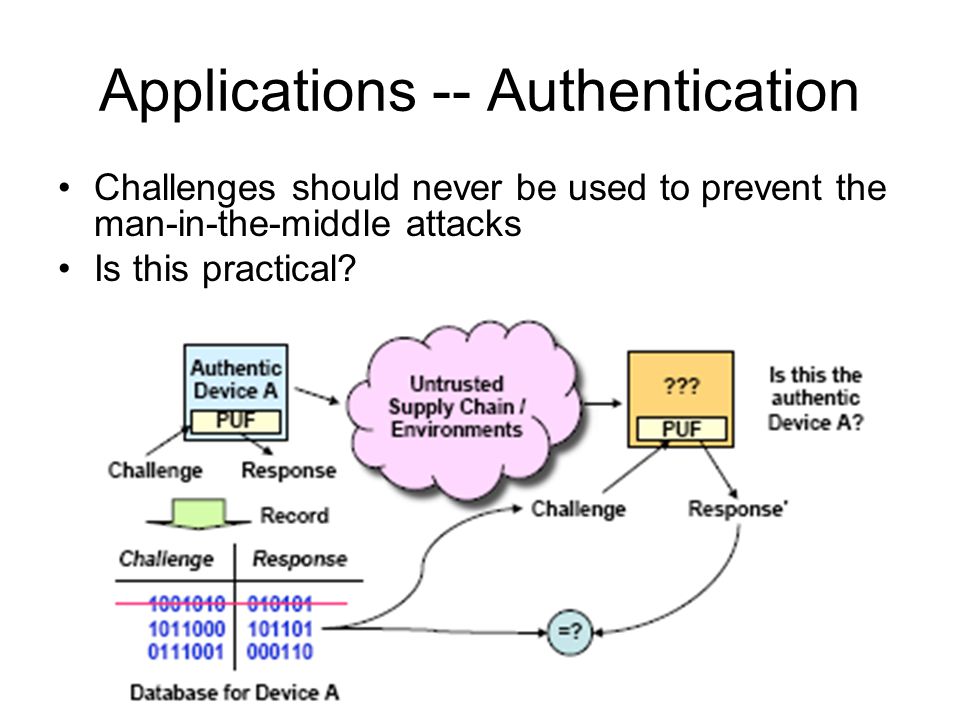
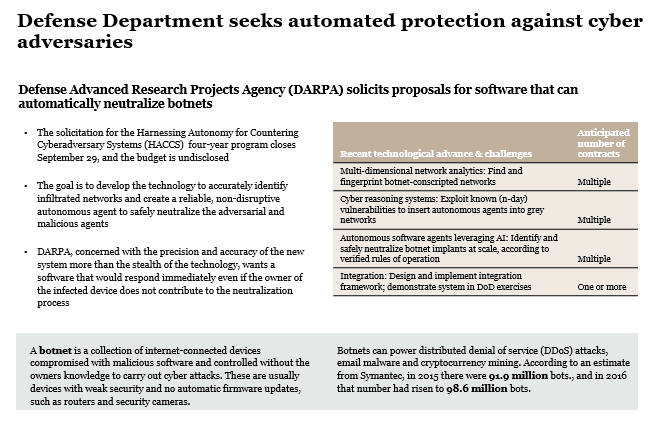
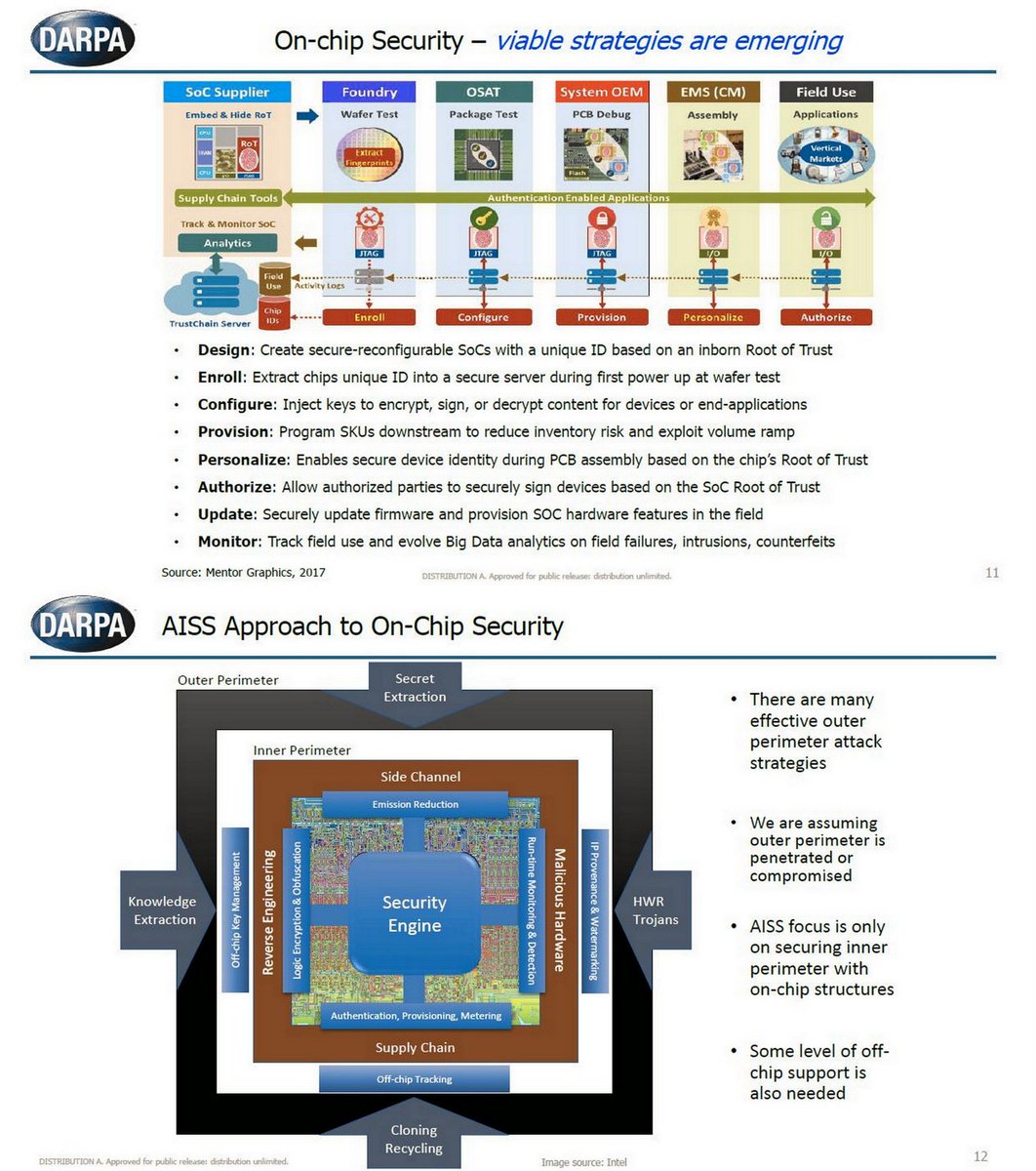
DARPA GRIT program developing compact, tunable Gamma ray source for advanced accelerator technology, high-energy laser systems, and new x-ray and gamma ray detectors

Gamma rays are ionizing electromagnetic radiation, obtained by the decay of an atomic nucleus. Gamma rays are given off by stars, and by some radioactive substances. Gamma-rays travel to us across vast distances of the universe, only to be absorbed by…...