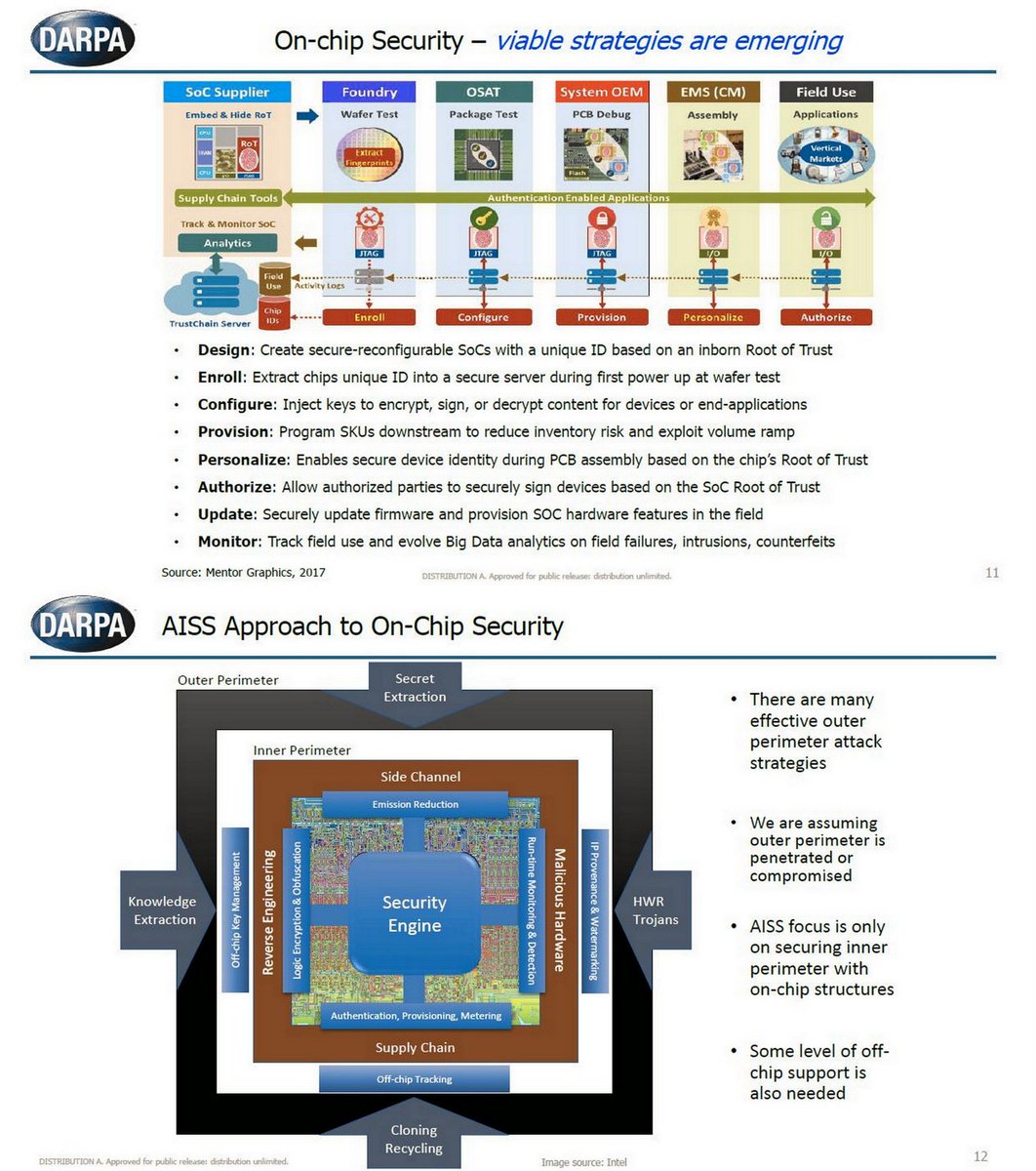
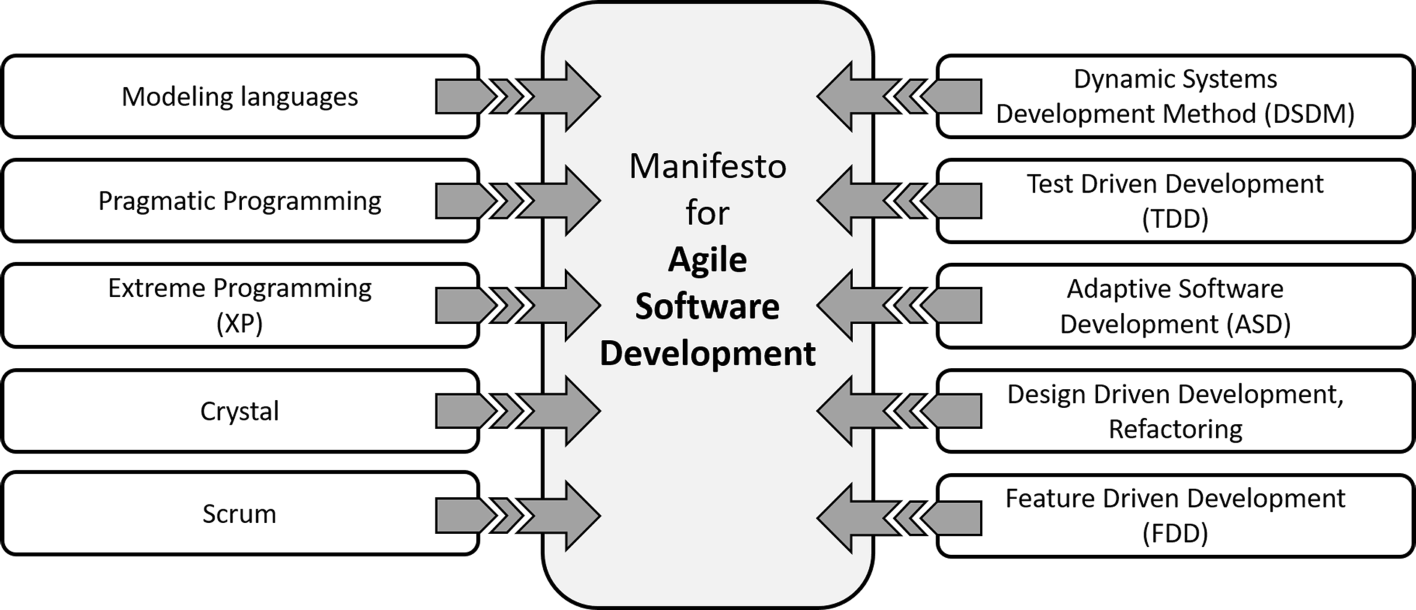
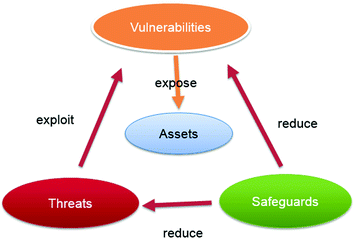
NASA’s Software Assurance through Software policies, engineering practices and software standards

As computing devices become more pervasive, the software systems that control them have become increasingly more complex and sophisticated. Computers are increasingly being introduced into safety-critical systems, and, as a consequence, have been involved in accidents. The world has become reliant…...