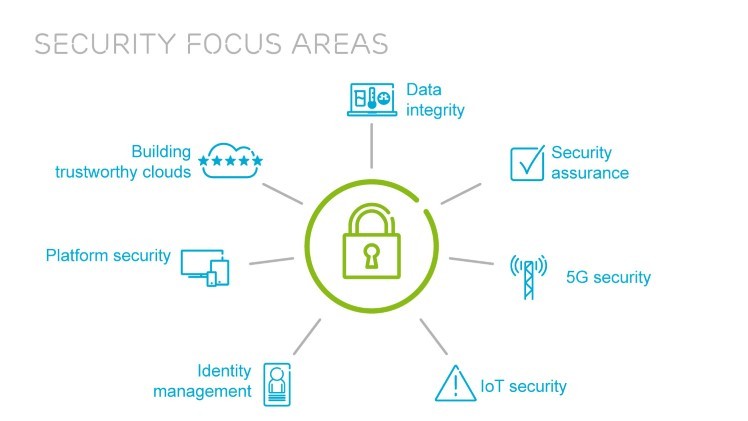
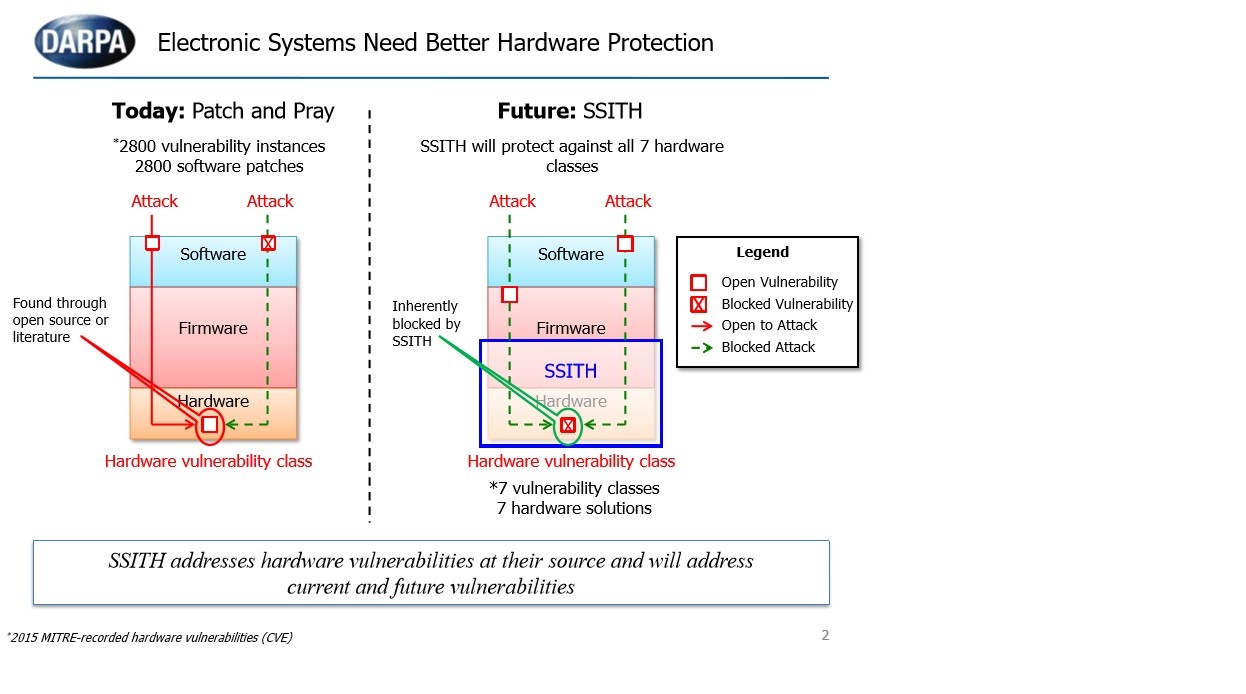
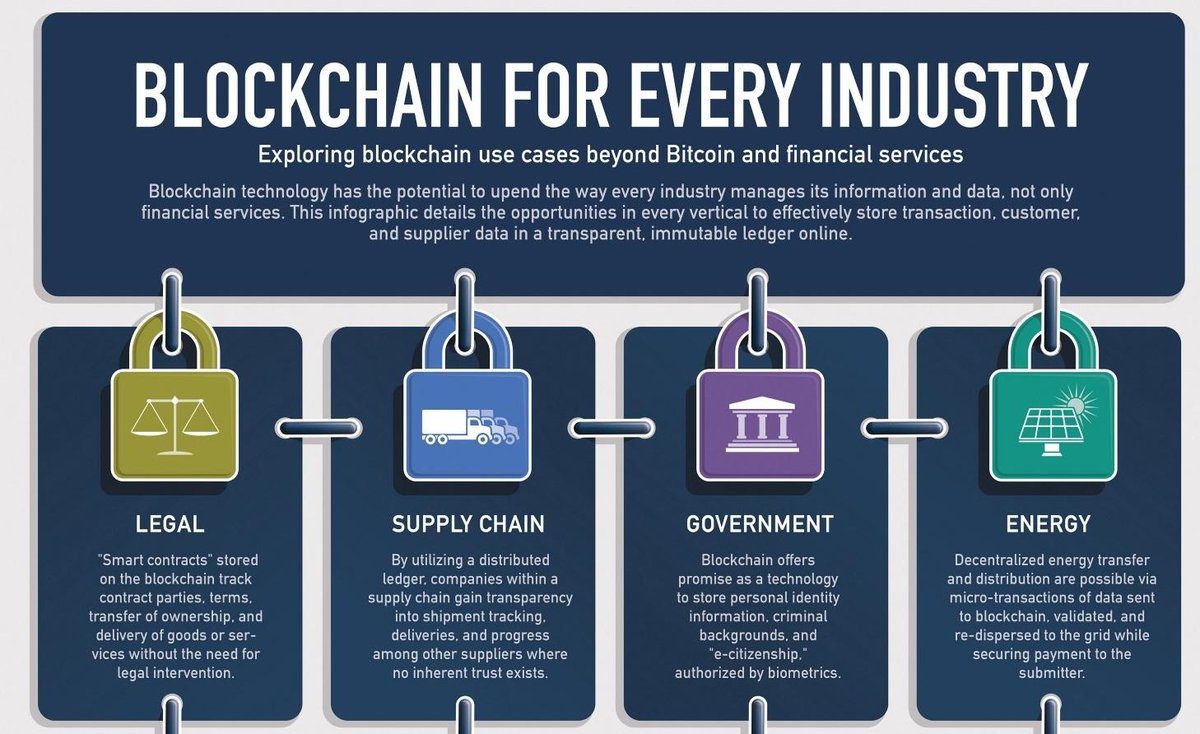
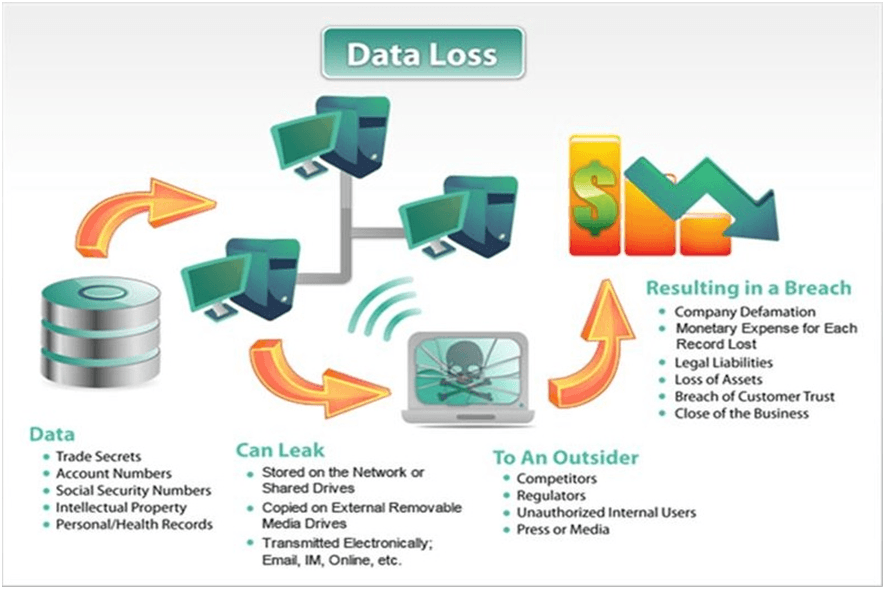
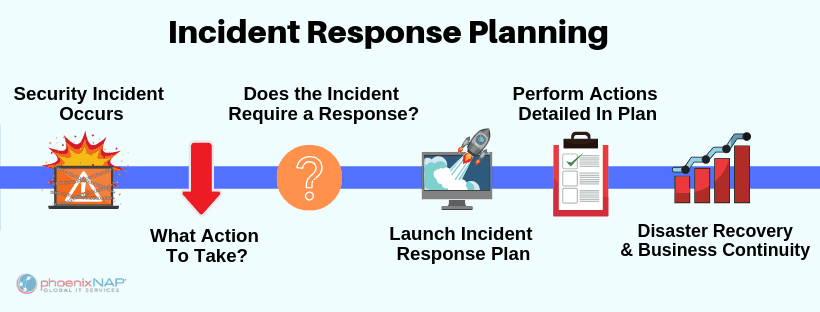
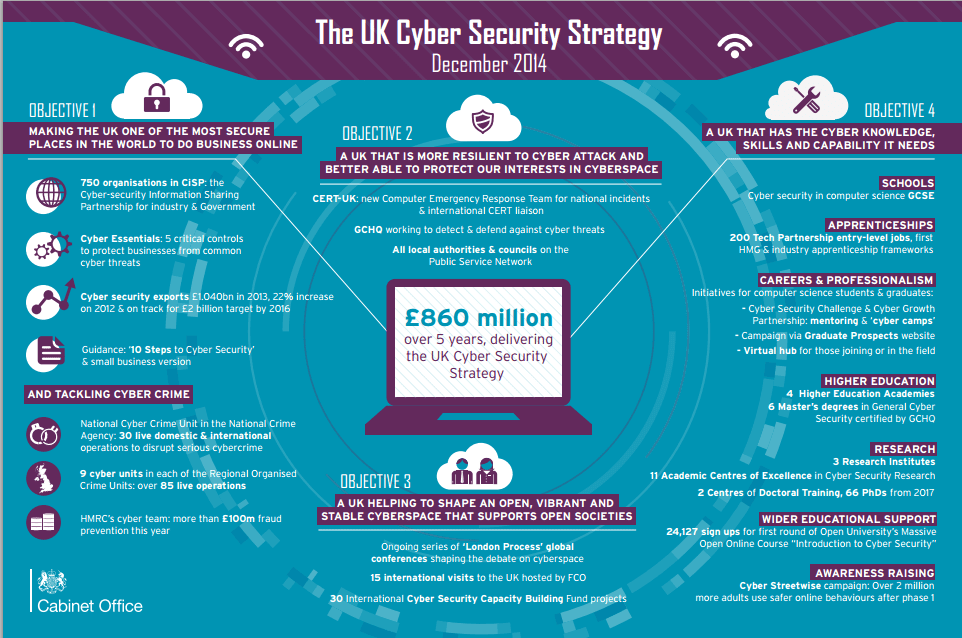
UK Cyber Security Strategy emphasizes Defence , Deterrence and Cyber technology development
The rapid development of digitalized services and online shopping in the UK has been paralleled with significant growth in cybercrime, leading to greater spending on security in public and private sectors. Organizations’ IT footprints have also become increasingly complex, driving…...