Small Modular Reactors (SMRs) on Floating Ships: A New Era of Energy for Coastal Nations
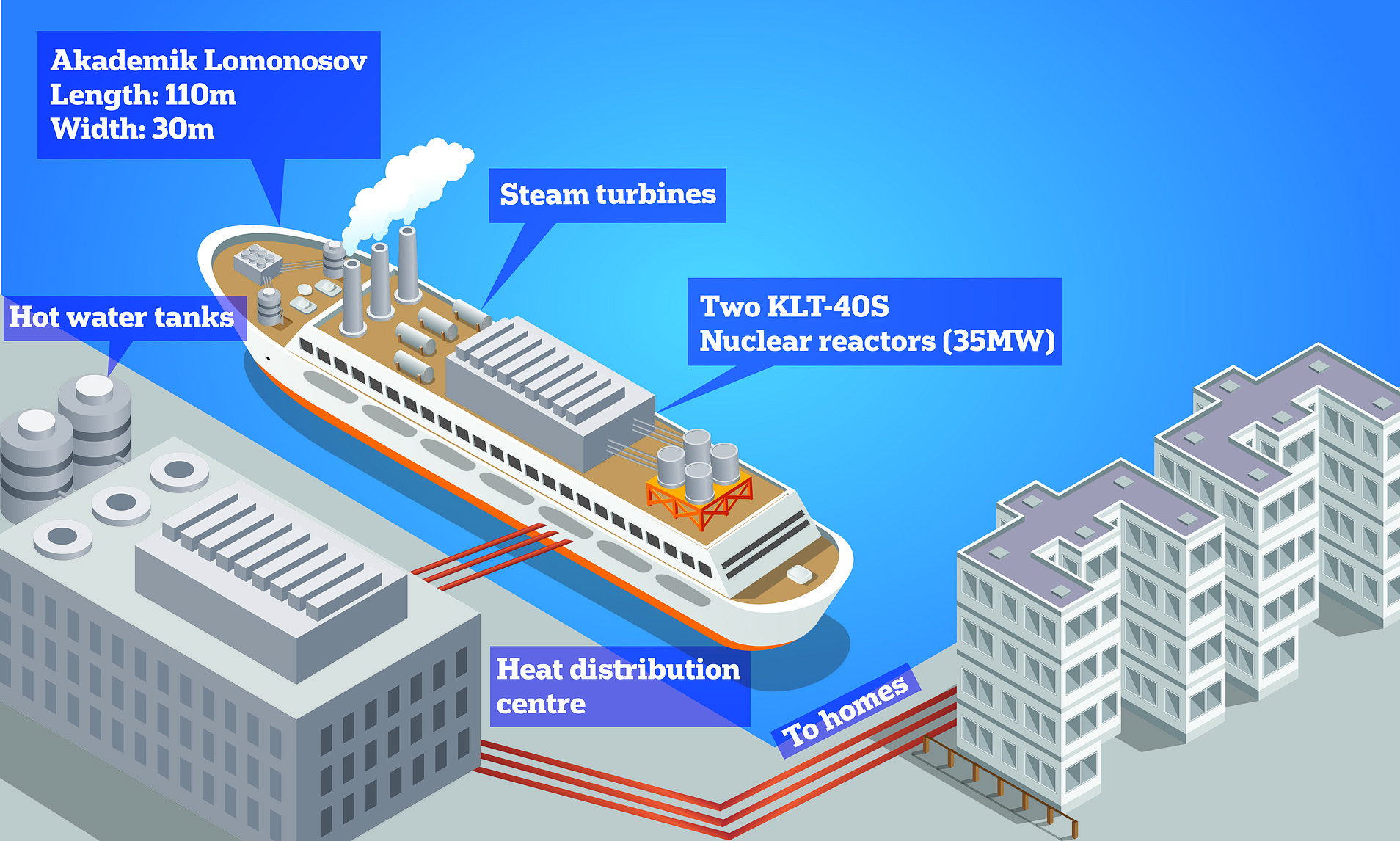
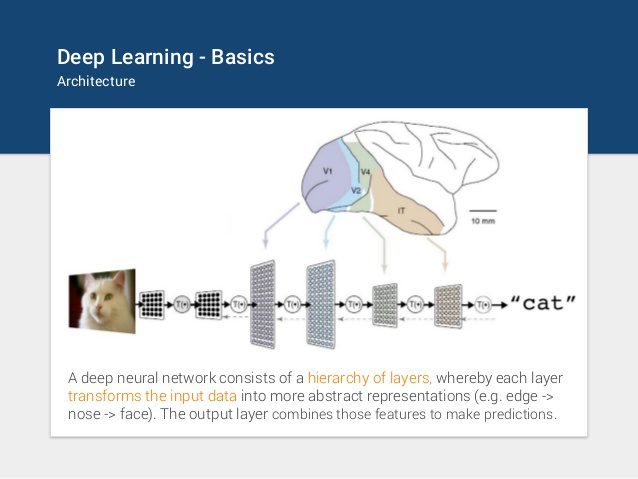
As global energy demand surges and the transition to cleaner, low-carbon sources intensifies, a groundbreaking solution is emerging: Small Modular Reactors (SMRs) deployed on floating ships. Small Modular Reactors (SMRs) offer scalable, cost-effective nuclear energy with enhanced safety features, reduced…...