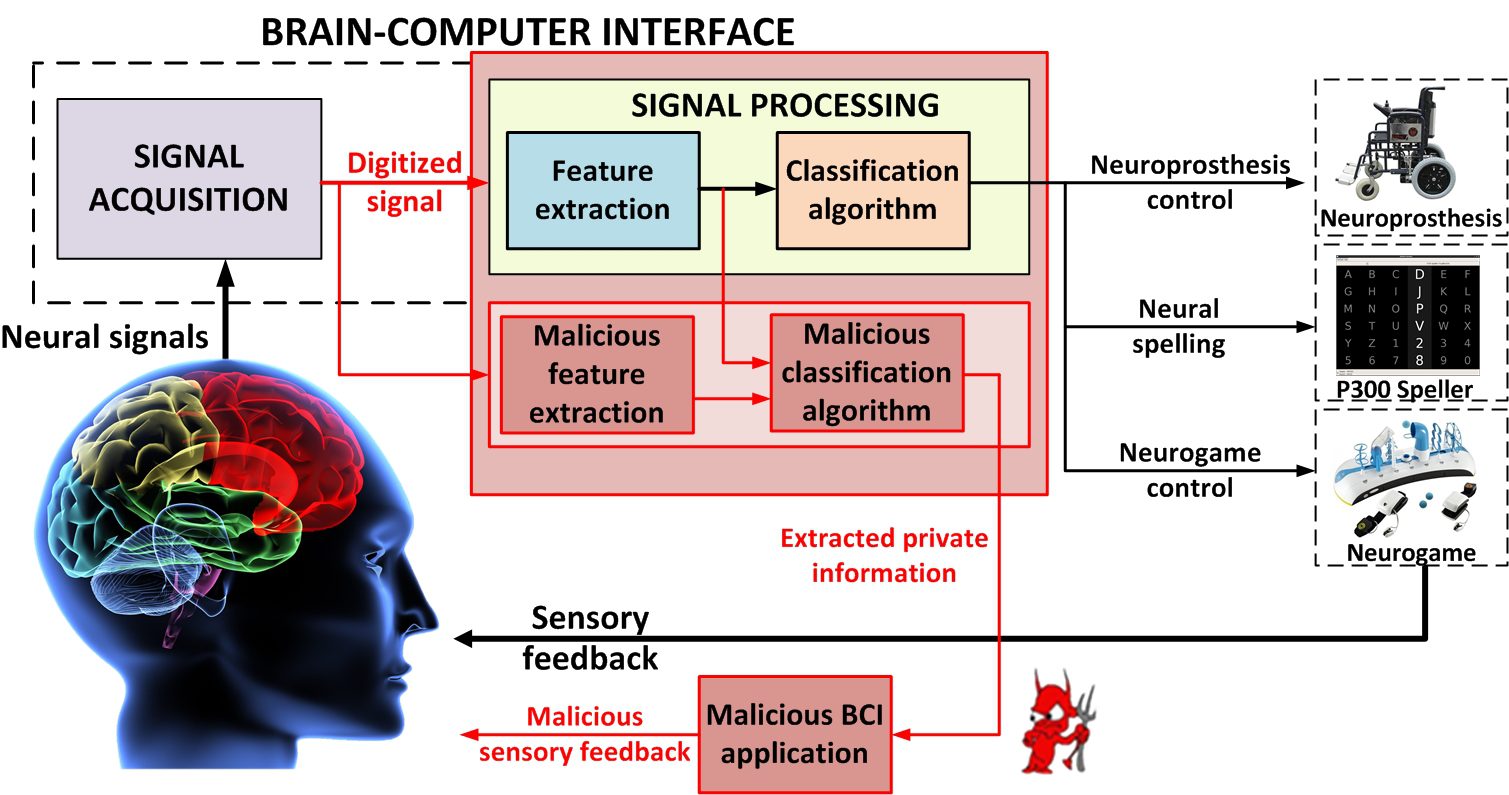
DARPA SMOKE to automate cyber red teaming or penetration testing to uncover military systems vulnerabilites

Cyberattacks are being conducted daily on any type of target, and any notion that a state of full cyber security can be reached is a mere illusion. Cybersecurity is about managing risks and to ascertain that, to a certain extent,…...