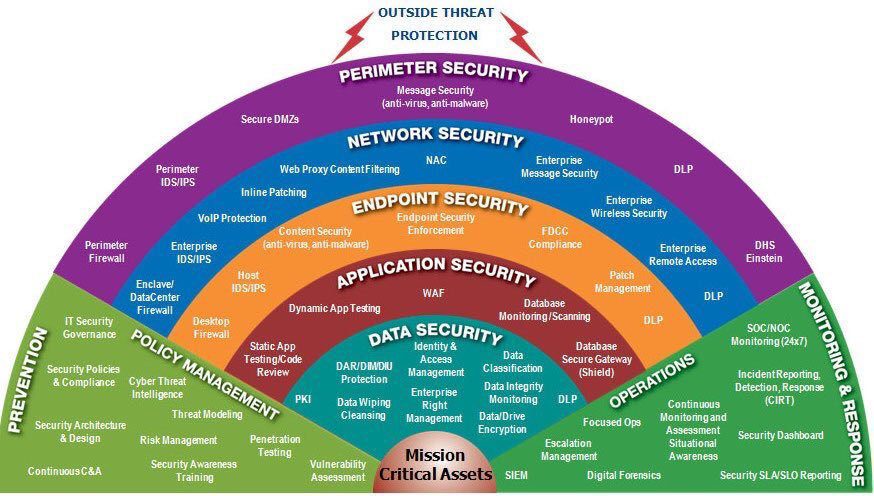
With the rise of cyber-attacks and data breaches, and today’s increasingly mobile workforce, securely managing data and endpoints without inhibiting employee productivity has become critical to organizations including military. Many devices including smart phones, tablets and laptops now have network access capabilities however these devices also provide an entry point for threats. These devices can expose organizations to a vast array of security threats and make the issue of corporate IT security a whole lot more complex.
IDST Pro Access Required
This analysis is part of IDST premium intelligence.
Subscribe to Continue ReadingAlready a member? Log in