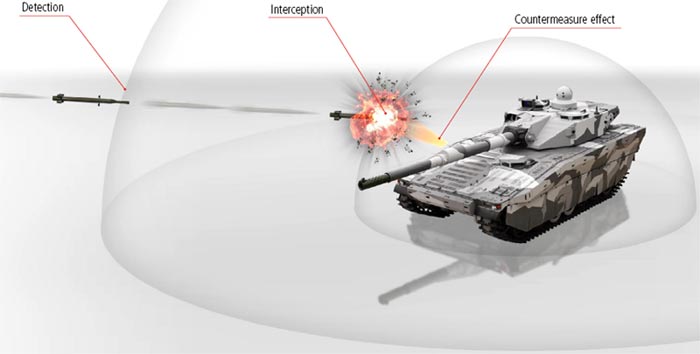
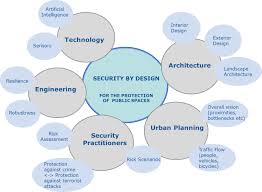
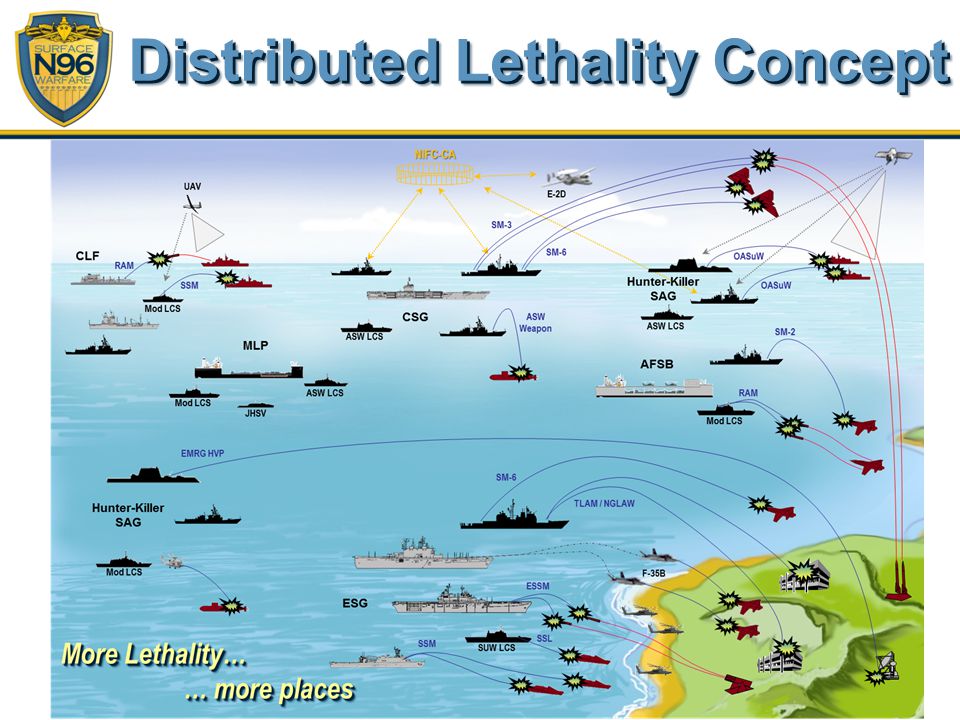
Countering Foreign Interference and Knowledge security
State actors use a variety of methods to acquire knowledge and technology that they can use for military purposes or for objectives that are not consistent with our fundamental values. Examples include centrally controlled talent programmes, applying pressure to compatriots…...