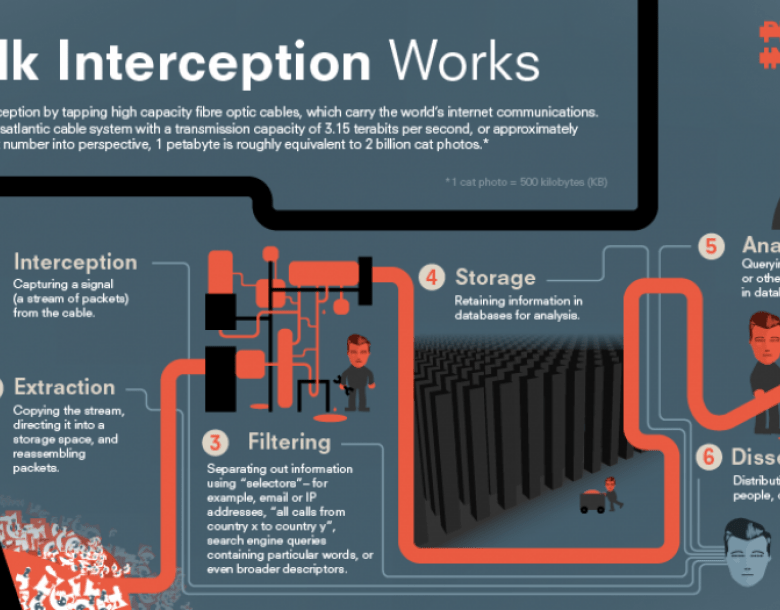
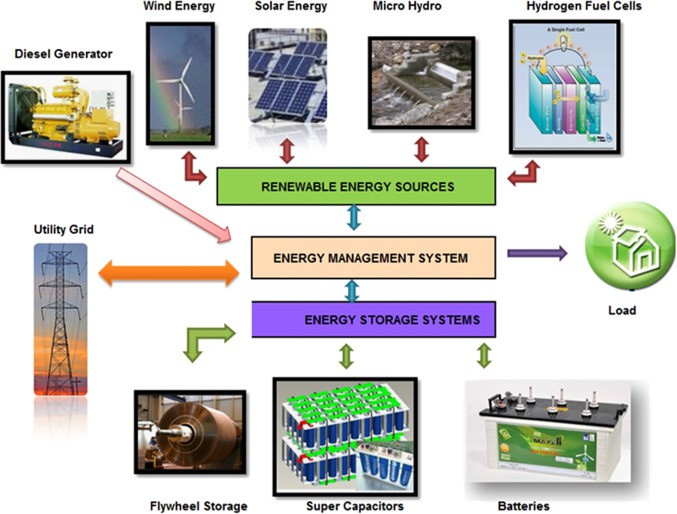
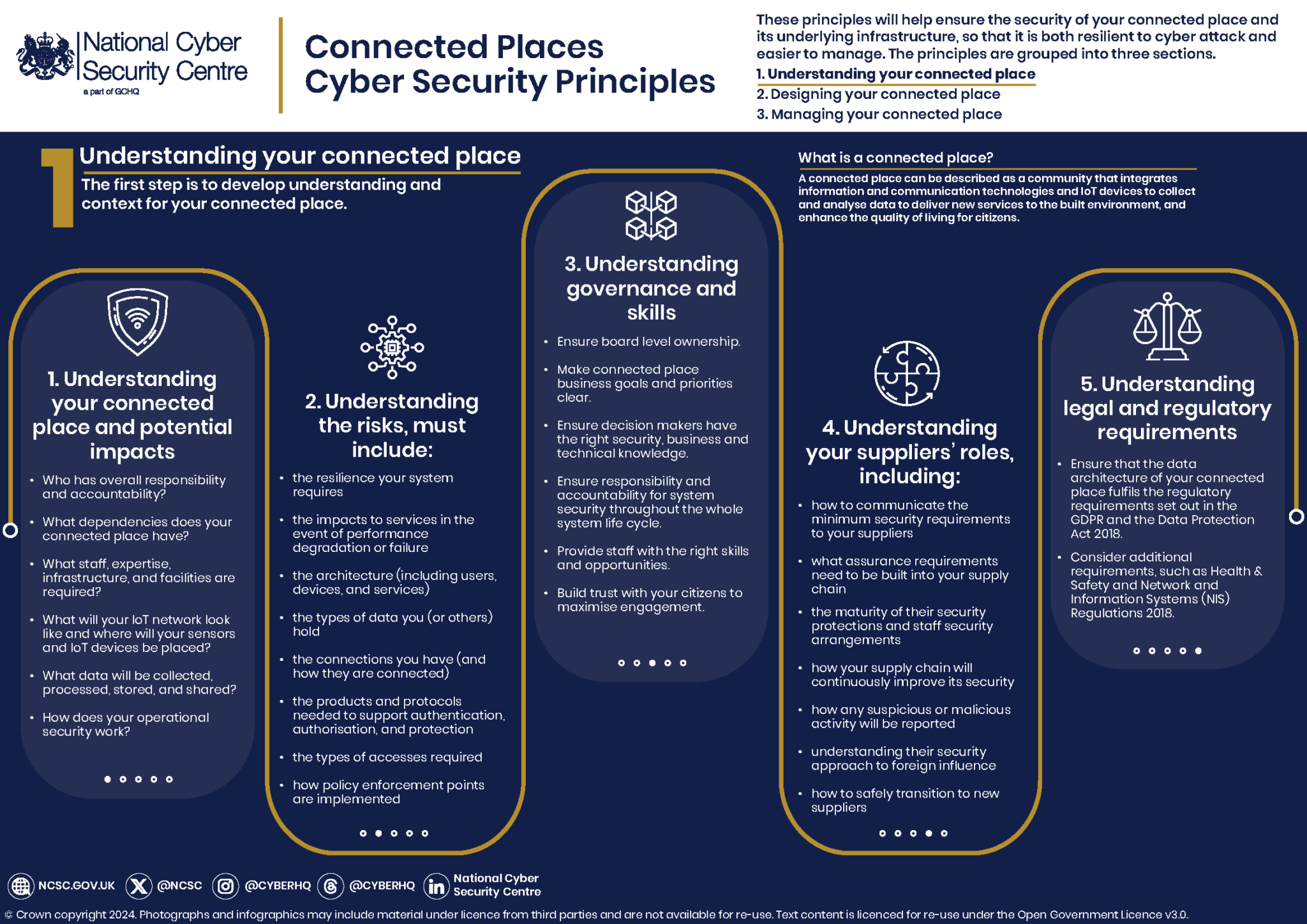
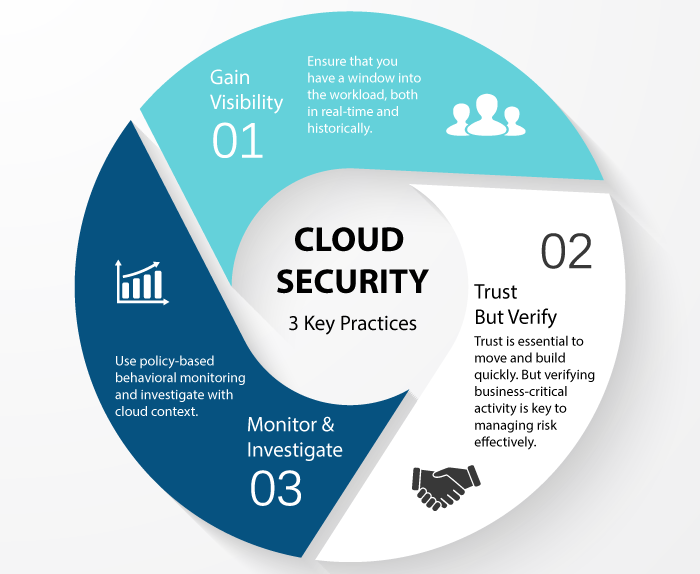
The Rise of Unmanned Surface Vehicles (USVs): Transforming Naval Warfare

Unmanned Surface Vehicles (USVs) are revolutionizing how we explore and protect our oceans. These autonomous vessels, operating at or near the sea surface without any onboard operators, are increasingly being employed across various sectors. From monitoring marine life to enhancing…...