Rising DNS attacks require DNS security measures and Protective DNS says Joint NSA and CISA Guidance
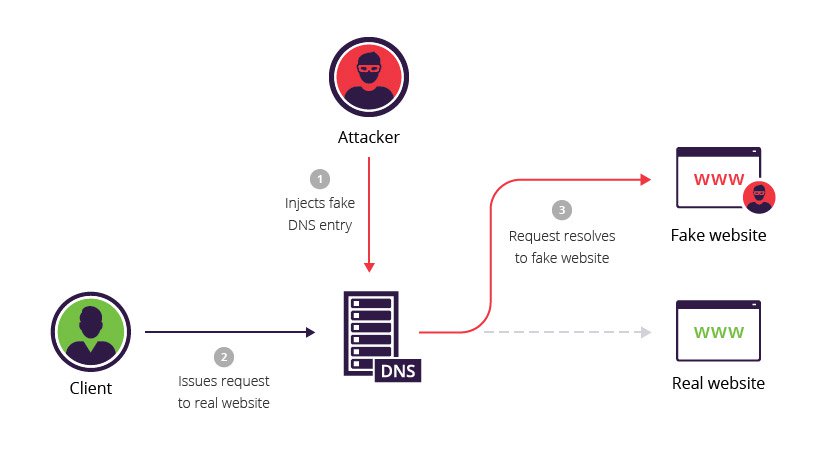
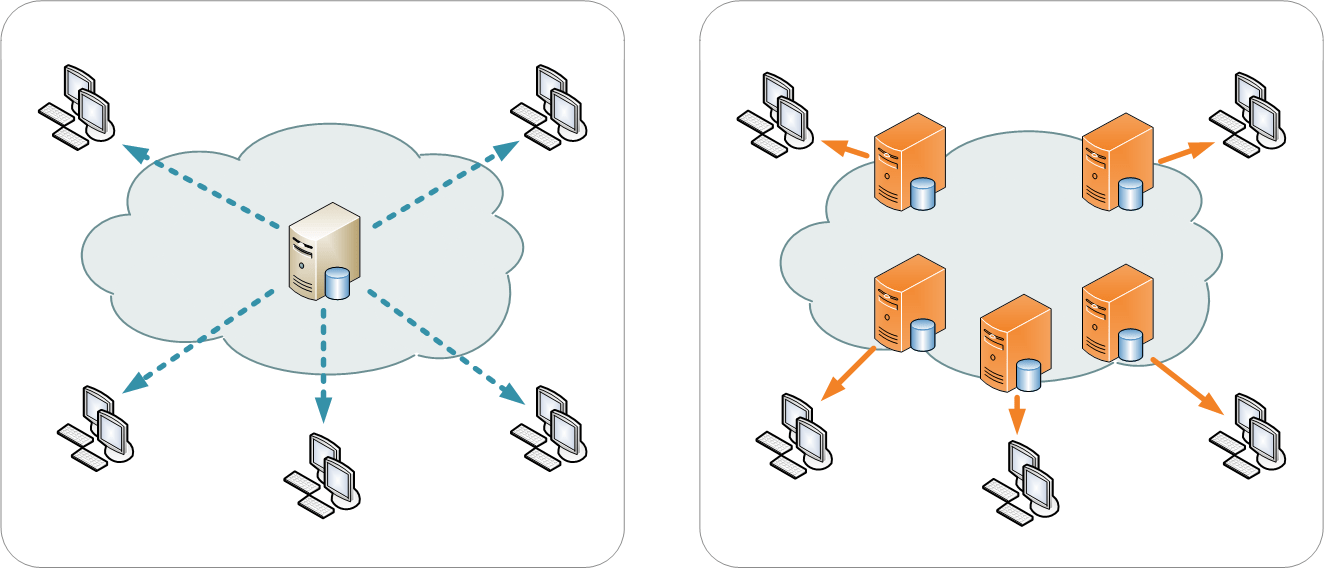
The Domain Name System (DNS) is central to the operation of modern networks, translating human-readable domain names into machine-usable Internet Protocol (IP) addresses. Email services, chat services and even social networks rely on DNS to work 24 hours a day,…...