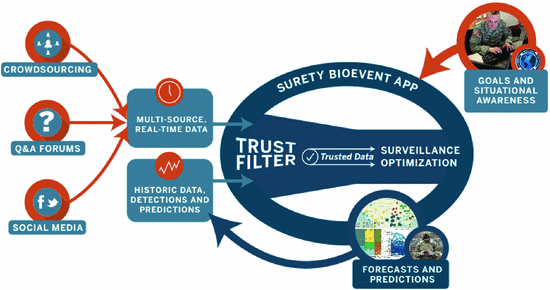
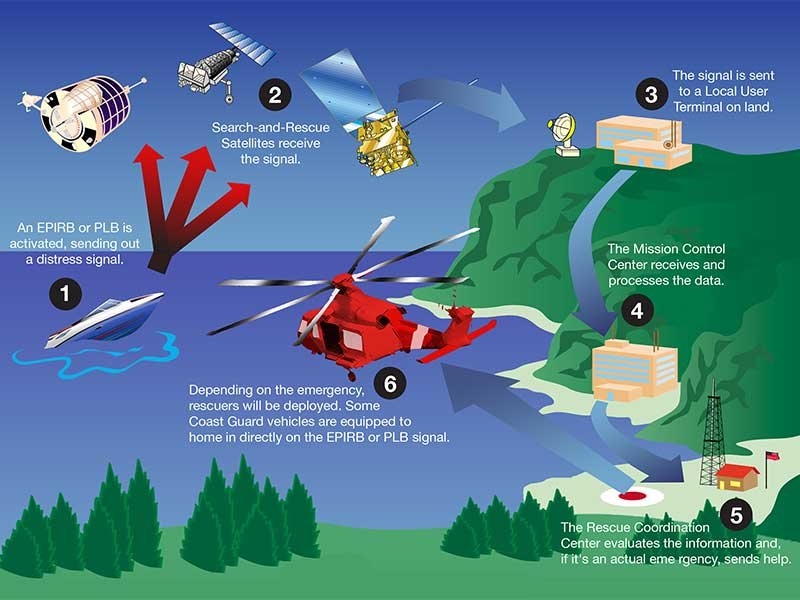
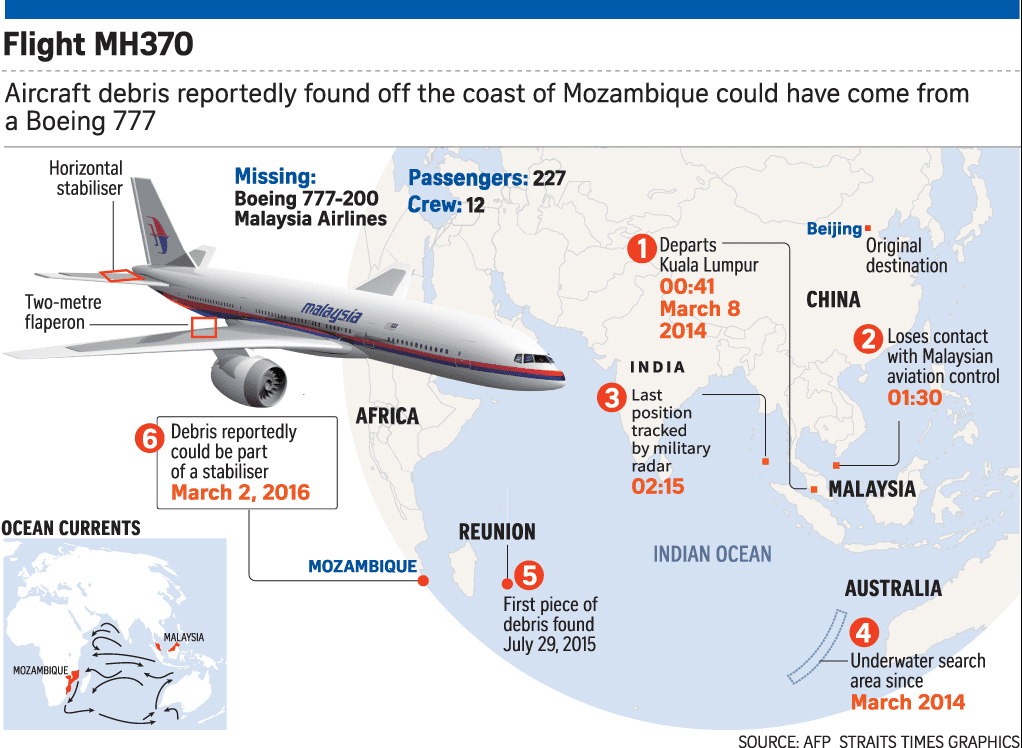
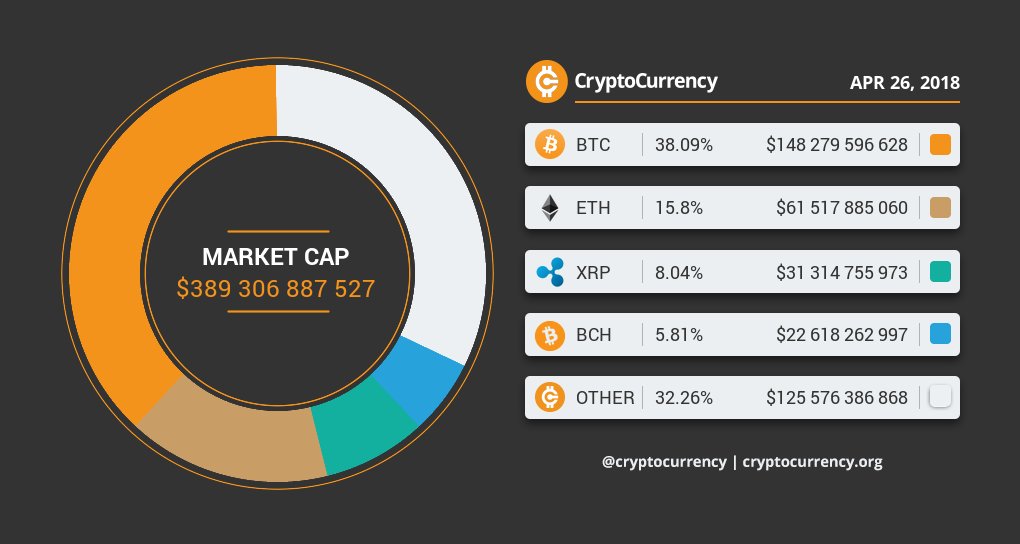
Growing Threat of Biohacking or DNA Malware with development of DNA based Biocomputers and memories
Recently biocomputers are becoming feasible due to advancements in nanobiotechnology and Synthetic Biology. Biocomputers use systems of biologically derived molecules—such as DNA and proteins—to perform computational calculations. It is expected that the most significant advantage of the DNA chip will…...