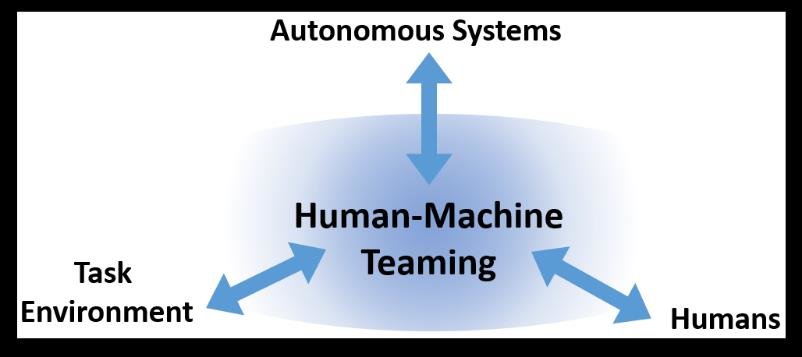
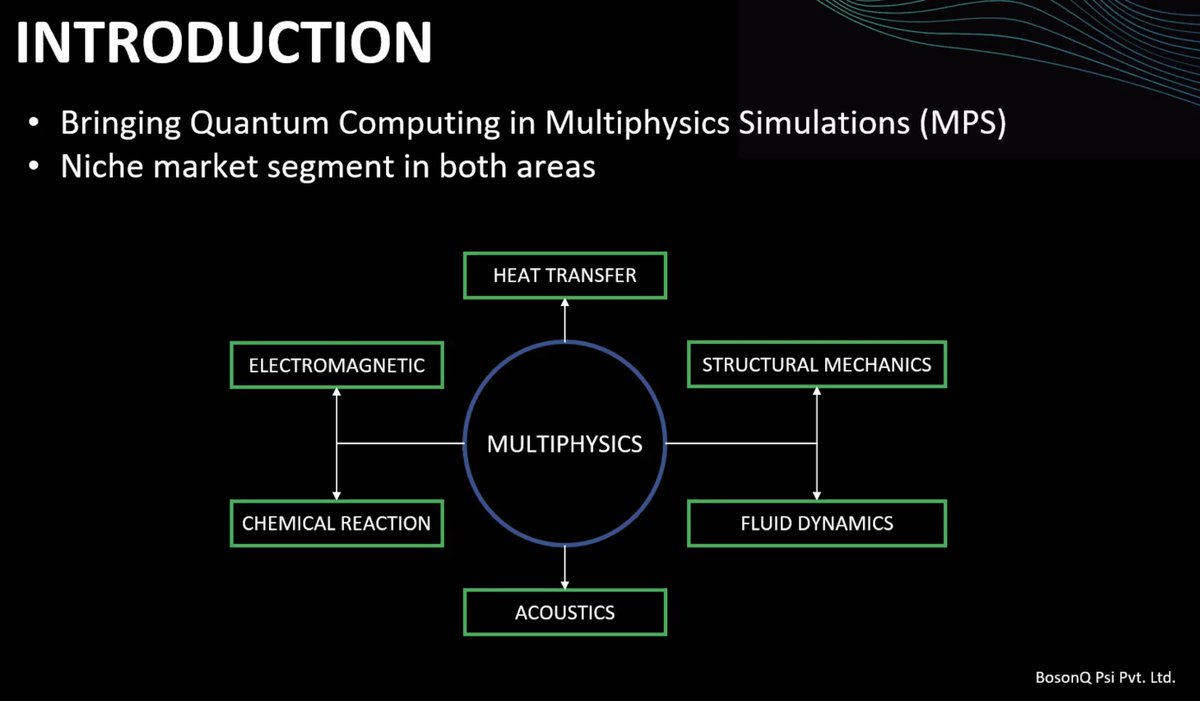
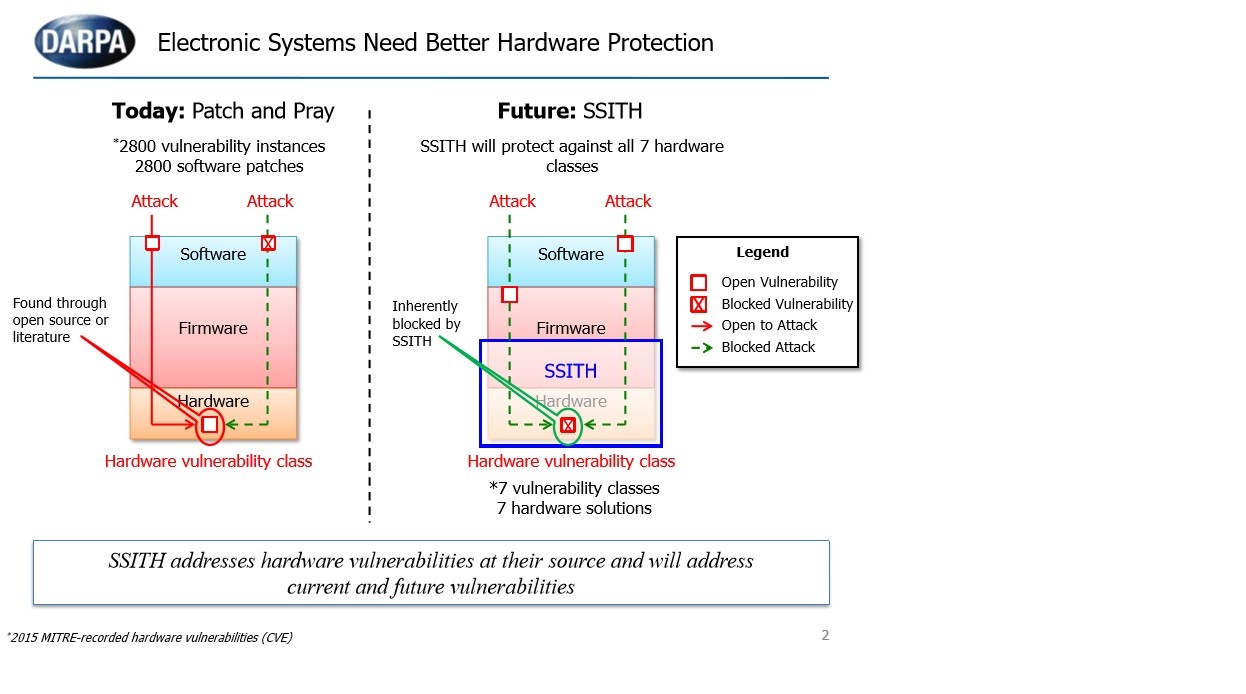
DARPA SSITH developed secure hardware architectures for Unhackable Military systems, FETT testing exploits to thwart Tampering
As 5G and IoT proliferation sweep across the planet, businesses and consumers are benefiting greatly from increased connectivity. However, this connectivity is also introducing greater risks and security concerns than ever before. As the Military and civilian technological systems, from…...