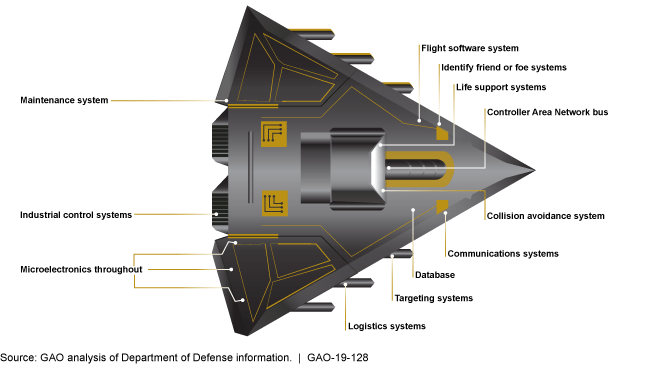
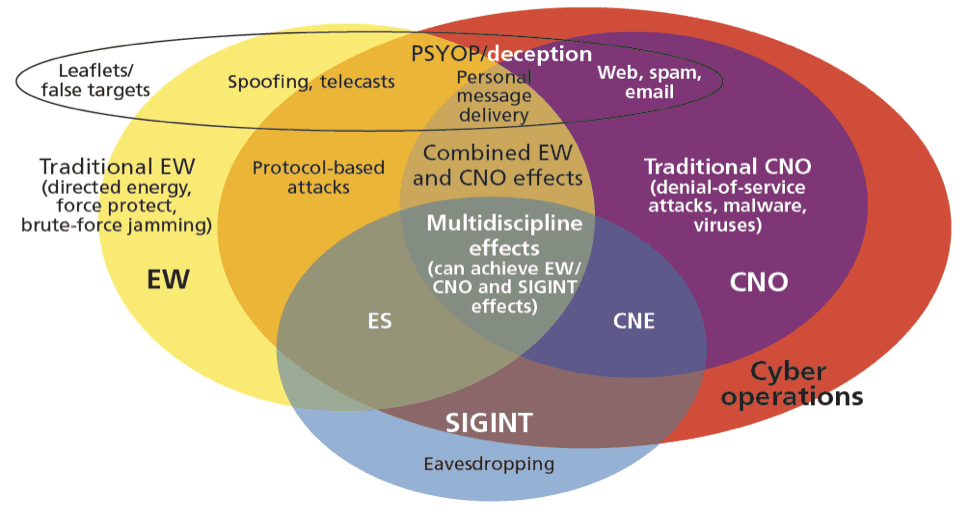
DARPA AI Cyber Challenge Aims to Secure Nation’s Most Critical Software
DARPA’s AI Cyber Challenge: Harnessing Artificial Intelligence to Secure Critical Infrastructure DARPA launches AIxCC to revolutionize software security, leveraging AI to defend open-source code and critical national systems. In today’s rapidly evolving digital landscape, where software forms the backbone of…...