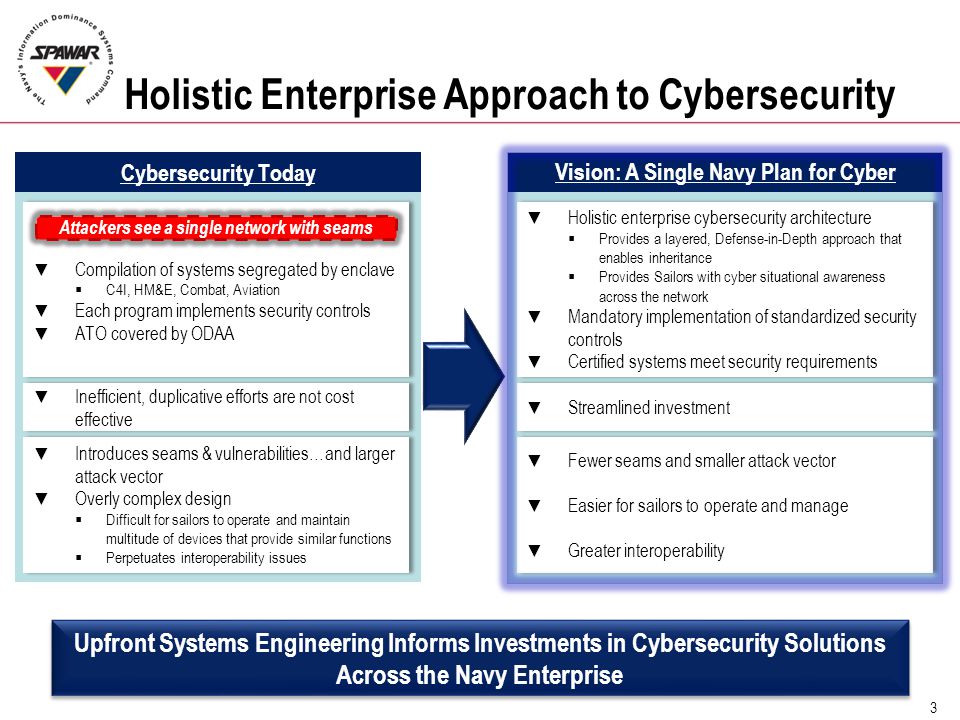
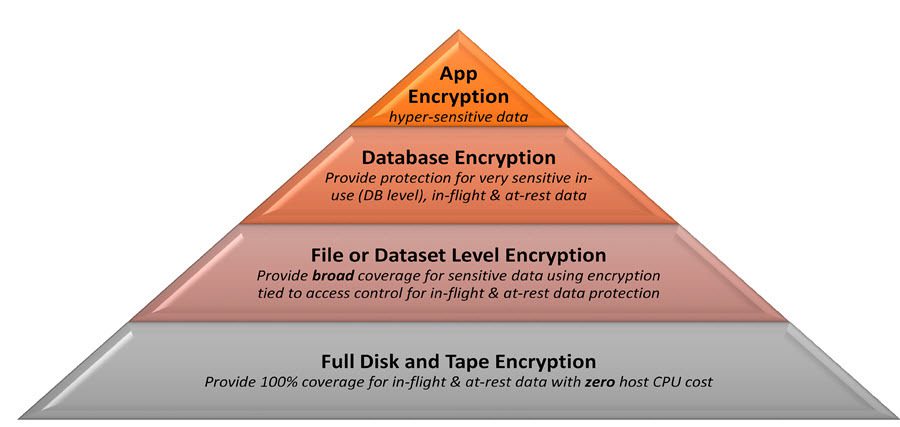
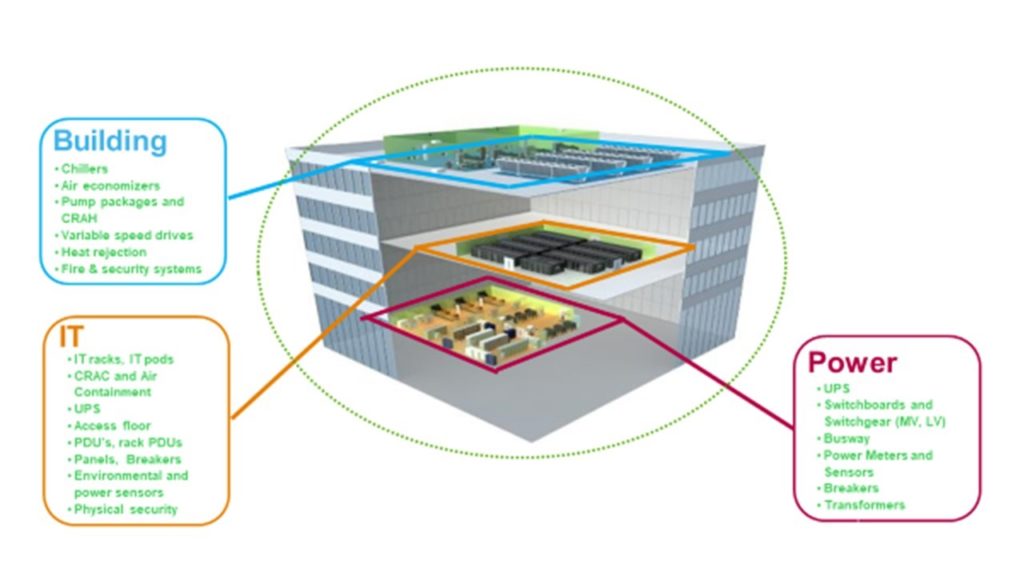
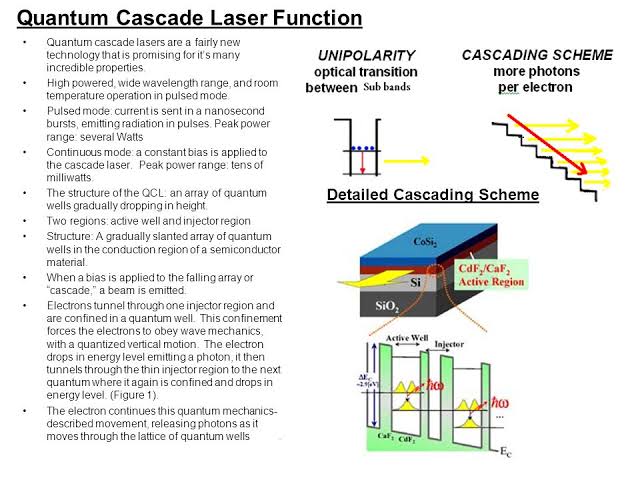
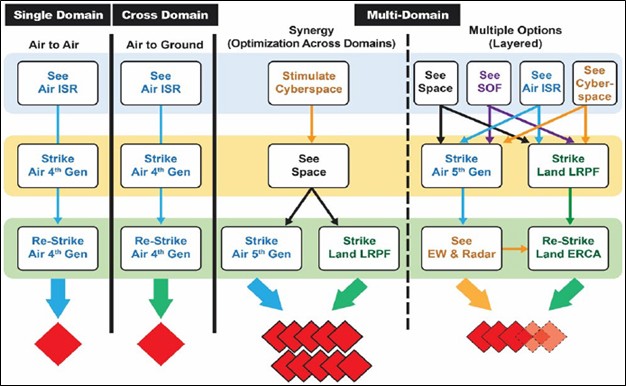
DARPA OPS-5G to mitigate security threats facing 5G and future wireless networks in military appliations
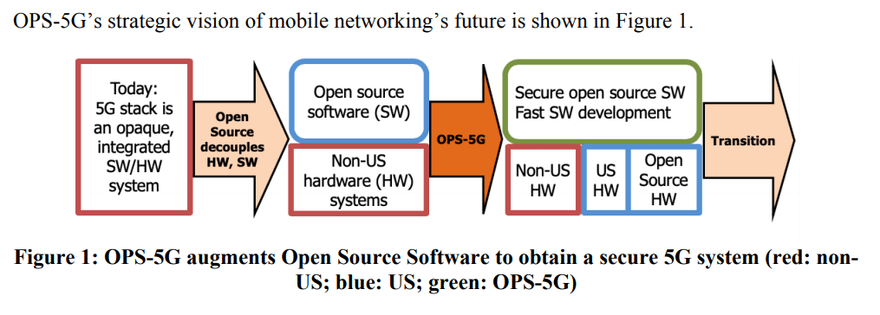
5G is the latest in a series of evolutions in public mobile networking, with widespread coverage and access on a subscription basis. 5G networks are characterized by improved capabilities across a variety of measures, including throughputs, latencies, numbers of devices,…...