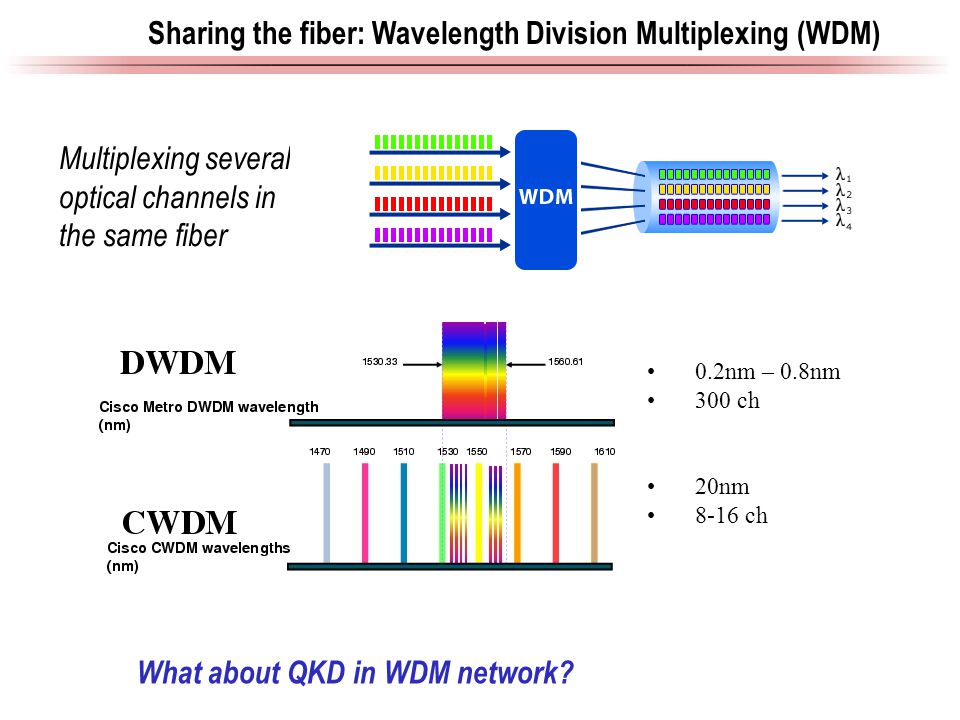
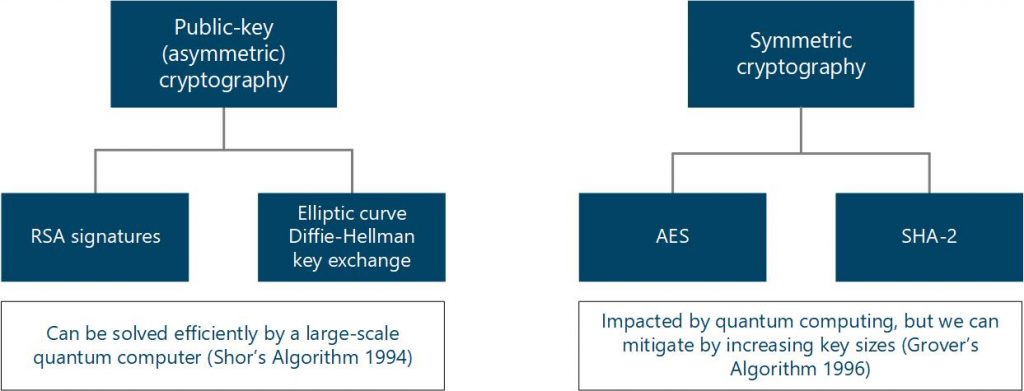
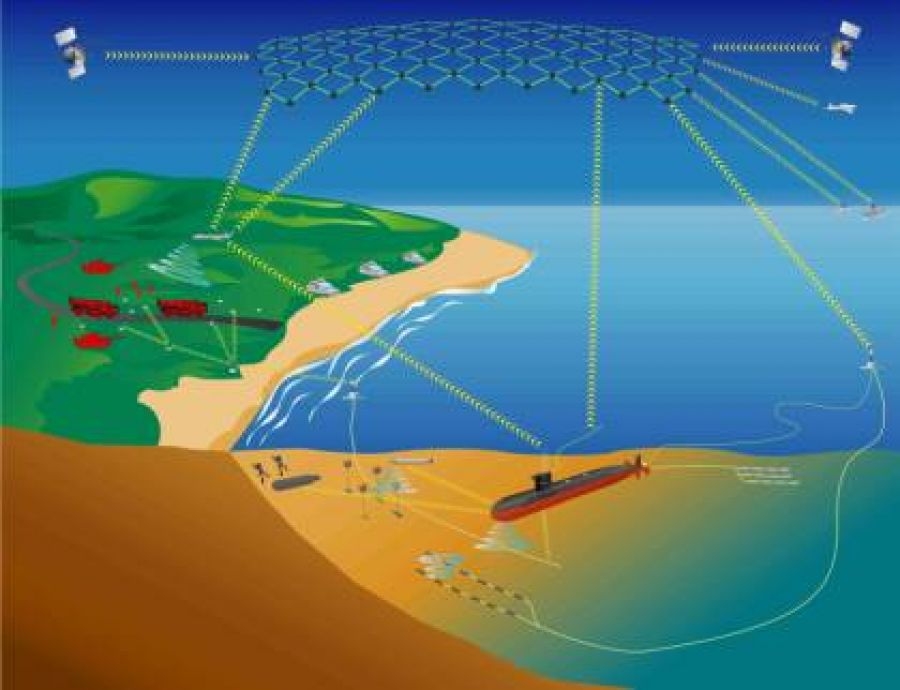
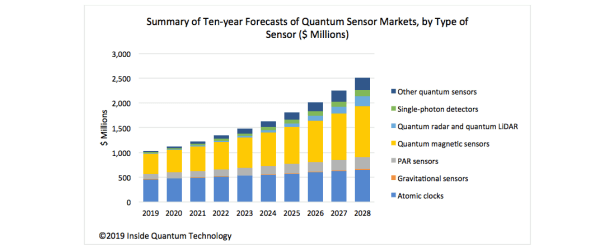
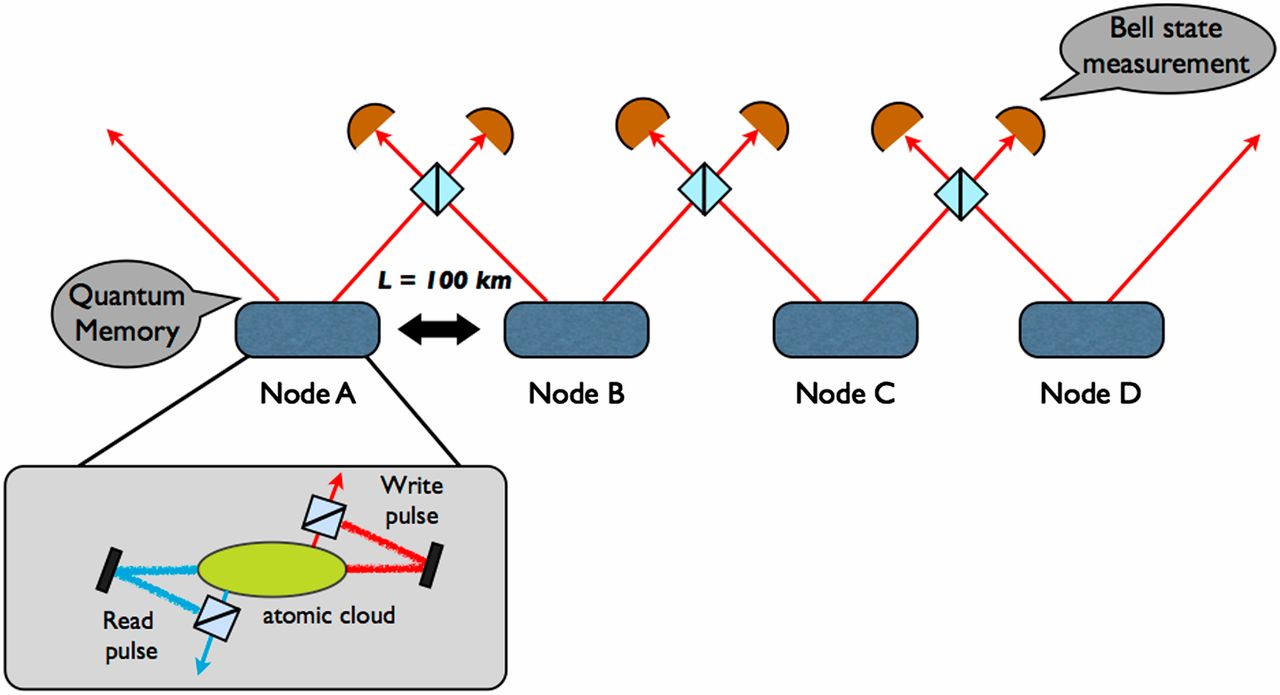
Quantum thermodynamics and Quantum Heat Engines can lead to development of microscopic heat engines, refrigerators and solar cells
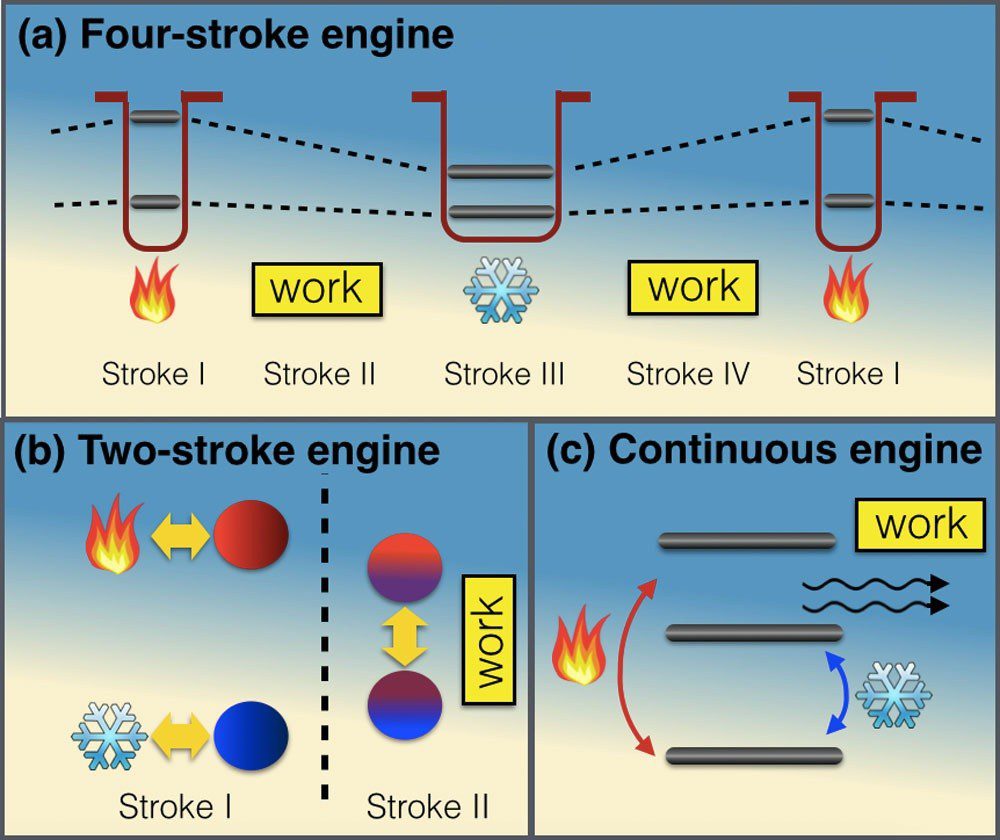
One of the most important features of thermodynamics is that it has improved human quality of life amazingly during the last centuries. Since in 1606, the Spanish inventor Jerónimo de Ayanz y Beaumont patented the first steam engine a great…...