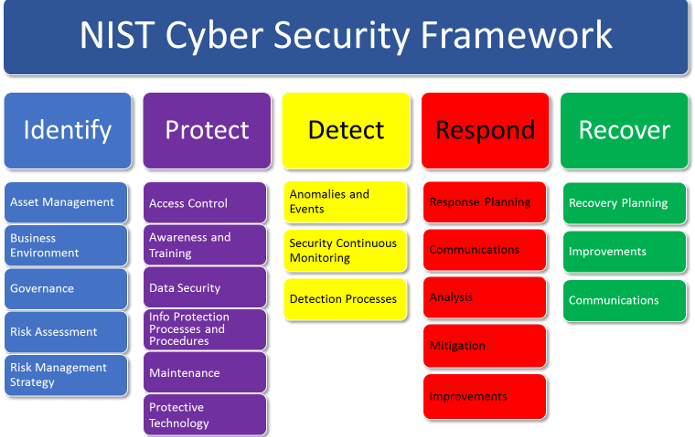
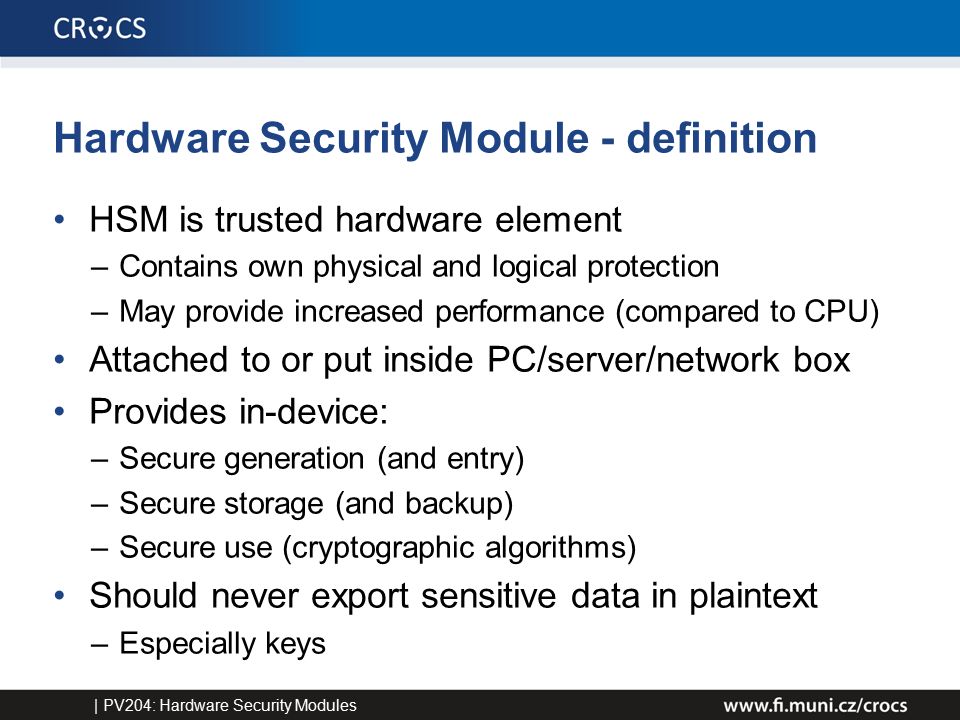
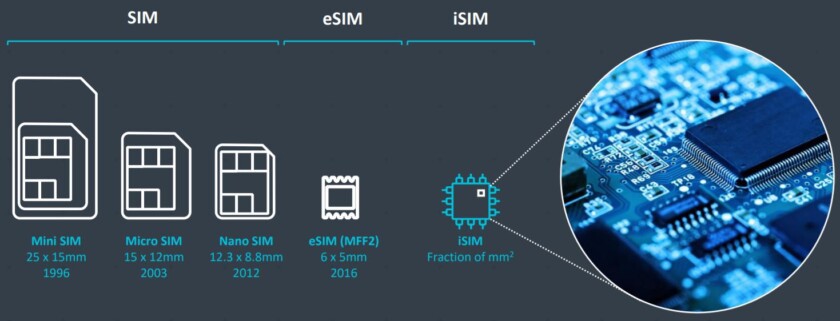
Threats to ICT supply chains including Counterfeit electronic components and Hardware Trojans present critical risk to military and security systems

Information and communications technology, encompassing digital services and infrastructure, cybersecurity and software, is ubiquitous throughout the economy and society. As the digital transformation gathers pace, the number and complexity of ICT services is accelerating. Information and Communications Technology (ICT)…...