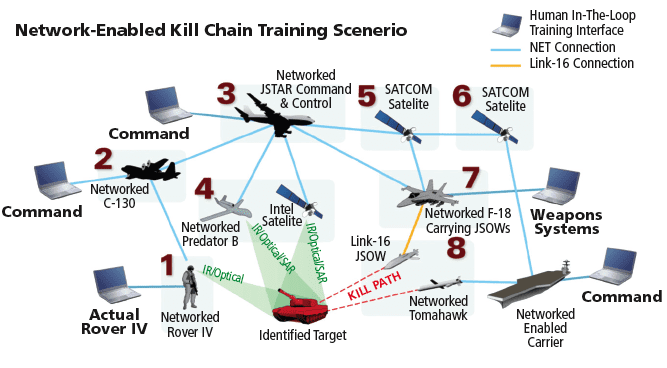
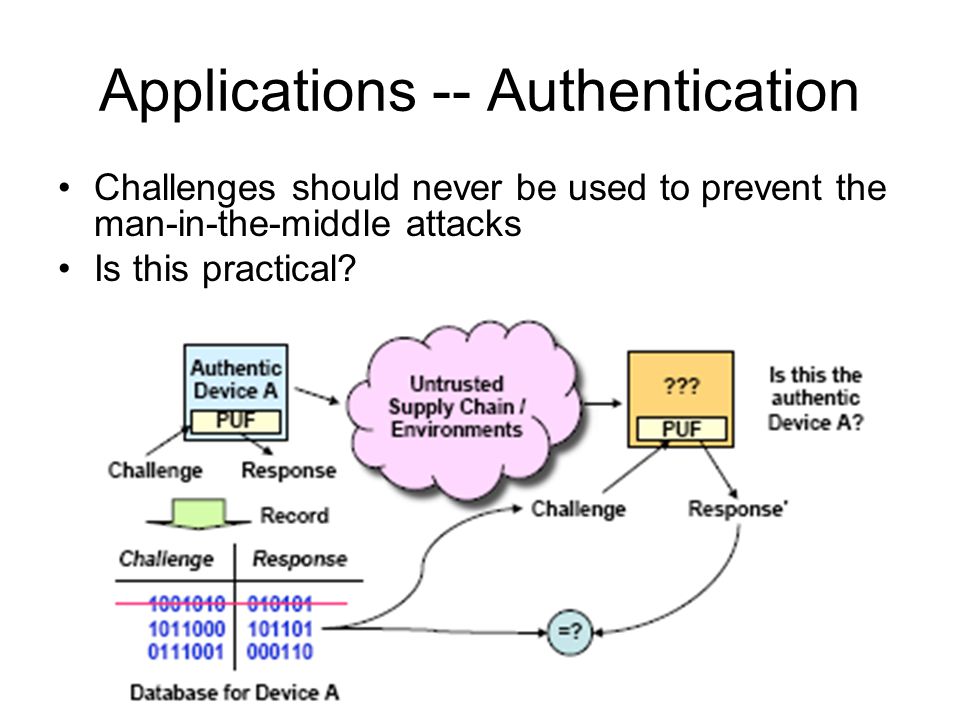
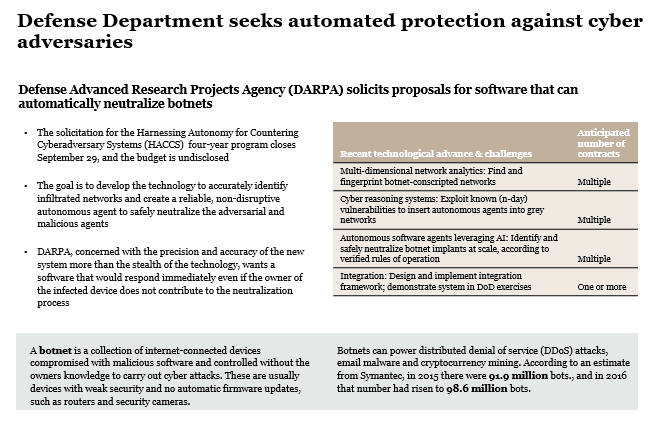
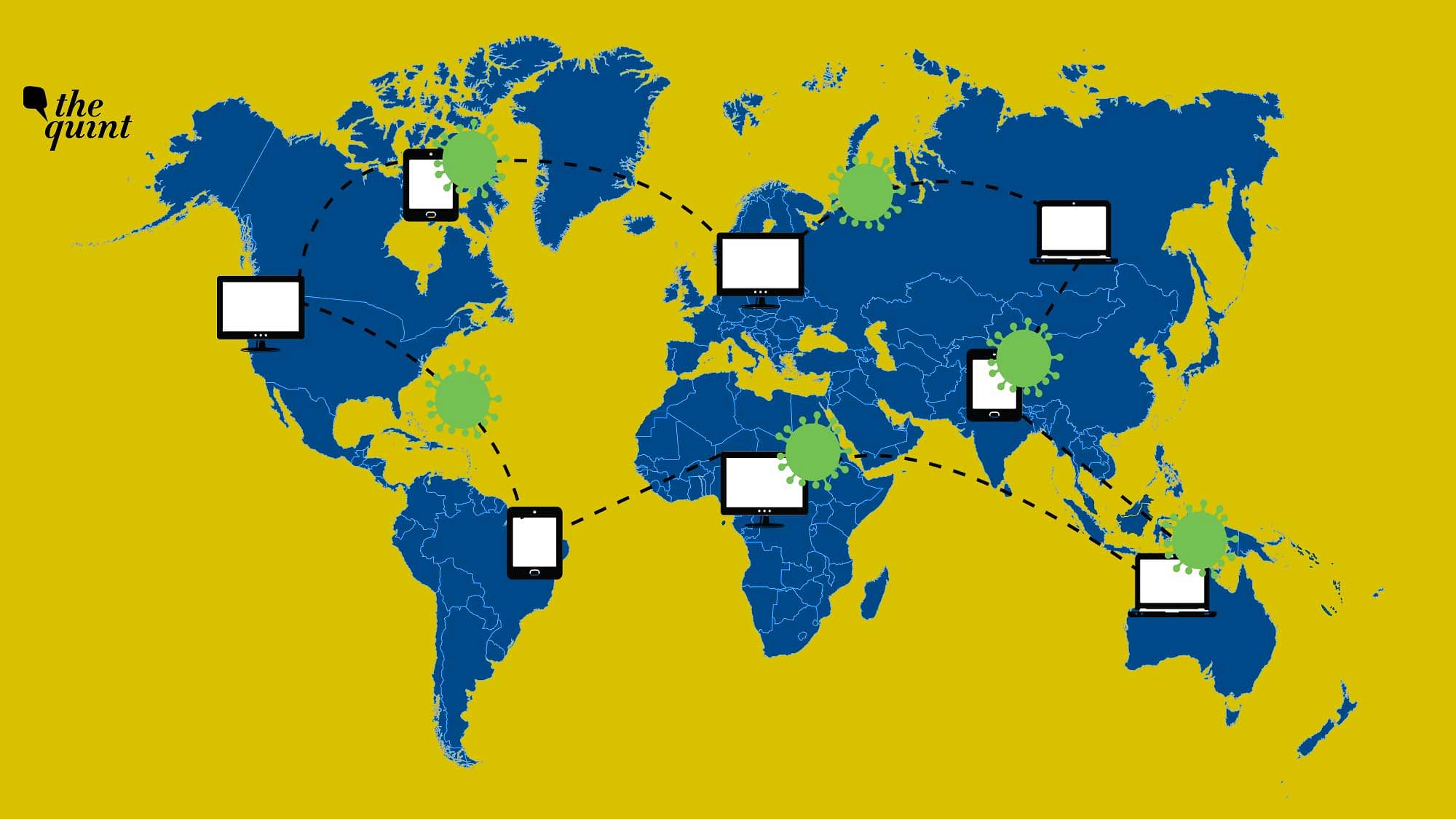
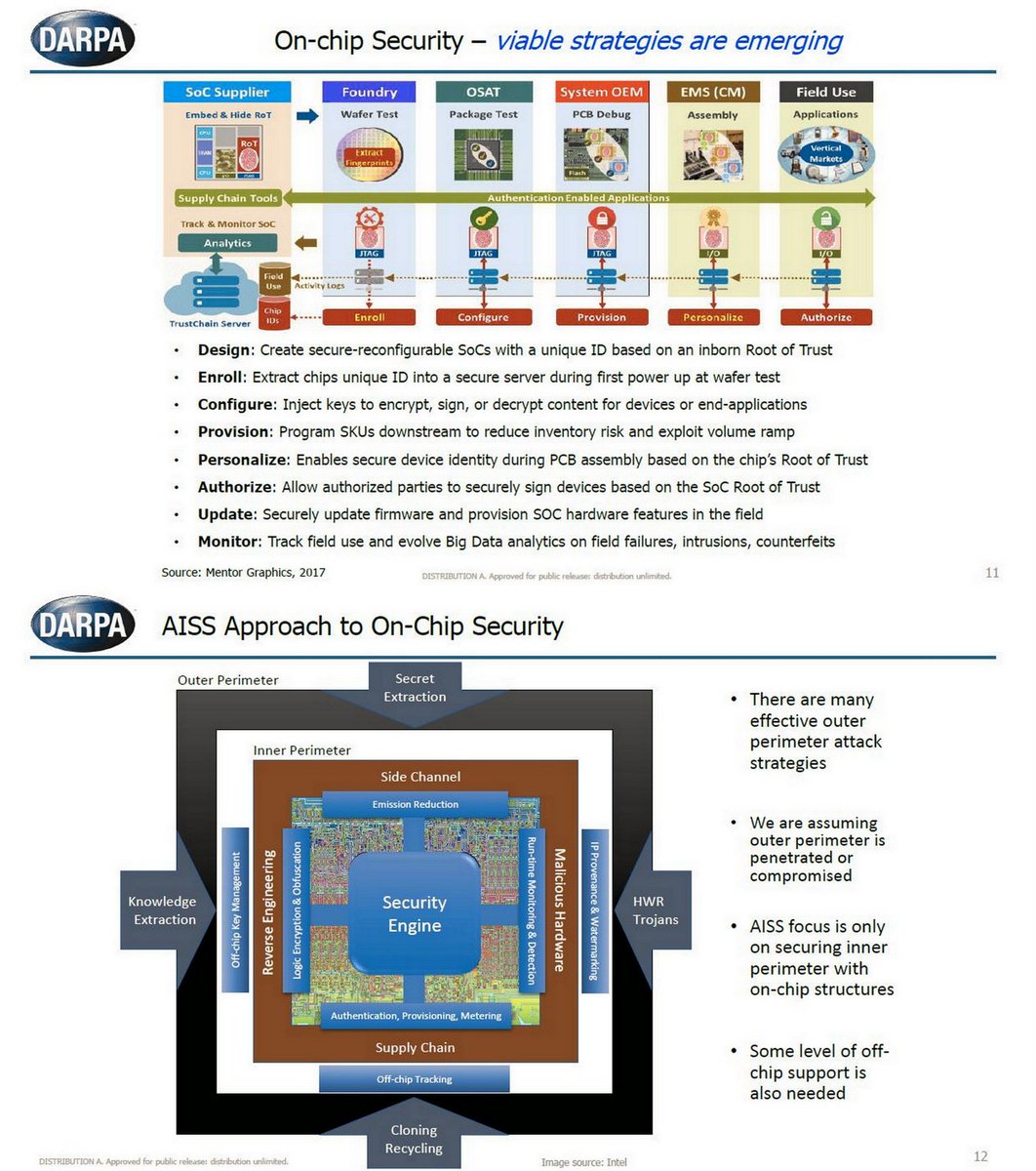
Smart home devices have many security risks and threats to be exploited by hackers and Intelligence agencies for mass surveillance
The rise of the digital era has brought with it many wondrous changes to our daily lives, not least of which the fact that we now carry digital assistants with us everywhere we go in the form of smartphones, tablets,…...