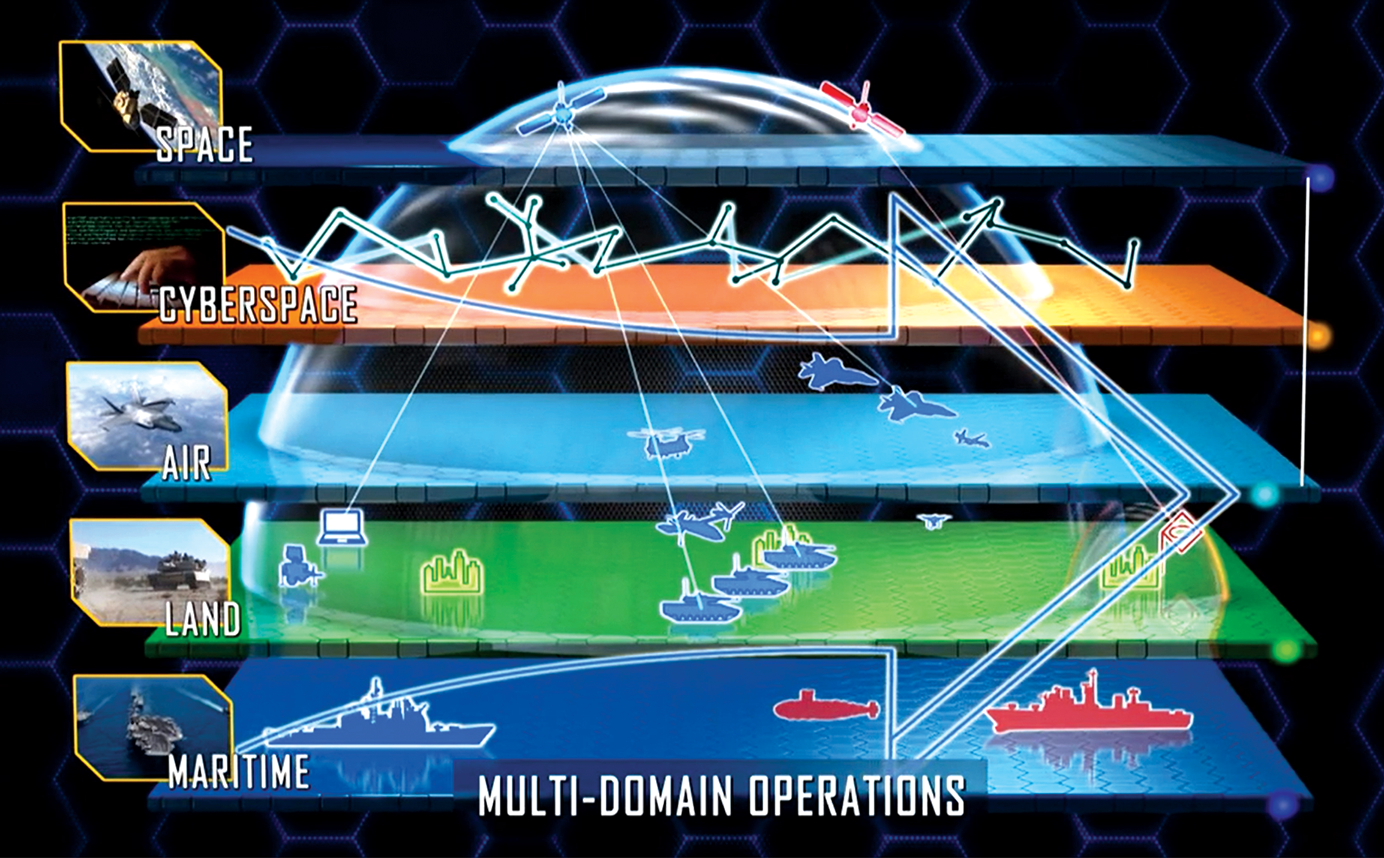
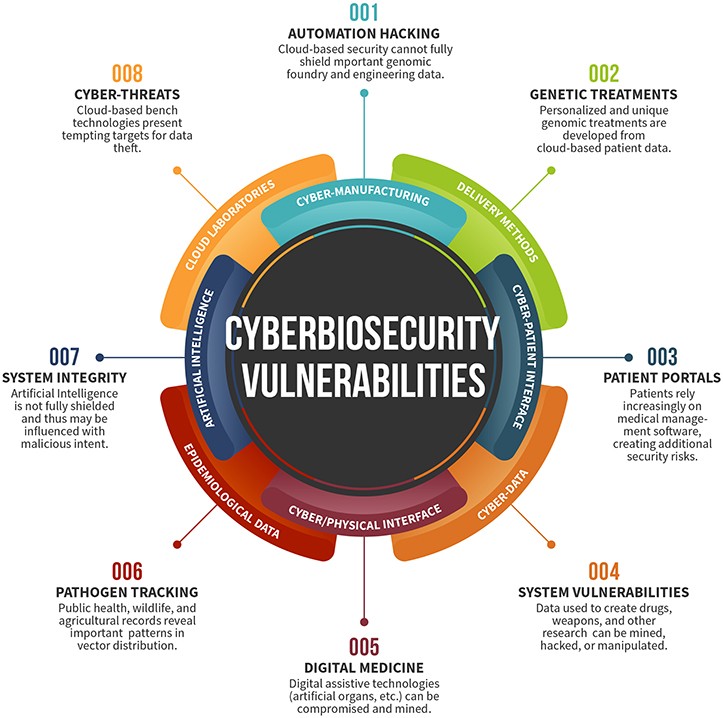
USSOCOM Special Operations Forces technology requirements to support counterterrorism, crisis response to high-end conflicts

Special operations (S.O.) are military, law enforcement or intelligence operations that are “special” or unconventional and carried out by dedicated special forces and other special operations forces units using unconventional methods and resources. Special operations may be performed independently, or…...