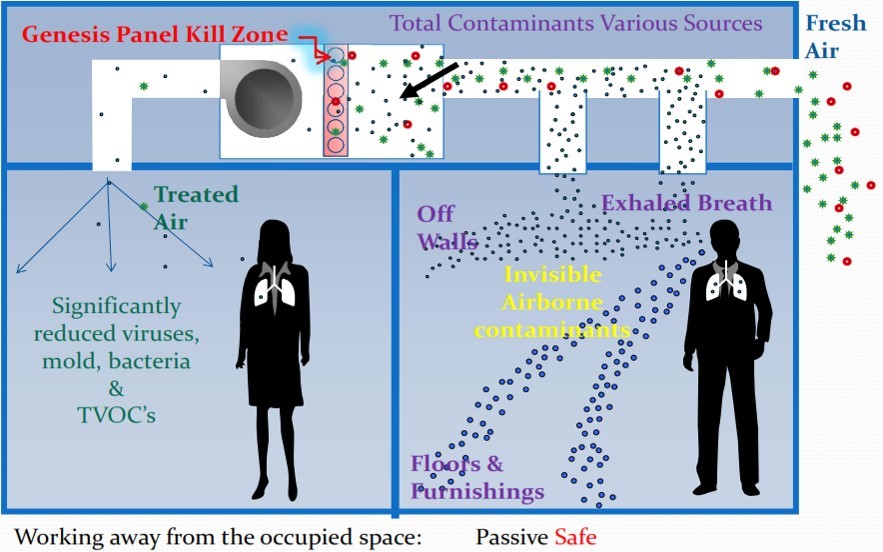
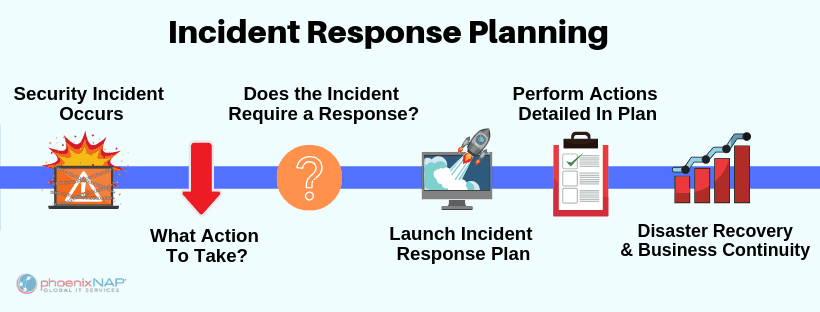
DARPA MICE will quantify how authoritarian regimes control information

Authoritarianism is a form of government characterized by the rejection of political plurality, the use of strong central power to preserve the political status quo, and reductions in the rule of law, separation of powers, and democratic voting. Authoritarian states…...