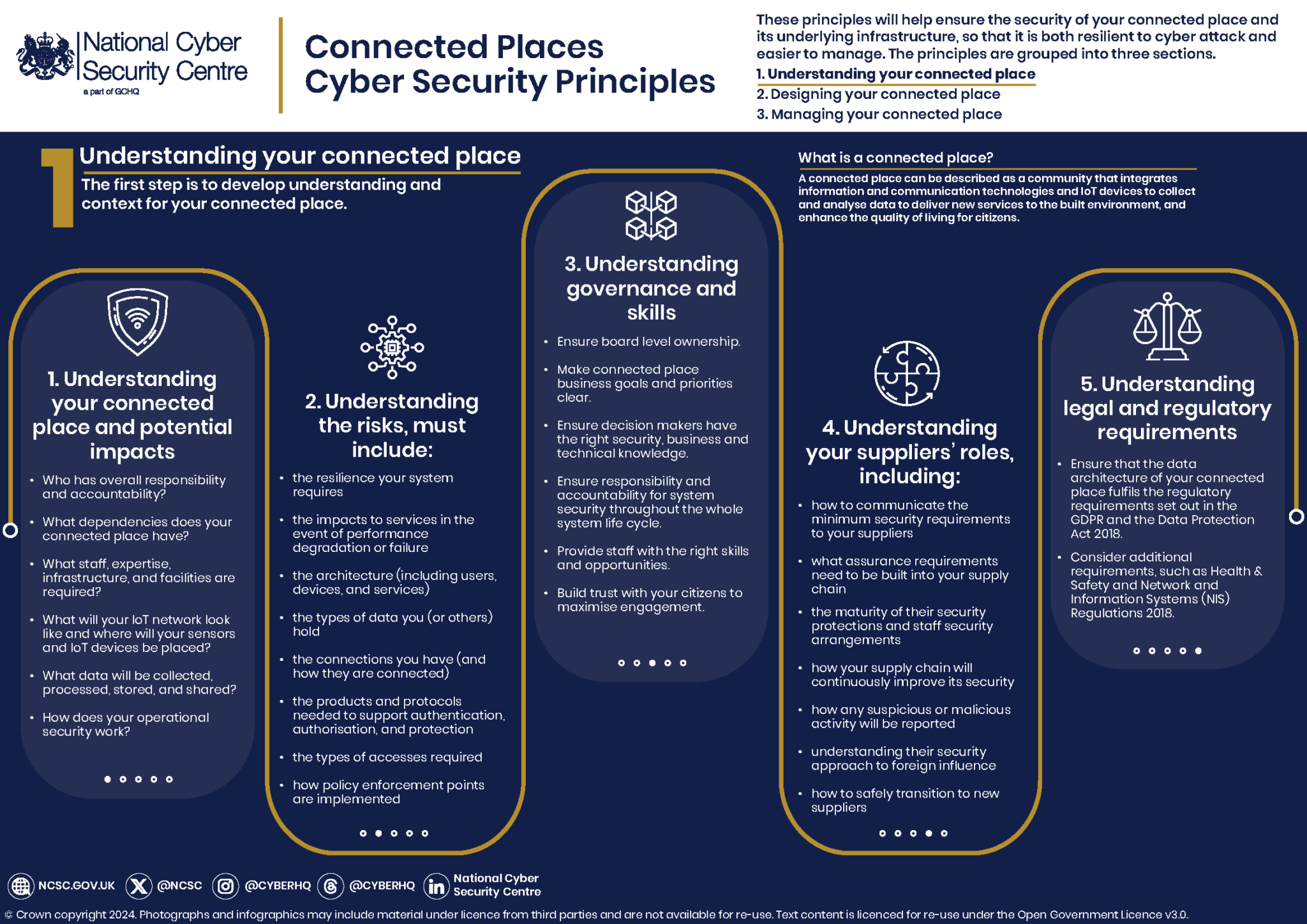
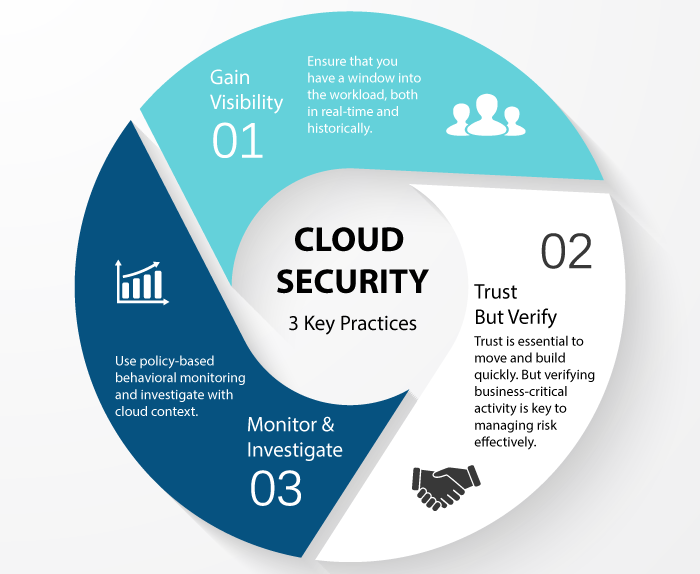
Bolstering National Security: Addressing Vulnerabilities in the U.S. Defense Industrial Base

As global tensions rise, the U.S. Defense Industrial Base (DIB) finds itself grappling with a range of escalating supply chain risks, particularly those emanating from China. These risks are not confined to the availability of raw materials and components but…...