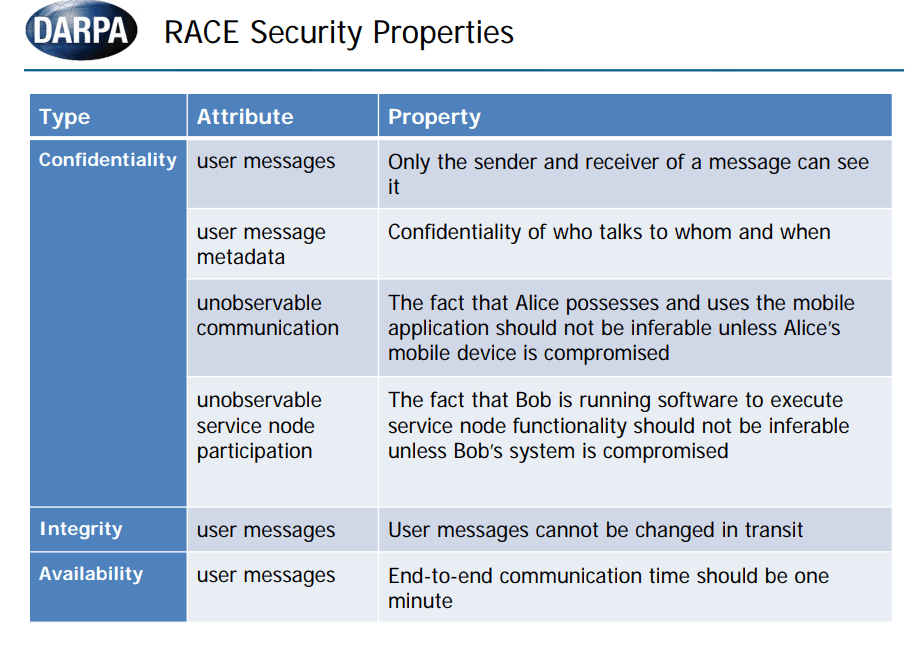
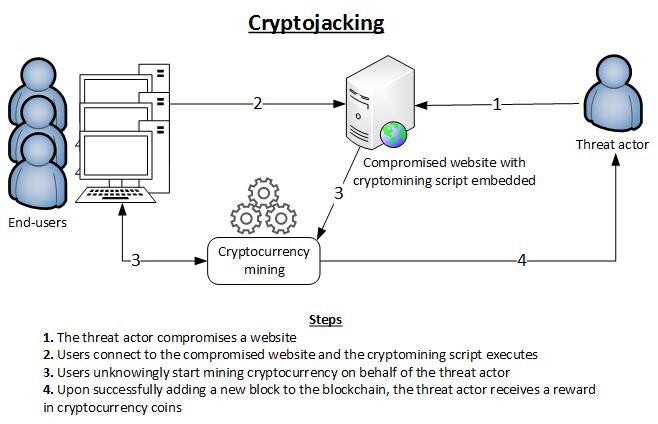
SpaceChain deploys Internet of blockchains , other Countries also plan Blockchain space technology,

Historically, there was a necessity for a third party that demanded a payment to perform transactions or submit information to ensure the accuracy of transactions and create a reliable history. Blockchain eradicates the need for an intermediary through creating a…...