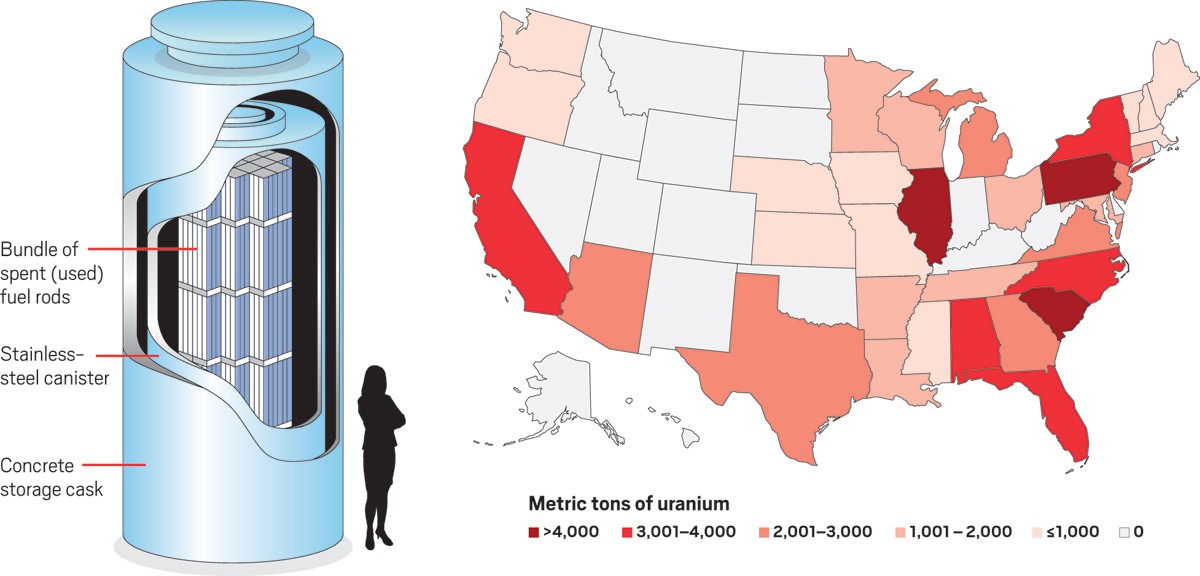
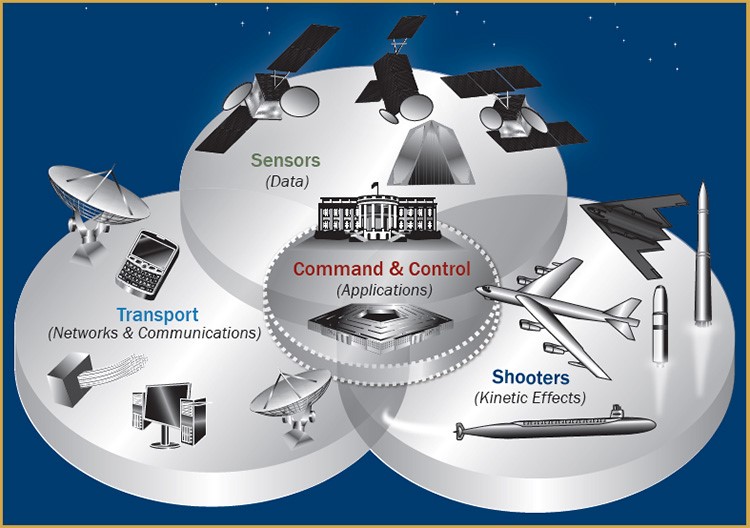
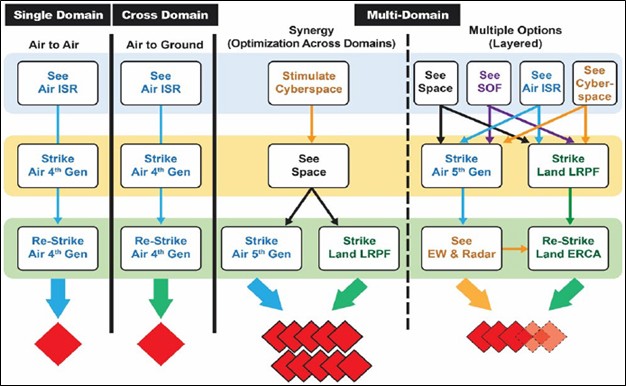
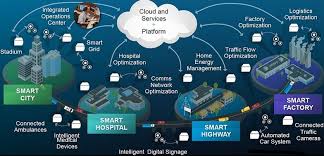
Countries advance Border management Strategy and technology to counter terrorists, and criminals, smuggling weapons, and illegal drugs, and counterfeit goods
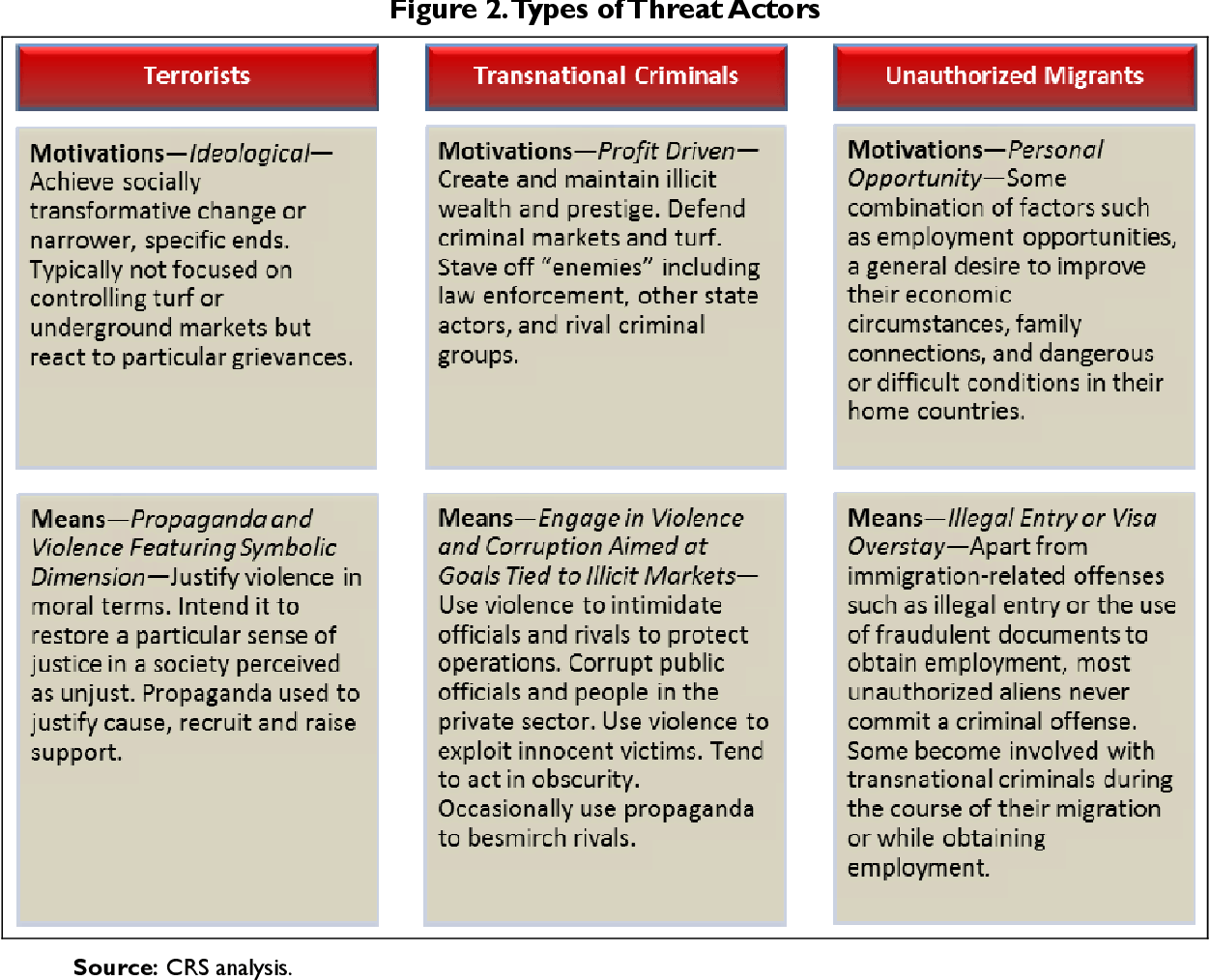
In an increasingly globalised and interconnected world it has become simple for people and goods to cross borders and so for terrorists. America’s borders and ports are busy places, with tens of millions of cargo containers and hundreds of millions…...