Photoacoustic Imaging enable Seeing Through Solids, hackproof Biometrics and Image Underwater Objects
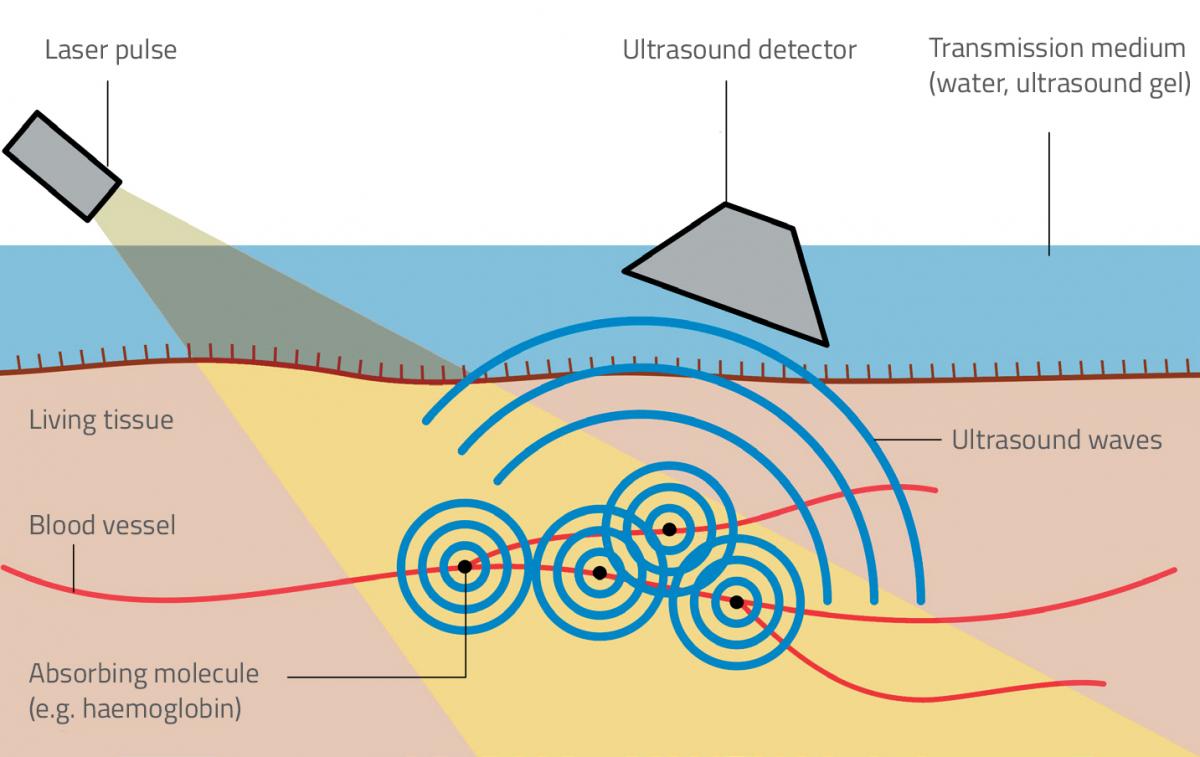
Alexander Graham Bell discovered photoacoustics by accident when he was working on the development of the photophone, a followup to his recently developed telephone that operated via modulated sunlight instead of electricity. You would operate a photophone by speaking into its…...