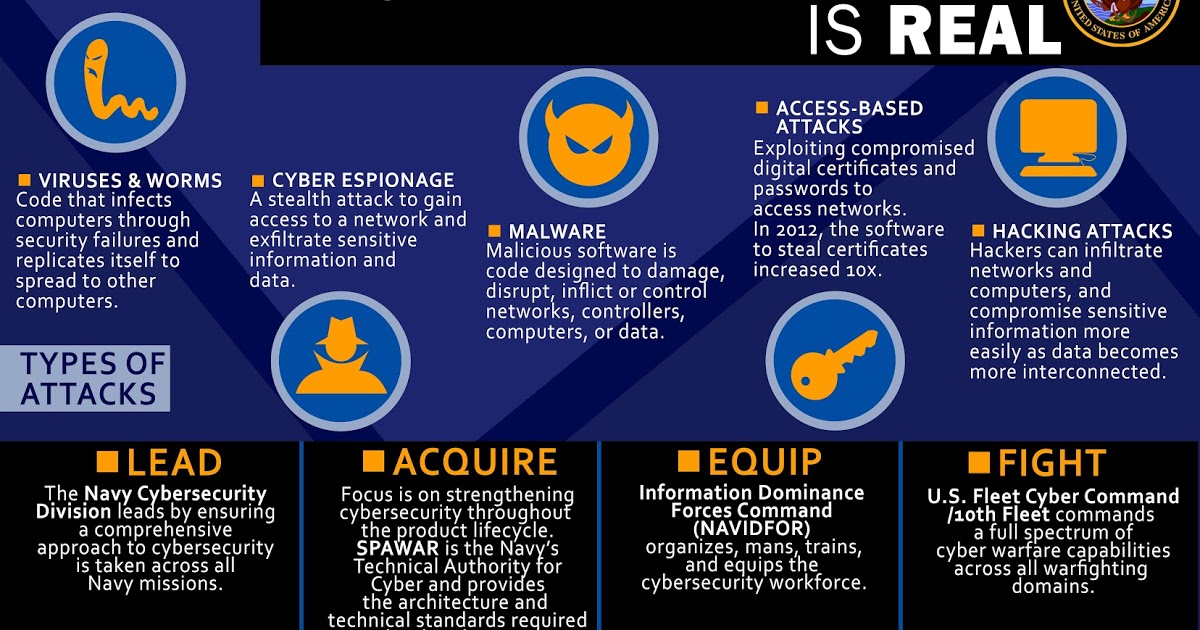
Global threat Intelligence and warnings shared by Cyber Agencies enables mitigating cyber threats before large scale exploitation by hackers

According to the World Economic Forum’s 2016 Global Risks Report, cyber-security is recognised as one of the greatest threats to business worldwide, and the global cost of crimes in cyberspace is estimated to be $445bn. By 2021, cybercrime damage is…...