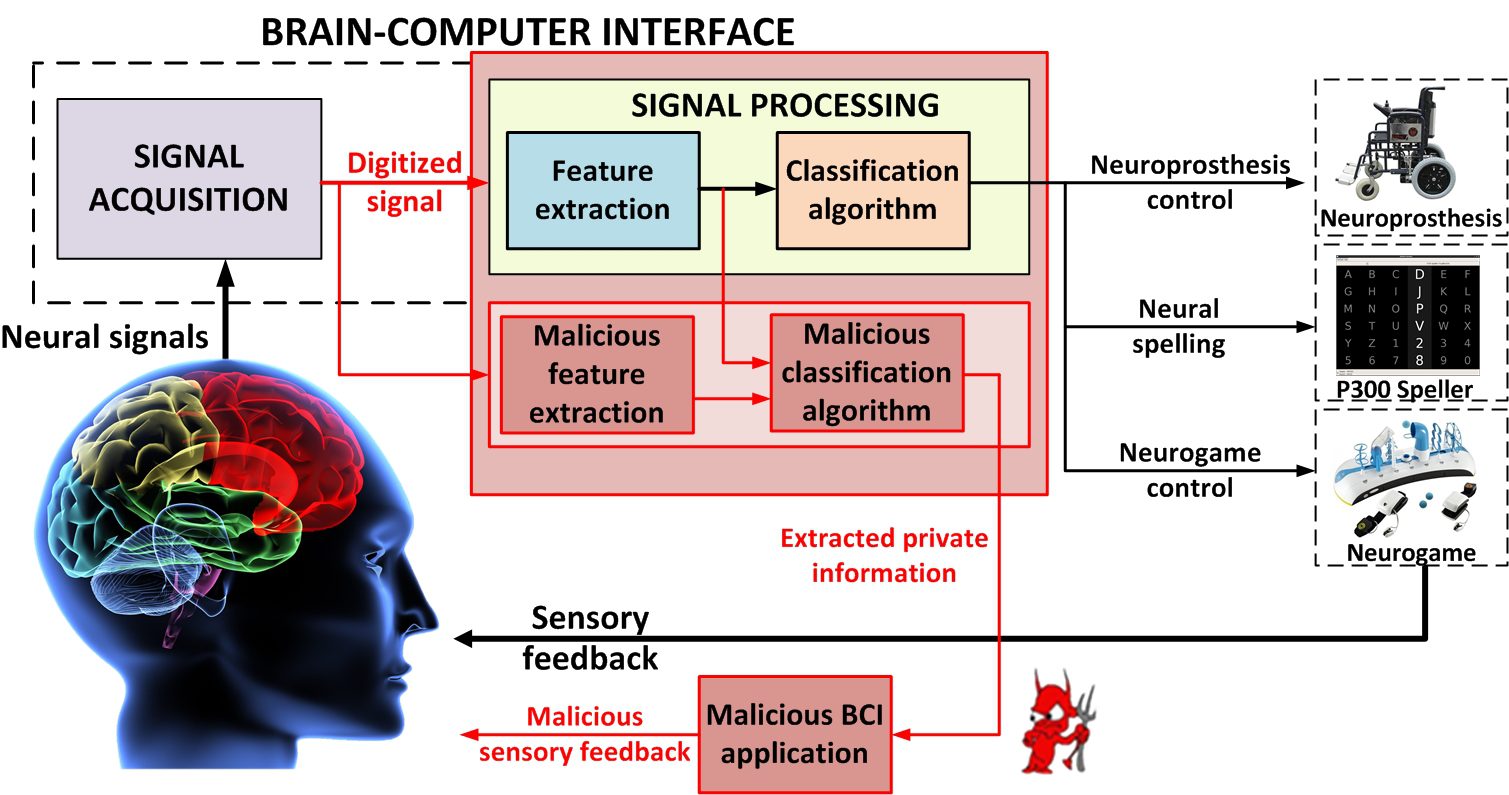
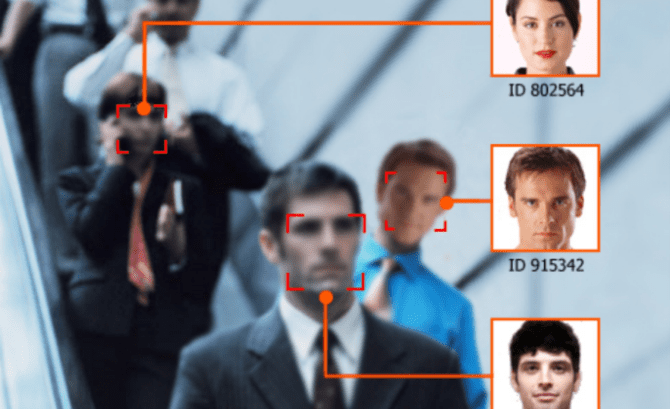
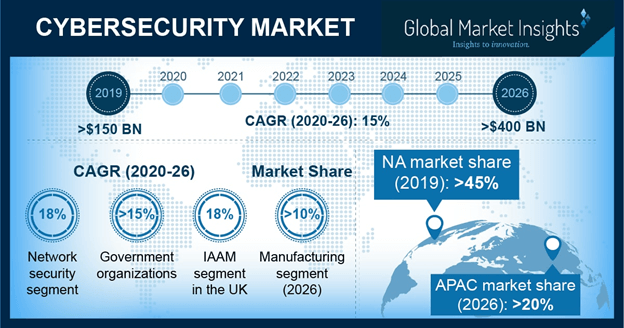
DARPA EVADE to improve the cybersecurity of Military IoT/embedded devices
By 2025, it is predicted that there can be as many as 100 billion connected IoT devices or network of everyday objects as well as sensors that will be infused with intelligence and computing capability. These devices shall comprise of…...