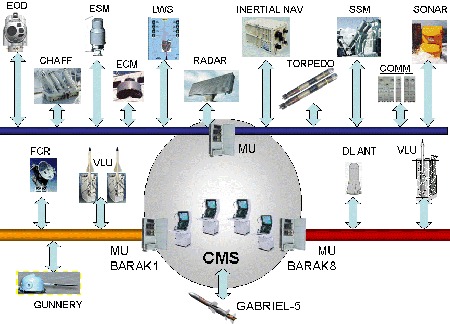
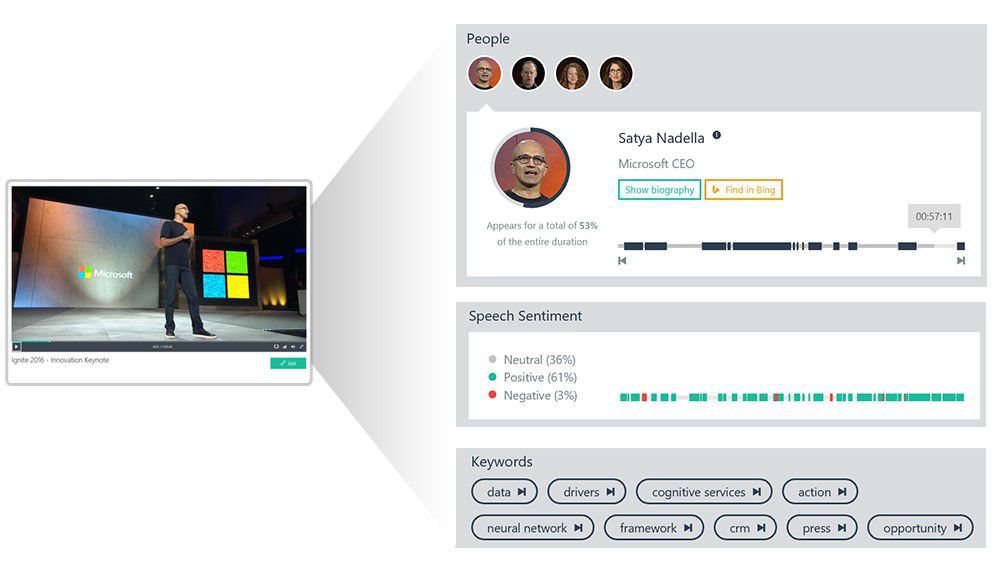
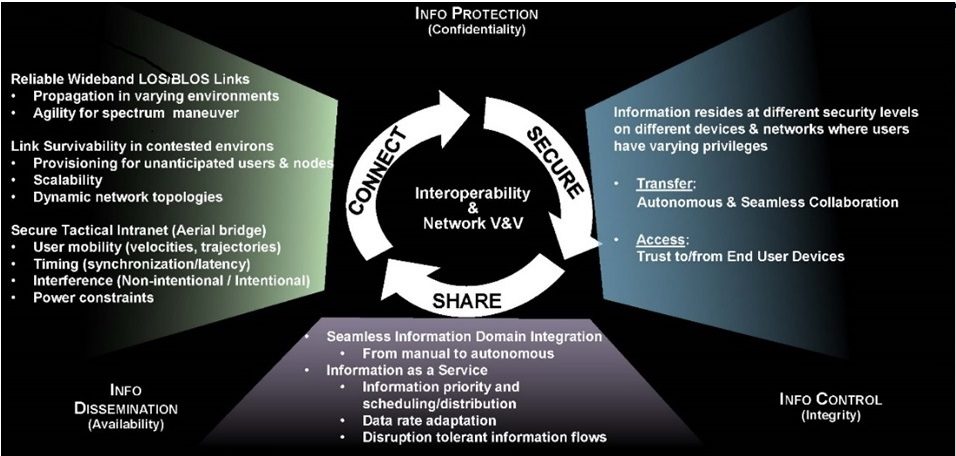
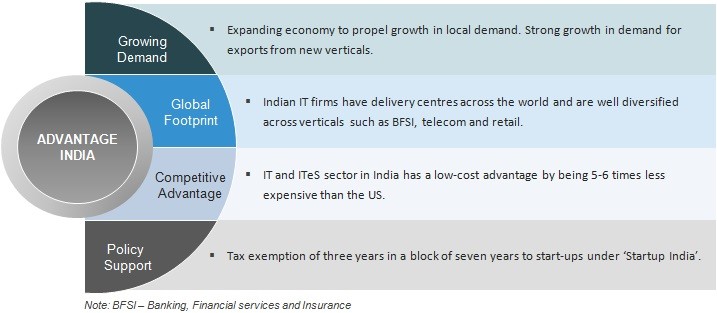
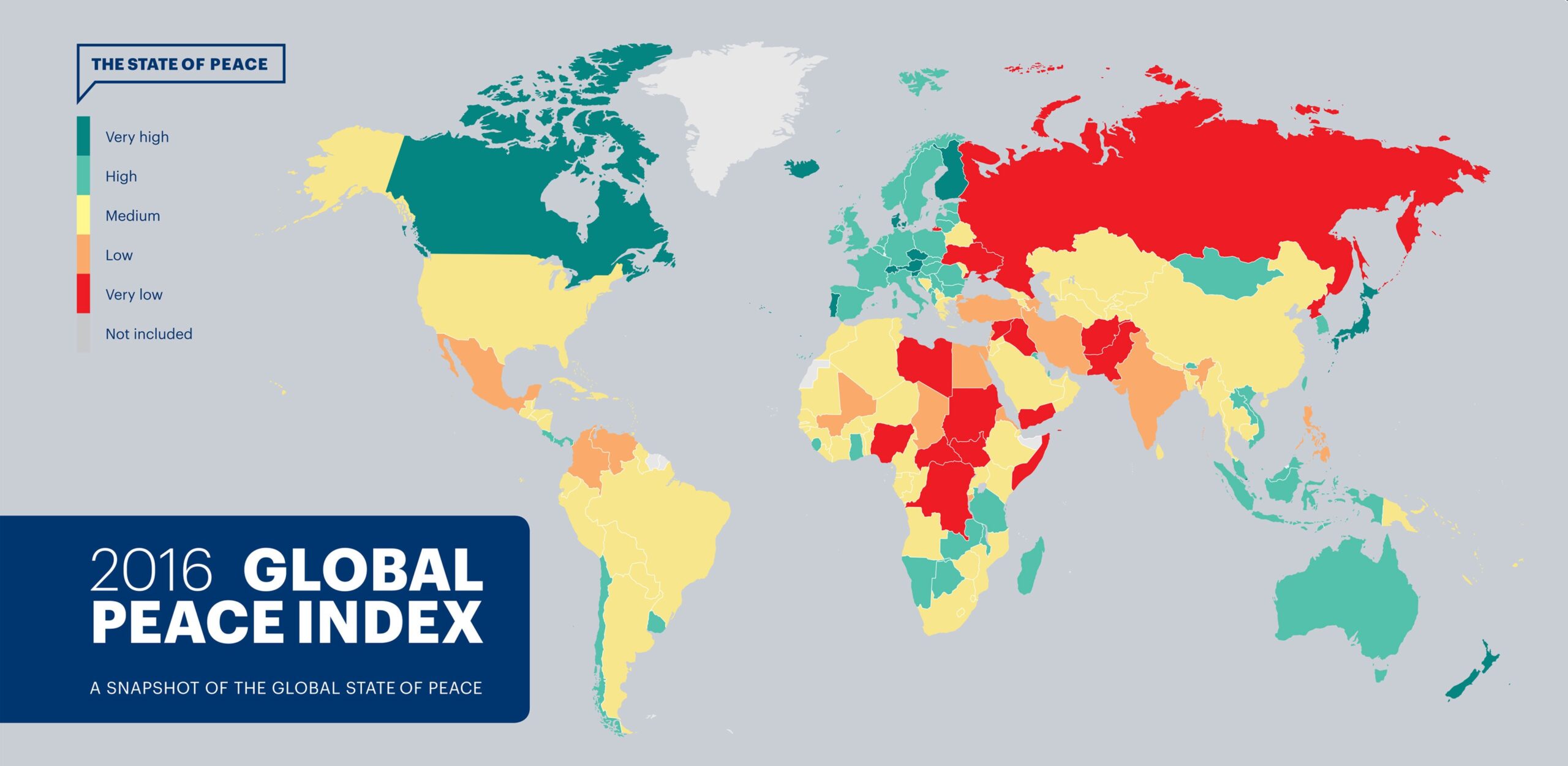
Generative adversarial networks or dueling Neural Networks can bestow AI systems with “imagination” and also poison AI defences
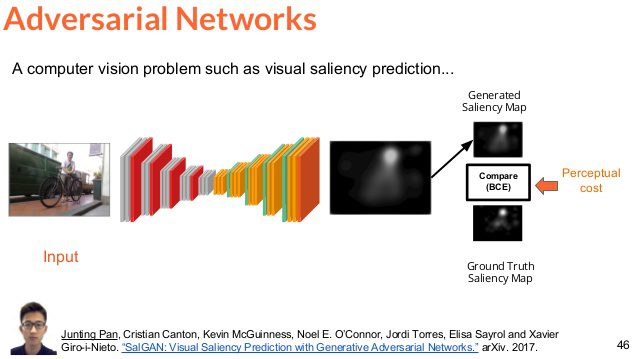
Most AI advances and applications are based on a type of algorithm known as machine learning that finds and reapplies patterns in data. Deep learning, a powerful subset of machine learning, uses neural networks to find and amplify even the smallest…...