China J-20 stealth fighter’s combat missions in the South China Sea, advancing China’s A2/AD strategy
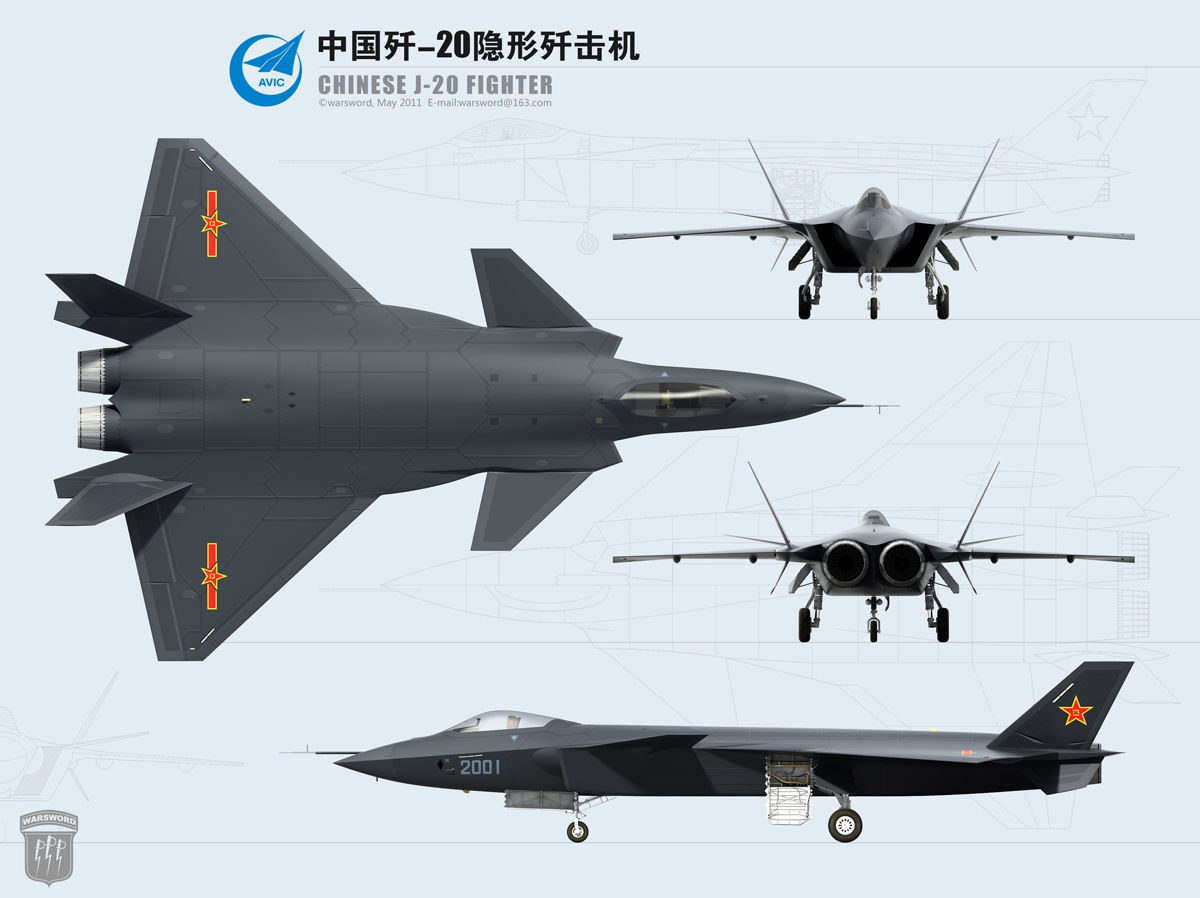
China’s progress toward military superpower status continues to accelerate. According to the latest one, the People’s Liberation Army Air Force (PLAAF) now ranks as the third-largest air force in the world with 2,250 combat aircraft. The People’s Liberation Army Navy…...