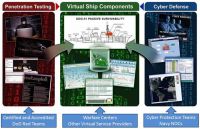
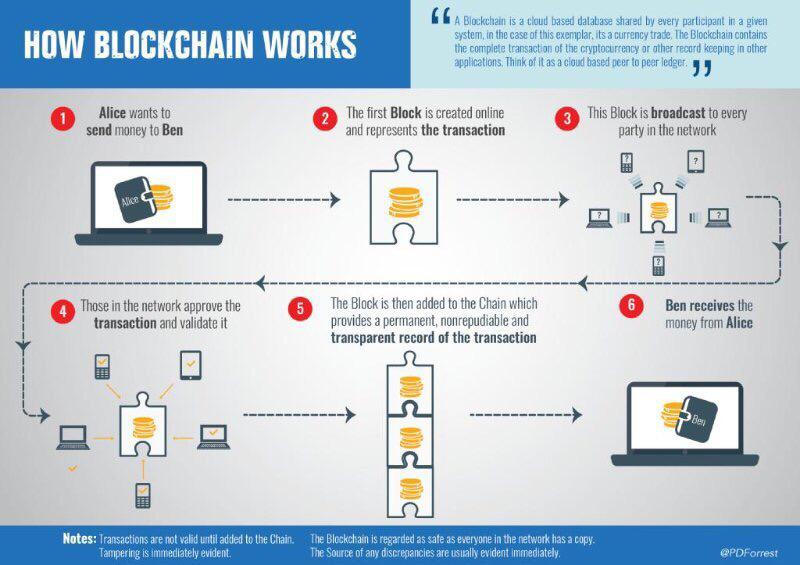
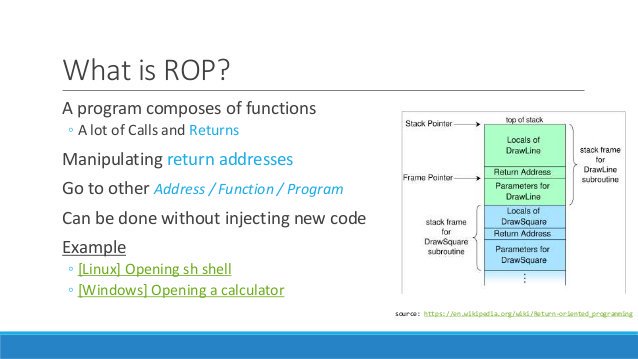
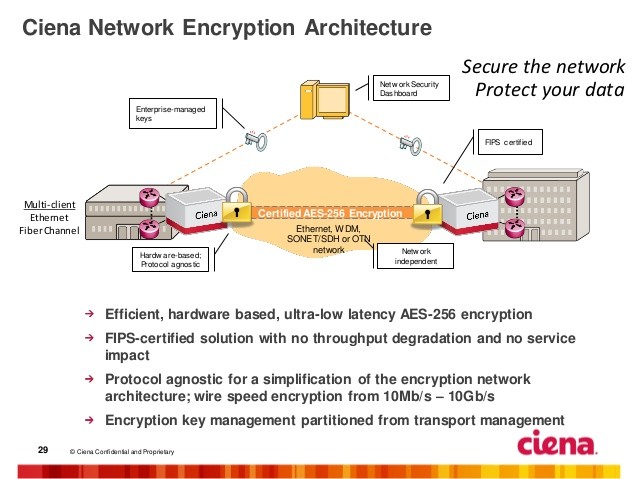
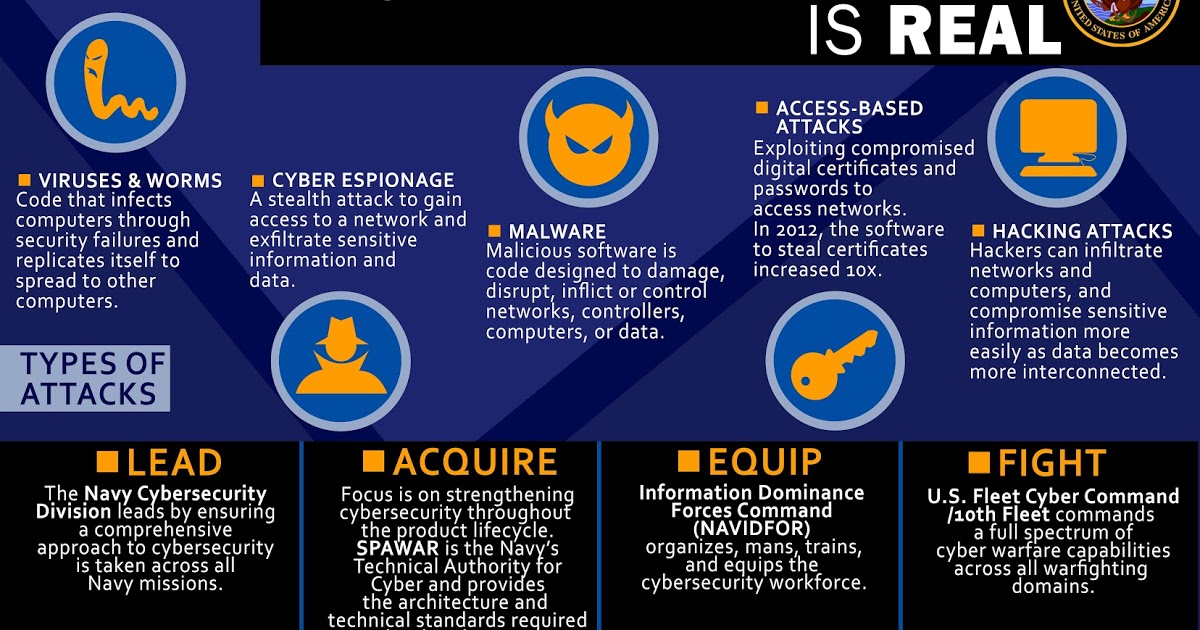
DARPA GAPS program developing hardware and software architectures that can provide physical security like air-gaps
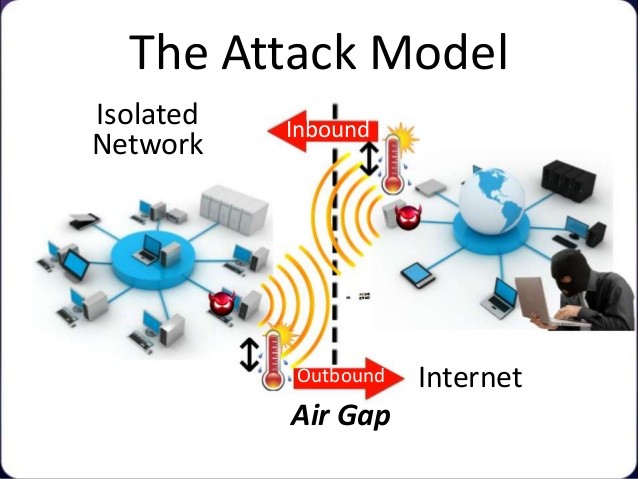
Today, modern computing systems are incapable of creating sufficient security protections such that they can be trusted with the most sensitive data while simultaneously being exposed to untrusted data streams.” “Therefore, for the most sensitive computing systems, [the Department of…...