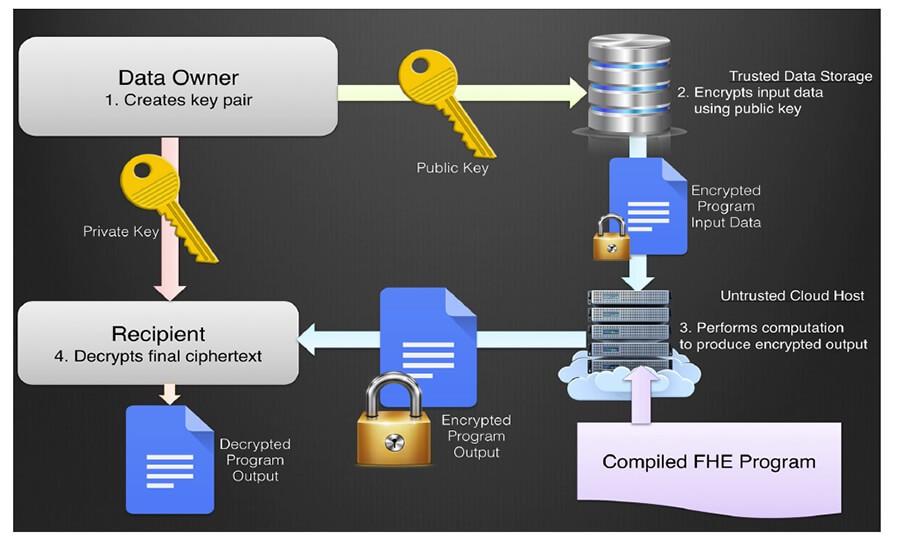
The Next Frontier in Encryption: Homomorphic Encryption the Future of Secure Computation

Businesses, large and small, are embracing the Cloud. No matter which research company, vendor or expert you consult, everyone agrees that about four in every five enterprise workloads are either already in the Cloud or will be within the next…...